- Главная
- Разное
- Дизайн
- Бизнес и предпринимательство
- Аналитика
- Образование
- Развлечения
- Красота и здоровье
- Финансы
- Государство
- Путешествия
- Спорт
- Недвижимость
- Армия
- Графика
- Культурология
- Еда и кулинария
- Лингвистика
- Английский язык
- Астрономия
- Алгебра
- Биология
- География
- Детские презентации
- Информатика
- История
- Литература
- Маркетинг
- Математика
- Медицина
- Менеджмент
- Музыка
- МХК
- Немецкий язык
- ОБЖ
- Обществознание
- Окружающий мир
- Педагогика
- Русский язык
- Технология
- Физика
- Философия
- Химия
- Шаблоны, картинки для презентаций
- Экология
- Экономика
- Юриспруденция
To Cloud or Not To Cloud ? презентация
Содержание
- 1. To Cloud or Not To Cloud ?
- 4. Myth # 1 - Cloud is Too New
- 5. Not Quite Coined by Compaq Executive George Favaloro back in 1996
- 6. Myth # 2 - Cloud is Just a Fad
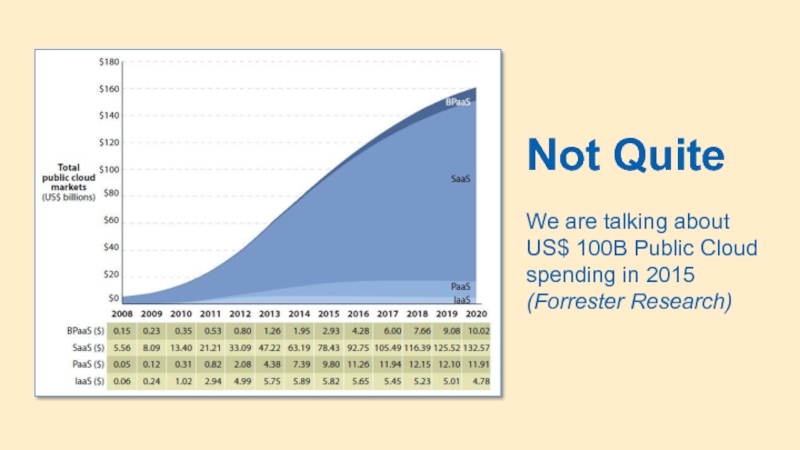
- 7. Not Quite We are talking about
- 8. Myth # 3 - Cloud is Costly
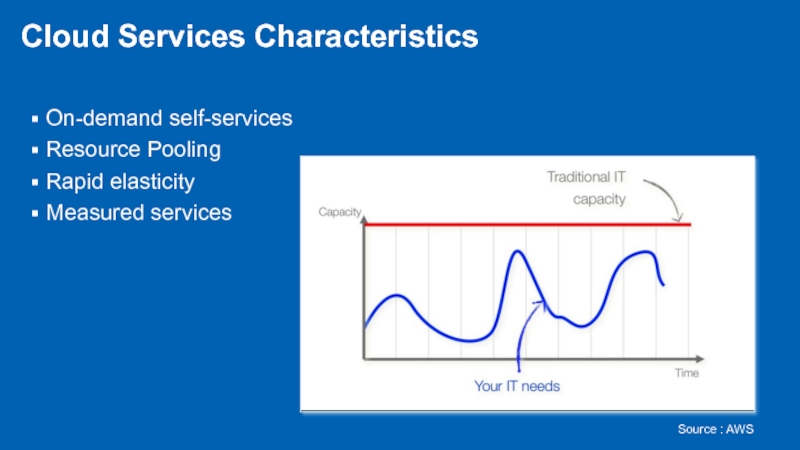
- 9. Cloud Services Characteristics On-demand self-services Resource Pooling Rapid elasticity Measured services Source : AWS
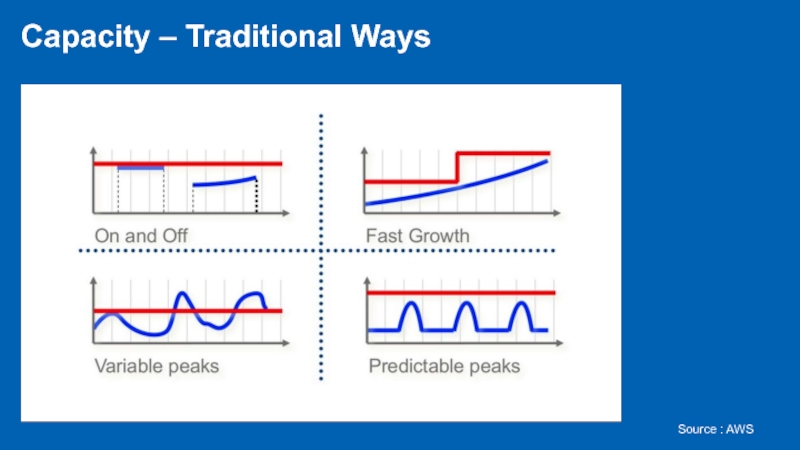
- 10. Capacity – Traditional Ways Source : AWS
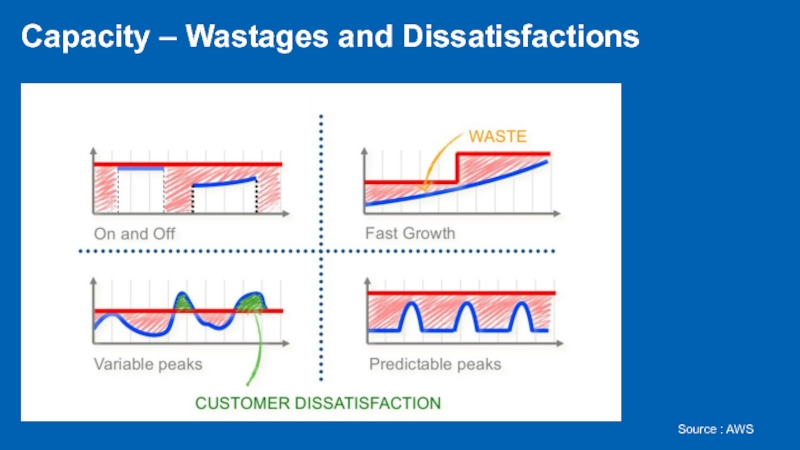
- 11. Capacity – Wastages and Dissatisfactions Source : AWS
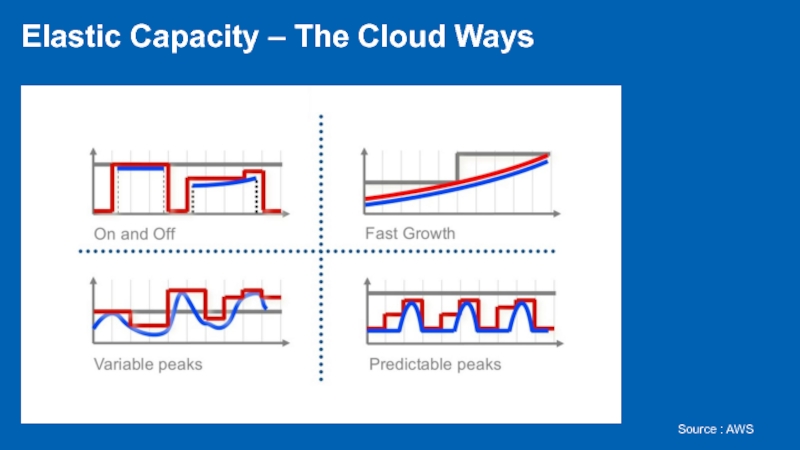
- 12. Elastic Capacity – The Cloud Ways Source : AWS
- 13. Myth # 4 - Cloud is Not Secure
- 14. Insecure ? Truth is that data and
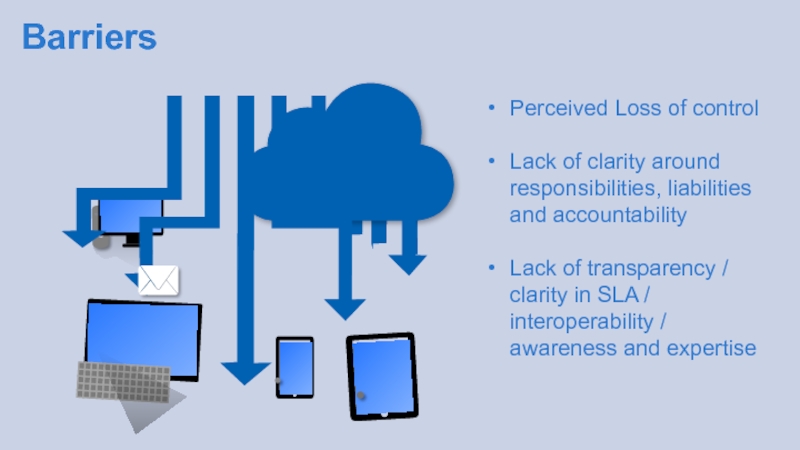
- 15. Barriers Perceived Loss of control
- 16. Cloud … is not New is not
- 17. To Jump or Not to Jump ?
- 18. Next Step ? Proper Risk Assessment
- 19. Risks and Security Concerns Vendor Lock In
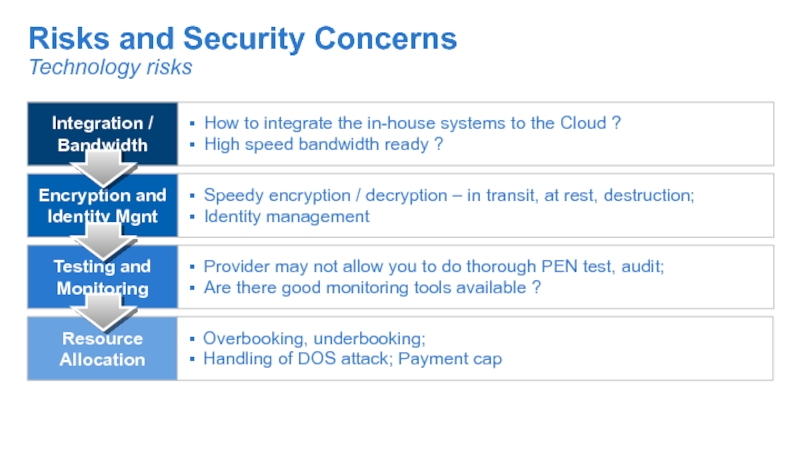
- 20. Risks and Security Concerns Integration / Bandwidth
- 21. Questions To Ask … When and where
- 22. Bear In Mind … Even though you
- 23. ISO 27001, 27002, 27017, 27018, 29100
- 24. Standards Development / Setting Organizations (SDO /
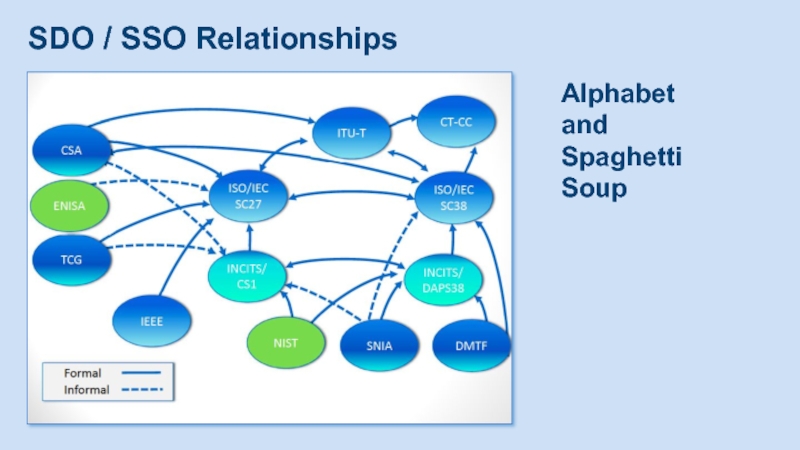
- 25. SDO / SSO Relationships Alphabet and Spaghetti Soup
- 26. Any Pointers ?
- 27. Do Our Homework … Self Assessment
- 28. Get Help from Professionals Companies and individuals
- 29. Take Away Messages Credit : Ching Yiu
- 30. Take Away Messages Cloud is real and
- 31. To Cloud or Not To Cloud ? mail@michaelyung.com
- 32. Thank You !!
Слайд 9Cloud Services Characteristics
On-demand self-services
Resource Pooling
Rapid elasticity
Measured services
Source : AWS
Слайд 14Insecure ?
Truth is that data and systems residing in public or
Typically, cloud-based systems can be more secure than existing internal systems if you do the upfront work required
Слайд 15Barriers
Perceived Loss of control
Lack of clarity around responsibilities, liabilities and
Lack of transparency / clarity in SLA / interoperability / awareness and expertise
Слайд 19Risks and Security Concerns
Vendor Lock In
Poor SLA
3rd Party access to Data
Poor
Few tools, procedures or standard formats available for data and service portability
Service level affects confidentiality and availability
The needs to protect the intellectual property, trade secrets, personal data; complied to regulations / laws in different geographical regions
Business continuity and disaster recovery plans must be well documented and tested
Service and contractual risks
Слайд 20Risks and Security Concerns
Integration / Bandwidth
Encryption and Identity Mgnt
Testing and Monitoring
Resource
How to integrate the in-house systems to the Cloud ?
High speed bandwidth ready ?
Speedy encryption / decryption – in transit, at rest, destruction;
Identity management
Provider may not allow you to do thorough PEN test, audit;
Are there good monitoring tools available ?
Overbooking, underbooking;
Handling of DOS attack; Payment cap
Technology risks
Слайд 21Questions To Ask …
When and where to use the cloud –
SLO (and then SLA)
Availability, reliability, accessibility, performance and security
Along with what best practices
People, processes, change management etc.
Along with what technologies, services, vendors
Servers, storage, network, software etc.
Слайд 22Bear In Mind …
Even though you are outsourcing some of your
You are not outsourcing to vendor, the …
Risk,
Accountability and
Compliance obligations
Find the right Cloud Services Provider – qualified, Security Standards compliance
Слайд 23ISO 27001, 27002, 27017, 27018, 29100
SSAE 16, HIPAA, FedRAMP, FISMA. PCI-DSS
Are
Слайд 24Standards Development / Setting Organizations (SDO / SSO)
DMTF = Distributed Management
ENISA = European Network and Information Security Agency
ETSI = European Telecommunications Standards Institute
IEC = International Electrotechnical Commission
IEEE = Institute of Electrical and Electronics Engineers
INCITS = International Committee for Information Technology Standards
ISO = International Organization for Standardization
ITU-T = International Telecommunication Union – Telecom
NIST = National Institute for Standards and Technology
OASIS = Organization for the Advancement of Structured Information Standards
SNIA = Storage Networking Industry Association
TCG = Trusted Computing Group
Alphabet Soup
Слайд 28Get Help from Professionals
Companies and individuals with certifications
An objective measurement of
Committing the effort and resources to obtain certification indicates seriousness of prospective companies and individuals
Слайд 30Take Away Messages
Cloud is real and here to stay
Take ownership and
Review your current set up and the Cloud Services Provider with guidelines
Focus in the SLO and SLA
Ask for expert help from services providers, and professional organizations