- Главная
- Разное
- Дизайн
- Бизнес и предпринимательство
- Аналитика
- Образование
- Развлечения
- Красота и здоровье
- Финансы
- Государство
- Путешествия
- Спорт
- Недвижимость
- Армия
- Графика
- Культурология
- Еда и кулинария
- Лингвистика
- Английский язык
- Астрономия
- Алгебра
- Биология
- География
- Детские презентации
- Информатика
- История
- Литература
- Маркетинг
- Математика
- Медицина
- Менеджмент
- Музыка
- МХК
- Немецкий язык
- ОБЖ
- Обществознание
- Окружающий мир
- Педагогика
- Русский язык
- Технология
- Физика
- Философия
- Химия
- Шаблоны, картинки для презентаций
- Экология
- Экономика
- Юриспруденция
Connectivity NA(P)T 3 Thomson Gateway NAT > NAT: Network Address Translation ("IP Masquerading") > NAPT: Network Address and Port Translation. презентация
Содержание
- 2. Connectivity NA(P)T
- 3. Thomson Gateway NAT NAT: Network Address Translation ("IP Masquerading") NAPT: Network Address and Port Translation
- 4. Definition NAT: Maps IP addresses from one
- 5. Necessity IPv4: 32 bits Private networks 10.0.0.0,
- 6. Example [IN] eth0-> :
- 7. Static vs. Dynamic NAT Static Address Assignment
- 8. Basic NAT Block external addresses set aside
- 9. When to Use Basic NAT Inside address
- 10. NAPT Extension: translation of transport identifiers TCP,
- 11. NAPT – Continued NAPT uses ports from
- 12. When to Use NAPT Multiple private hosts
- 13. Two-Way NAT Sessions can be initiated from
- 14. Connection Sharing HyperNAT – IP Passthrough Allow
- 15. Connection Sharing HyperNAT – IP Passthrough “Default Server” Service/Portmaps
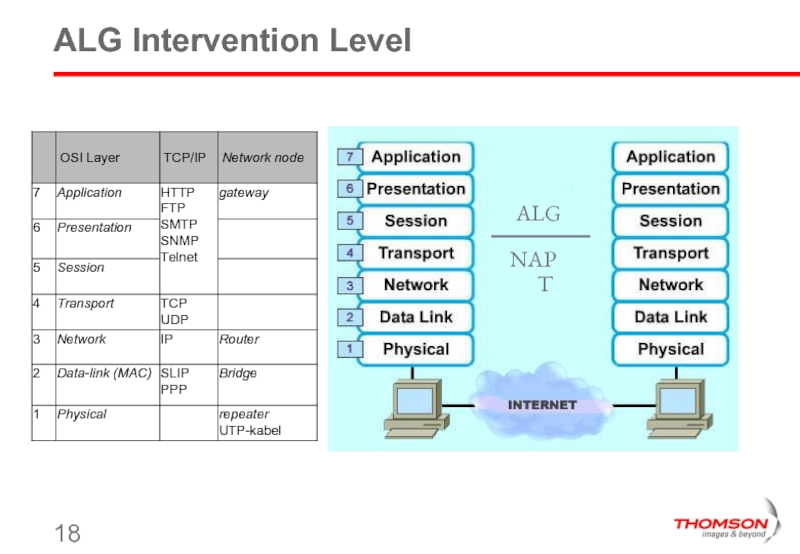
- 16. Connectivity – NAT ALGs
- 17. Definition ALG = Application Level Gateway Translates
- 18. ALG Intervention Level NAPT ALG
- 19. ALGs Real Actions Create connection Delete connection
- 20. Supported ALGs IP6to4 PPTP (VPN) ESP (IPSec)
- 21. ALGs Triggering Each ALG is bound to
- 22. FTP ALG No firewall opening needed Firewall
- 23. Managed Security Service Firewall
- 24. Managed Security Service Firewall - Overview
- 25. Managed Security Service Firewall - Default Policies Edit Level
- 26. Stateful firewall CLI configuration General configuration :firewall config state Tcpchecks Udpchecks Icmpchecks
- 27. Stateful firewall CLI configuration Firewall menu Chain
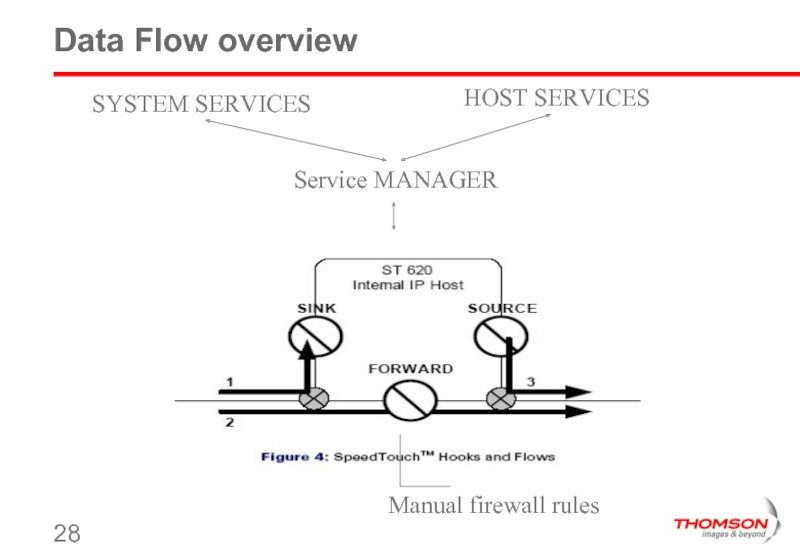
- 28. Data Flow overview Service MANAGER HOST SERVICES SYSTEM SERVICES Manual firewall rules
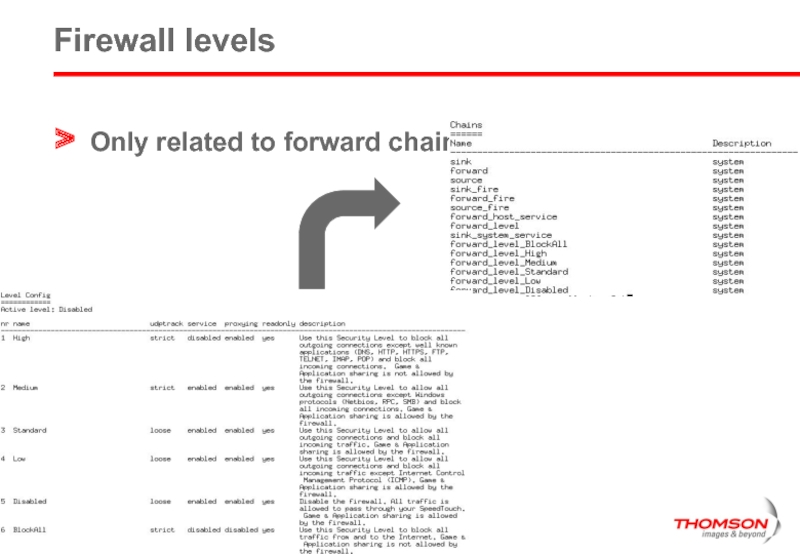
- 29. Firewall levels Only related to forward chain !
- 30. Firewall rules Rules are linked to chains.
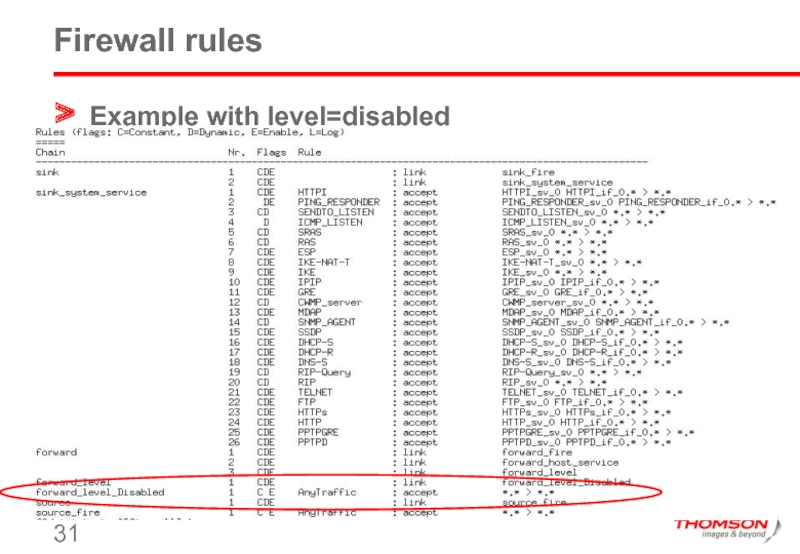
- 31. Firewall rules Example with level=disabled
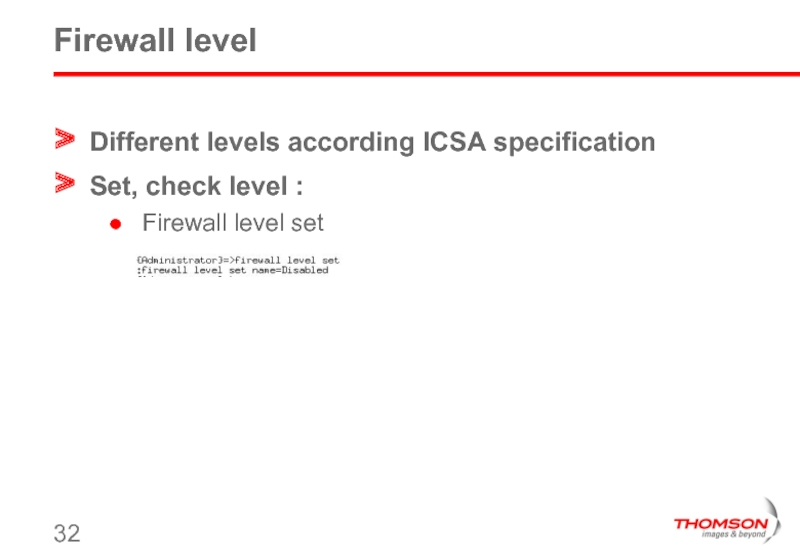
- 32. Firewall level Different levels according ICSA specification Set, check level : Firewall level set
- 33. Hands on - Firewall Create a rule
Слайд 3Thomson Gateway NAT
NAT: Network Address Translation ("IP Masquerading")
NAPT: Network Address and
Слайд 4Definition
NAT:
Maps IP addresses from one address realm to other
Provides transparent routing
Characteristics:
Transparent address assignment
Transparent routing through address translation
ICMP error packet payload translation
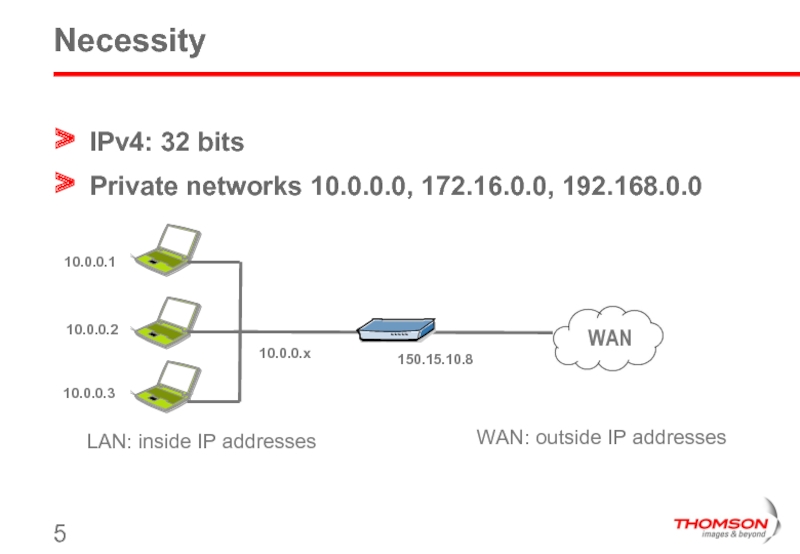
Слайд 5Necessity
IPv4: 32 bits
Private networks 10.0.0.0, 172.16.0.0, 192.168.0.0
LAN: inside IP addresses
WAN: outside
Слайд 6Example
[IN] eth0-> : 40.0.1.1 100.0.1.1
[UT] eth0->pppoe0 : 50.50.1.1 100.0.1.1 0076 TCP 49125->50000 [S.....]
[IN] pppoe0-> : 100.0.1.1 50.50.1.1 0076 TCP 50000->49125 [S.A...]
[UT] pppoe0->eth0 : 100.0.1.1 40.0.1.1 0076 TCP 50000->10000 [S.A...]
[IN] eth0-> : 40.0.1.1 100.0.1.1 0076 TCP 10000->50000 [..A...]
[UT] eth0->pppoe0 : 50.50.1.1 100.0.1.1 0076 TCP 49125->50000 [..A...]
[nat]=>maplist
Idx Type Interface Outside Address Inside Address Use
1 NAPT pppoe0 50.50.1.1 40.0.1.1 1
40.0.1.1
PPPoE Server
100.0.1.1
Packet
flow
Session flow
Address binding
NAPT: extension of NAT
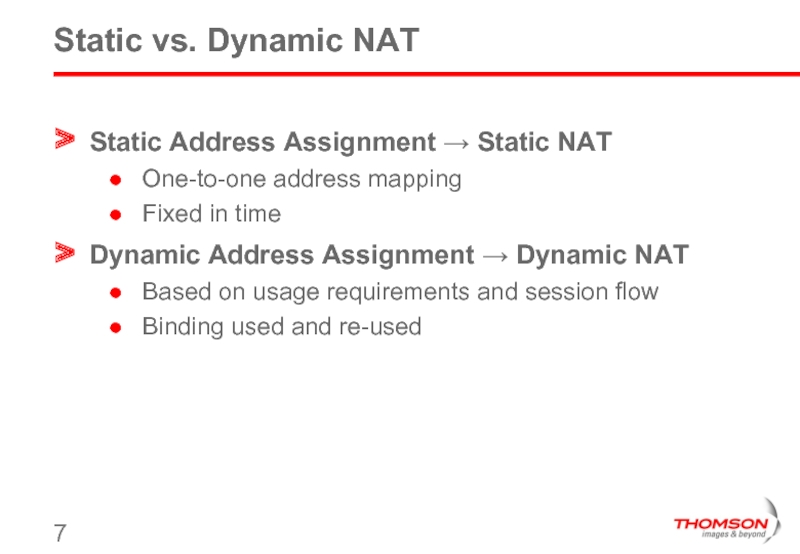
Слайд 7Static vs. Dynamic NAT
Static Address Assignment → Static NAT
One-to-one address mapping
Fixed
Dynamic Address Assignment → Dynamic NAT
Based on usage requirements and session flow
Binding used and re-used
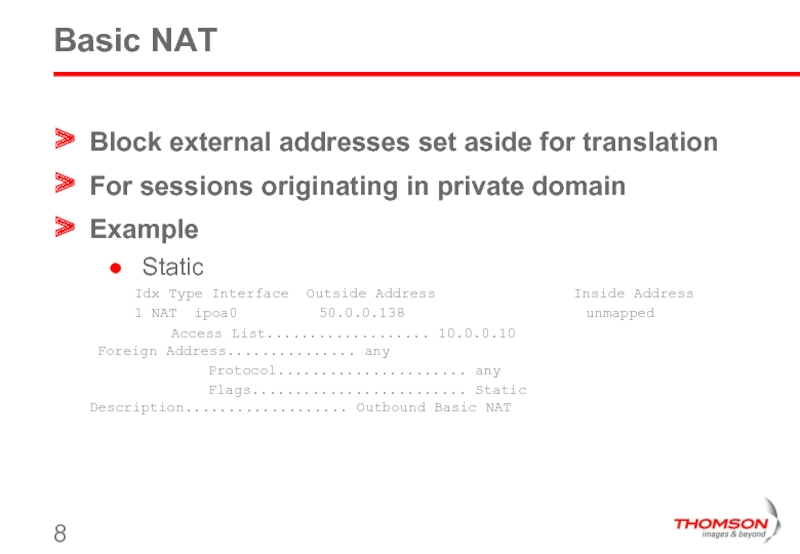
Слайд 8Basic NAT
Block external addresses set aside for translation
For sessions originating in
Example
Static
Idx Type Interface Outside Address Inside Address
1 NAT ipoa0 50.0.0.138 unmapped
Access List................... 10.0.0.10 Foreign Address............... any
Protocol...................... any
Flags......................... Static Description................... Outbound Basic NAT
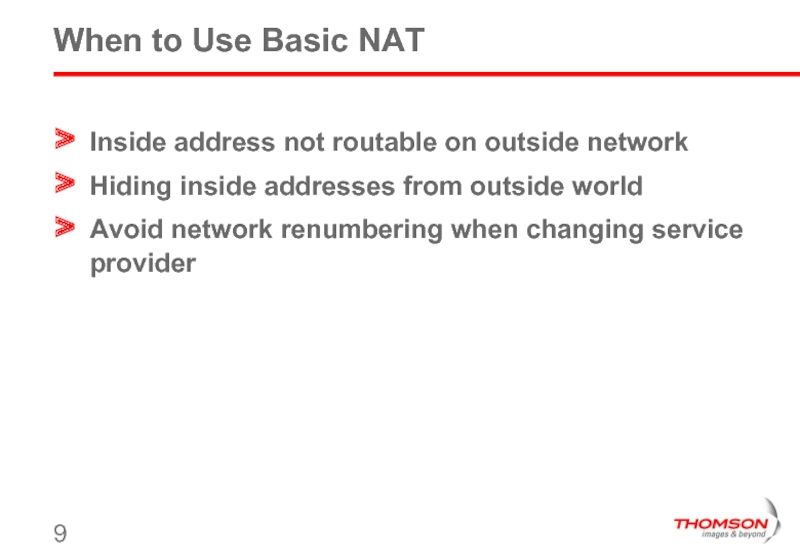
Слайд 9When to Use Basic NAT
Inside address not routable on outside network
Hiding
Avoid network renumbering when changing service provider
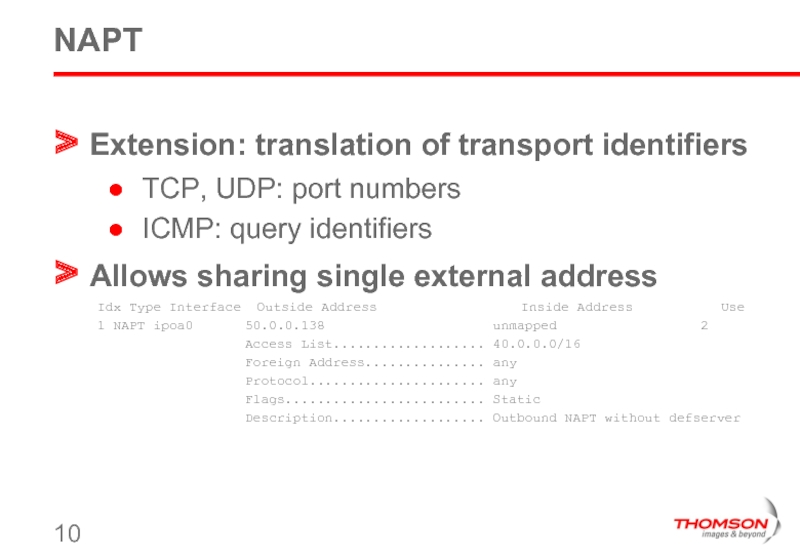
Слайд 10NAPT
Extension: translation of transport identifiers
TCP, UDP: port numbers
ICMP: query identifiers
Allows sharing
Idx Type Interface Outside Address Inside Address Use
1 NAPT ipoa0 50.0.0.138 unmapped 2
Access List................... 40.0.0.0/16
Foreign Address............... any
Protocol...................... any
Flags......................... Static
Description................... Outbound NAPT without defserver
Слайд 11NAPT – Continued
NAPT uses ports from range [49125 - 65536]
[IN] eth0->
[UT] eth0->ipoa0 : 50.0.1.138 100.0.1.1 0076 TCP 49125->50000 [S.....]
[IN] ipoa0-> : 100.0.1.1 50.0.1.138 0076 TCP 50000->49125 [S.A...]
[UT] ipoa0->eth0 : 100.0.1.1 40.0.1.1 0076 TCP 50000->10000 [S.A...]
[IN] eth0-> : 40.0.1.1 100.0.1.1 0076 TCP 10000->50000 [..A...]
[UT] eth0->ipoa0 : 50.0.1.138 100.0.1.1 0076 TCP 49125->50000 [..A...]
[IN] eth0-> : 40.0.1.2 100.0.1.1 0076 TCP 10001->50000 [S.....]
[UT] eth0->ipoa0 : 50.0.1.138 100.0.1.1 0076 TCP 49126->50000 [S.....]
[IN] ipoa0-> : 100.0.1.1 50.0.1.138 0076 TCP 50000->49126 [S.A...]
[UT] ipoa0->eth0 : 100.0.1.1 40.0.1.2 0076 TCP 50000->10001 [S.A...]
[IN] eth0-> : 40.0.1.2 100.0.1.1 0076 TCP 10001->50000 [..A...]
[UT] eth0->ipoa0 : 50.0.1.138 100.0.1.1 0076 TCP 49126->50000 [..A...]
Слайд 12When to Use NAPT
Multiple private hosts accessing public network through same
Link specific traffic to private host
Redirect all unknown incoming traffic to chosen private host
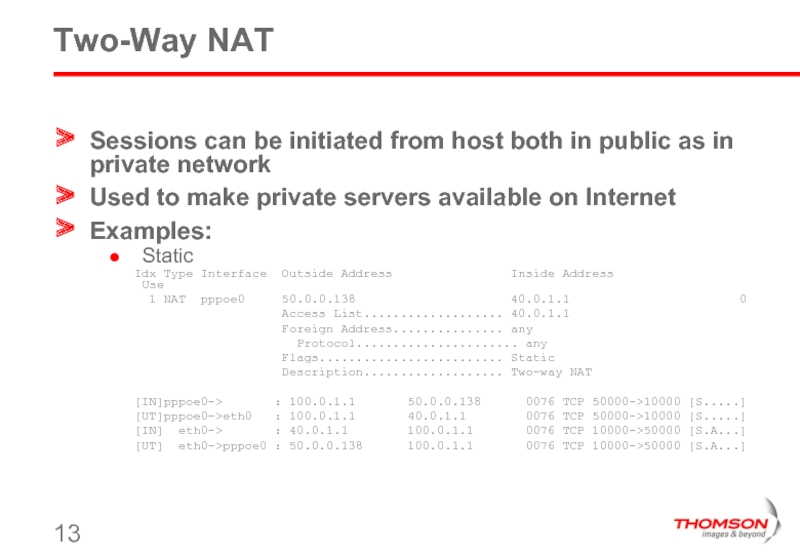
Слайд 13Two-Way NAT
Sessions can be initiated from host both in public as
Used to make private servers available on Internet
Examples:
Static
Idx Type Interface Outside Address Inside Address Use
1 NAT pppoe0 50.0.0.138 40.0.1.1 0
Access List................... 40.0.1.1
Foreign Address............... any
Protocol...................... any
Flags......................... Static
Description................... Two-way NAT
[IN]pppoe0-> : 100.0.1.1 50.0.0.138 0076 TCP 50000->10000 [S.....]
[UT]pppoe0->eth0 : 100.0.1.1 40.0.1.1 0076 TCP 50000->10000 [S.....]
[IN] eth0-> : 40.0.1.1 100.0.1.1 0076 TCP 10000->50000 [S.A...]
[UT] eth0->pppoe0 : 50.0.0.138 100.0.1.1 0076 TCP 10000->50000 [S.A...]
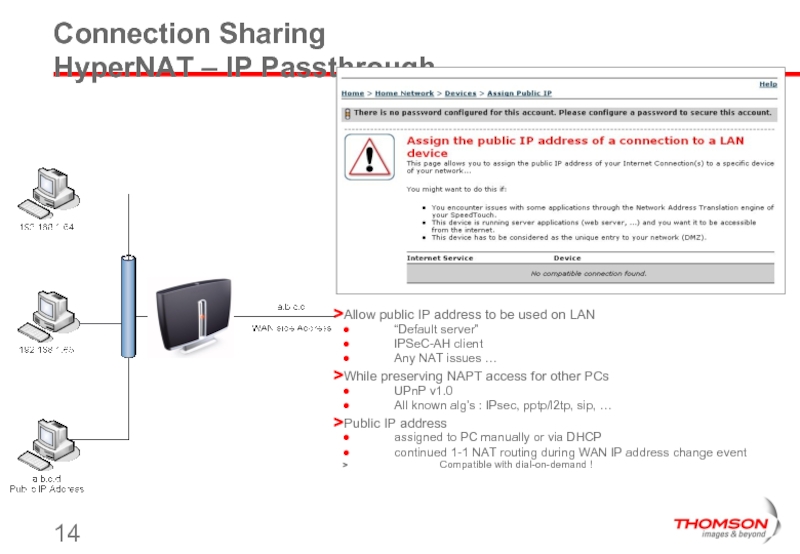
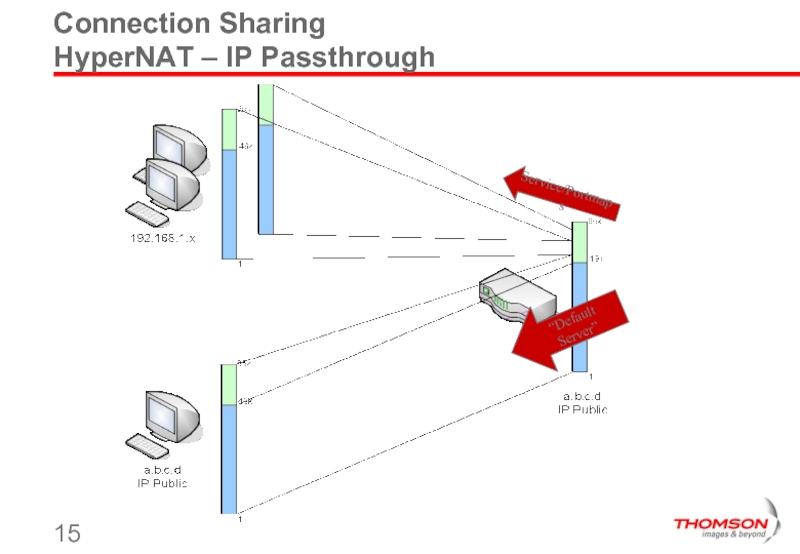
Слайд 14Connection Sharing
HyperNAT – IP Passthrough
Allow public IP address to be used
“Default server”
IPSeC-AH client
Any NAT issues …
While preserving NAPT access for other PCs
UPnP v1.0
All known alg’s : IPsec, pptp/l2tp, sip, …
Public IP address
assigned to PC manually or via DHCP
continued 1-1 NAT routing during WAN IP address change event
Compatible with dial-on-demand !
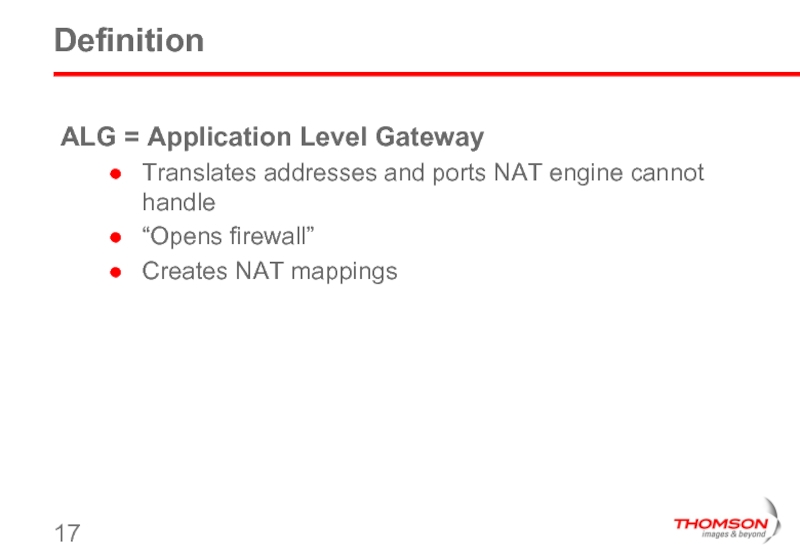
Слайд 17Definition
ALG = Application Level Gateway
Translates addresses and ports NAT engine cannot
“Opens firewall”
Creates NAT mappings
Слайд 19ALGs Real Actions
Create connection
Delete connection
Search connection
Packet modification
Add NAT mapping
Remove NAT mapping
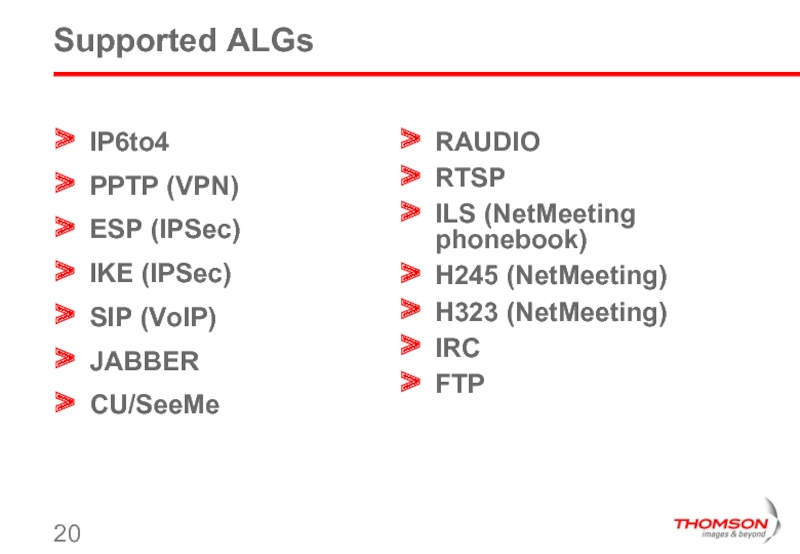
Слайд 20Supported ALGs
IP6to4
PPTP (VPN)
ESP (IPSec)
IKE (IPSec)
SIP (VoIP)
JABBER
CU/SeeMe
RAUDIO
RTSP
ILS (NetMeeting phonebook)
H245 (NetMeeting)
H323 (NetMeeting)
IRC
FTP
Слайд 21ALGs Triggering
Each ALG is bound to (range of) port(s)
{Administrator}[connection]=>applist
Application Proto
IP6TO4 6to4 0 enabled unavailable
PPTP tcp 1723 enabled unavailable
ESP esp 0 unavailable 15' 0"
IKE udp 500 disabled 15' 0"
SIP udp 5060 disabled 6 0"
JABBER tcp 5222 disabled 2' 0"
CU/SeeMe udp 7648 enabled unavailable
RAUDIO(PNA) tcp 7070 enabled unavailable
RTSP tcp 554 enabled unavailable
ILS tcp 389 unavailable 5' 0"
H245 tcp 0 unavailable 5' 0"
H323 tcp 1720 enabled unavailable
IRC tcp 6667 enabled 5' 0"
LOOSE(UDP) udp 0 enabled 5' 0"
FTP tcp 21 enabled unavailable
Available ALGs:
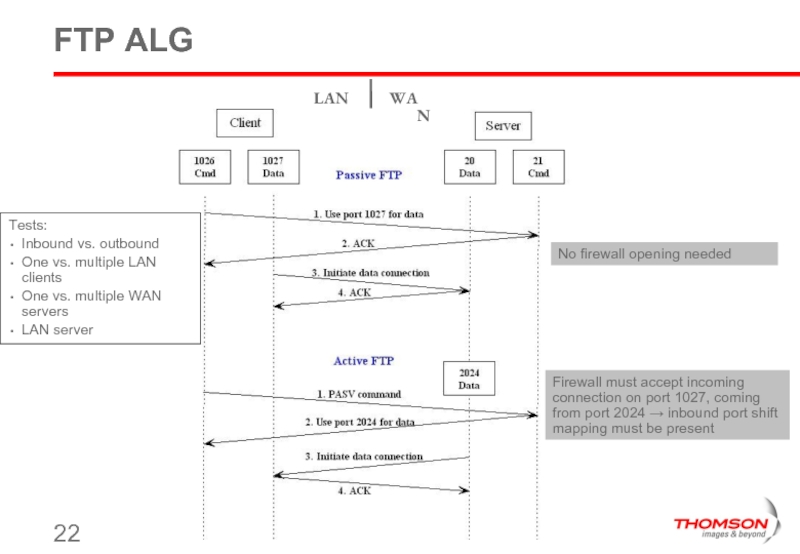
Слайд 22FTP ALG
No firewall opening needed
Firewall must accept incoming connection on port
LAN
WAN
Tests:
Inbound vs. outbound
One vs. multiple LAN clients
One vs. multiple WAN servers
LAN server
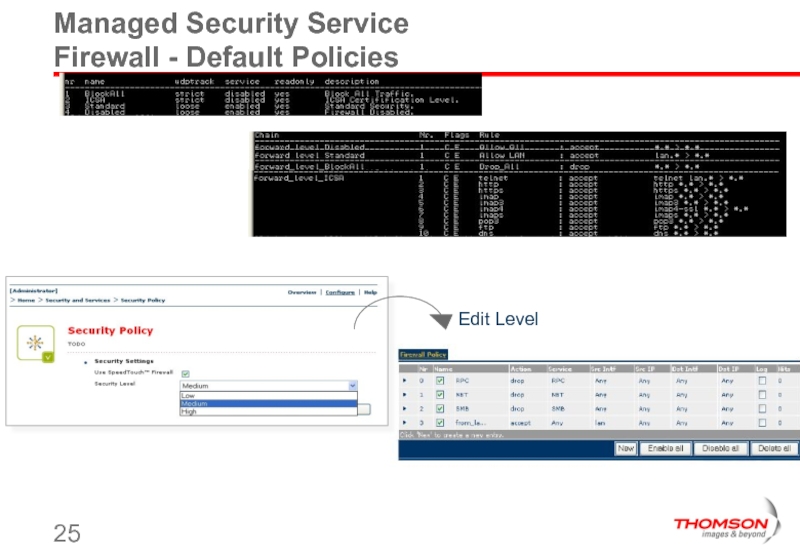
Слайд 24Managed Security Service
Firewall - Overview
Firewall has 2 functions
Protect ST Gateway
Police traffic LAN to WAN and vice versa
Mapped on 2 Fwall services
Firewall (fwd)
GUI/CLI
ServiceManager (sink/src)
CLI
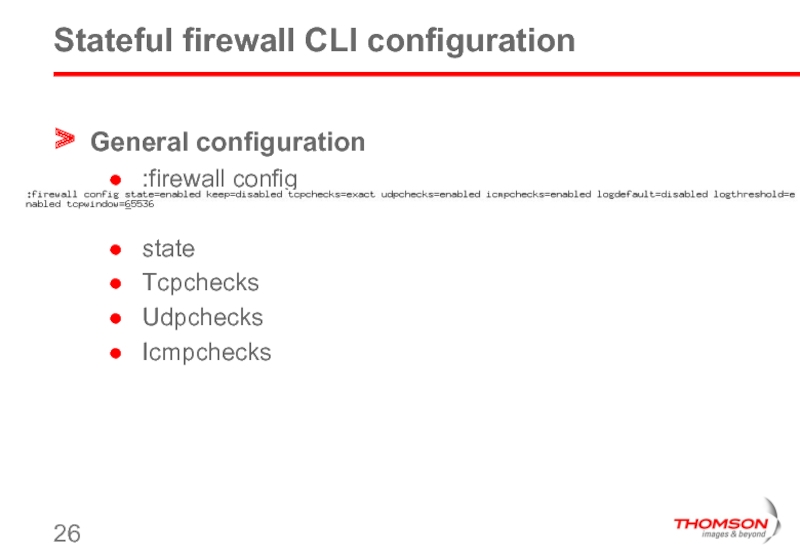
Слайд 26Stateful firewall CLI configuration
General configuration
:firewall config
state
Tcpchecks
Udpchecks
Icmpchecks
Слайд 27Stateful firewall CLI configuration
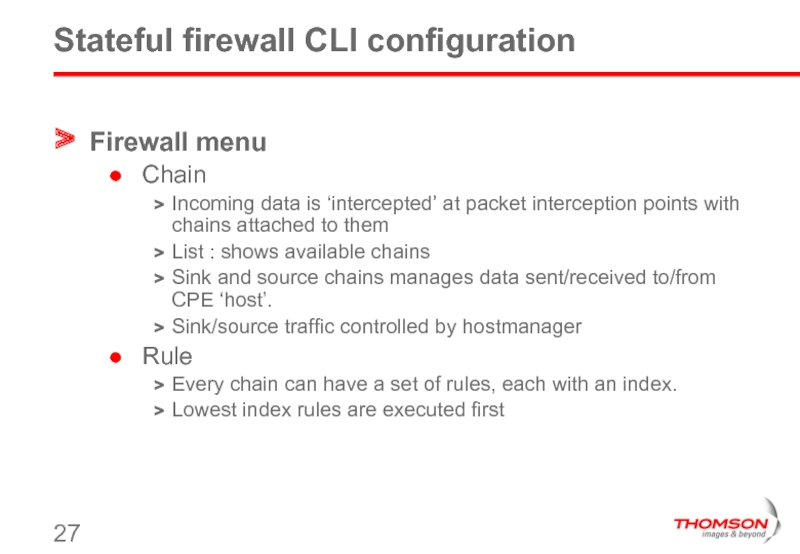
Firewall menu
Chain
Incoming data is ‘intercepted’ at packet interception
List : shows available chains
Sink and source chains manages data sent/received to/from CPE ‘host’.
Sink/source traffic controlled by hostmanager
Rule
Every chain can have a set of rules, each with an index.
Lowest index rules are executed first
Слайд 30Firewall rules
Rules are linked to chains.
Main actions : drop, accept, deny,
Classification criteria
Source and destination interface
Source and destination IP
Service :
Services from the :expr menu
Manual expressions can be created
Classifiers :
Tos, precedence, proto, dscp
Source/destination port ranges
Слайд 32Firewall level
Different levels according ICSA specification
Set, check level :
Firewall level set
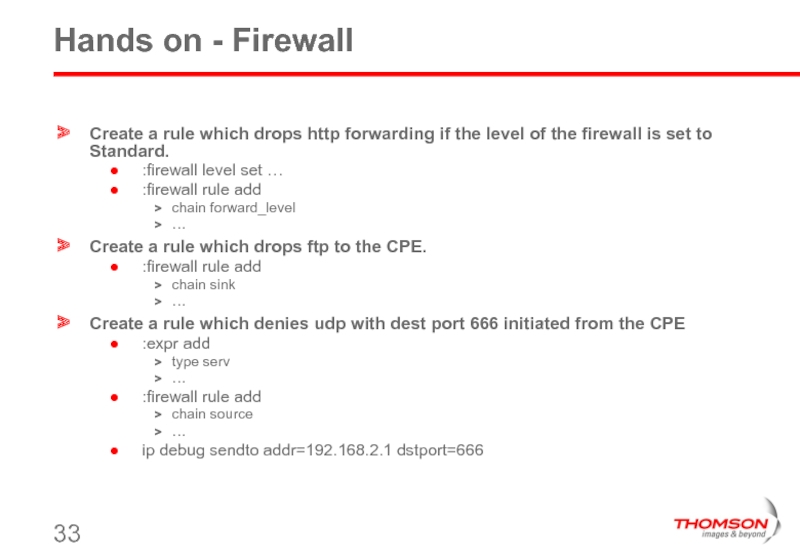
Слайд 33Hands on - Firewall
Create a rule which drops http forwarding if
:firewall level set …
:firewall rule add
chain forward_level
…
Create a rule which drops ftp to the CPE.
:firewall rule add
chain sink
…
Create a rule which denies udp with dest port 666 initiated from the CPE
:expr add
type serv
…
:firewall rule add
chain source
…
ip debug sendto addr=192.168.2.1 dstport=666




![Example[IN] eth0-> : 40.0.1.1 100.0.1.1 0076 TCP 10000->50000 [S.....][UT] eth0->pppoe0 : 50.50.1.1](/img/tmb/1/31483/2e17397ce0ba72f4091b3fd03df32a92-800x.jpg)
![NAPT – ContinuedNAPT uses ports from range [49125 - 65536][IN] eth0-> : 40.0.1.1](/img/tmb/1/31483/4f704fabb6ed9bd17fdc8377376ab145-800x.jpg)



![ALGs TriggeringEach ALG is bound to (range of) port(s){Administrator}[connection]=>applist Application Proto DefaultPort Traces Timeout](/img/tmb/1/31483/2ca4cf048b8c15dccf467604e2adbfa6-800x.jpg)