- Главная
- Разное
- Дизайн
- Бизнес и предпринимательство
- Аналитика
- Образование
- Развлечения
- Красота и здоровье
- Финансы
- Государство
- Путешествия
- Спорт
- Недвижимость
- Армия
- Графика
- Культурология
- Еда и кулинария
- Лингвистика
- Английский язык
- Астрономия
- Алгебра
- Биология
- География
- Детские презентации
- Информатика
- История
- Литература
- Маркетинг
- Математика
- Медицина
- Менеджмент
- Музыка
- МХК
- Немецкий язык
- ОБЖ
- Обществознание
- Окружающий мир
- Педагогика
- Русский язык
- Технология
- Физика
- Философия
- Химия
- Шаблоны, картинки для презентаций
- Экология
- Экономика
- Юриспруденция
Data Breach Notification Laws Time for a Pimp Slap презентация
Содержание
- 1. Data Breach Notification Laws Time for a Pimp Slap
- 2. Pimp slap A powerful, backhanded slap to the face
- 3. @stevewerby Favorite color: Cadet blue Hobby: Stalking
- 4. Infosec since ’99 - ran 2 IT
- 5. Today’s menu Incidents I was involved in
- 6. Definitions Exposed Made accessible to unauthorized person
- 7. Getting to know you Received a data
- 8. Example exposures…maybe Data sanitization vendor’s driver sold
- 9. $ Sony - $10s of millions Those I’ve been involved in – 5-6 figures
- 10. 3rd-party forensic analysis - $222,000 Legal consultant
- 11. 2 recent examples TRICARE Stanford Hospital
- 12. Tip of the iceberg Only a tiny fraction of data exposures are disclosed
- 13. In the beginning Enacted in 2002, effective
- 14. Motivation Perception that breaches of electronic data involving personally identifiable information was increasing
- 15. Increase in electronic breaches? Actual increase not
- 16. Rationale Provides necessary information for affected individuals
- 17. Boom goes the dynamite
- 18. Types of harm Death and physical harm
- 19. AYCE notification Death and physical harm Murderers,
- 20. Data breach notification laws Federal laws Health
- 21. Data breach notification laws
- 22. Data breach laws - future Federal laws
- 23. Components Who the law applies to Types
- 24. Who the law applies to Entity ||
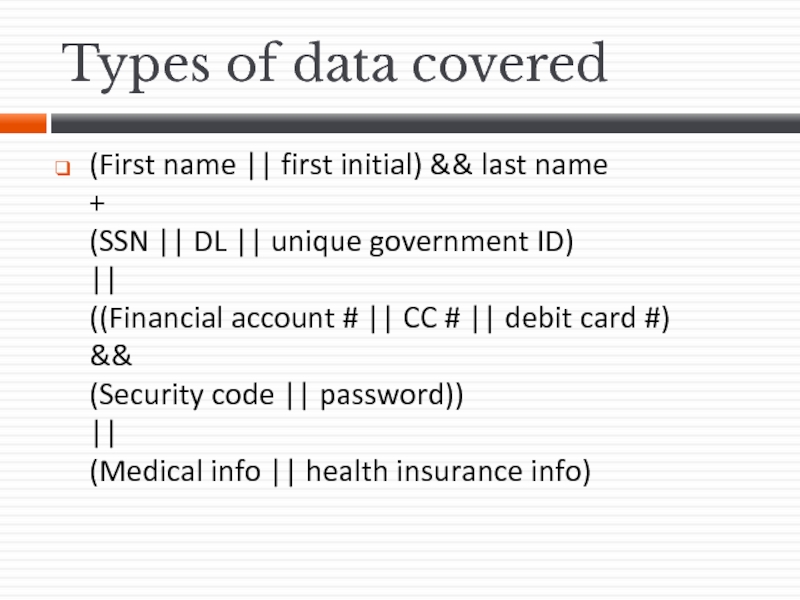
- 25. Types of data covered (First name ||
- 26. State/format of data covered Electronic
- 27. What constitutes a breach Unauthorized access and
- 28. Disclosure obligations - who Notify affected individual
- 29. Disclosure obligations - when Without reasonable delay
- 30. Disclosure obligations - method Written notice Email
- 31. Disclosure obligations - detail General incident overview
- 32. Non-compliance ramifications Attorney general may bring action
- 33. Exceptions Notification not required if affected individuals
- 34. Data breach notification laws
- 35. Issues – scope Not comprehensive enough Mostly
- 36. Issues – ambiguity Reasonable Without reasonable delay
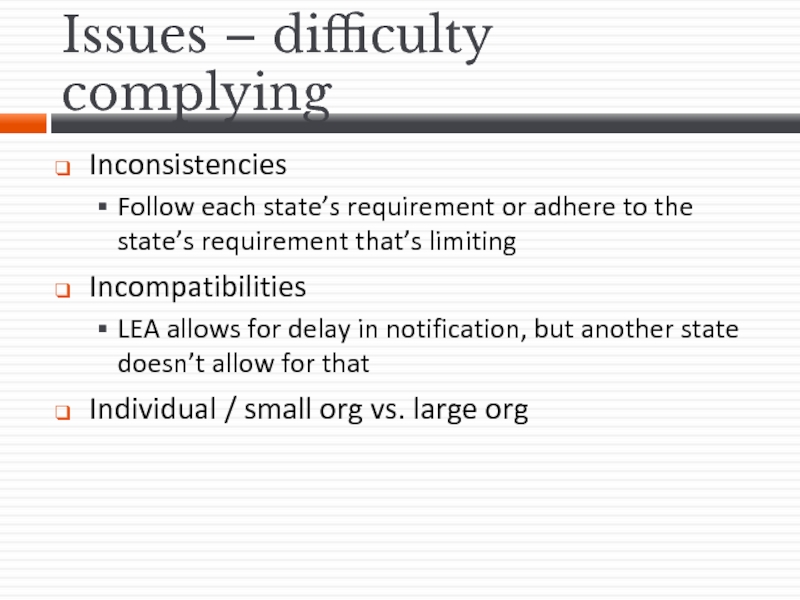
- 37. Issues – difficulty complying Inconsistencies Follow each
- 38. Issues – inequitable treatment Single incident could
- 39. Issues – miscellaneous Ways of identifying a
- 40. Issues – incentives Avoidance $ < notification $ + notification impact $?
- 41. Issues - rationale reality Provides necessary information
- 42. Issues - rationale reality Many incidents are
- 43. Pimp slap
- 44. Alternatives
- 45. Plan 1 Play Angry Birds and just don’t sweat it
- 46. Plan 2 Fine violators $100 billion
- 47. Plan 3 Make all information public
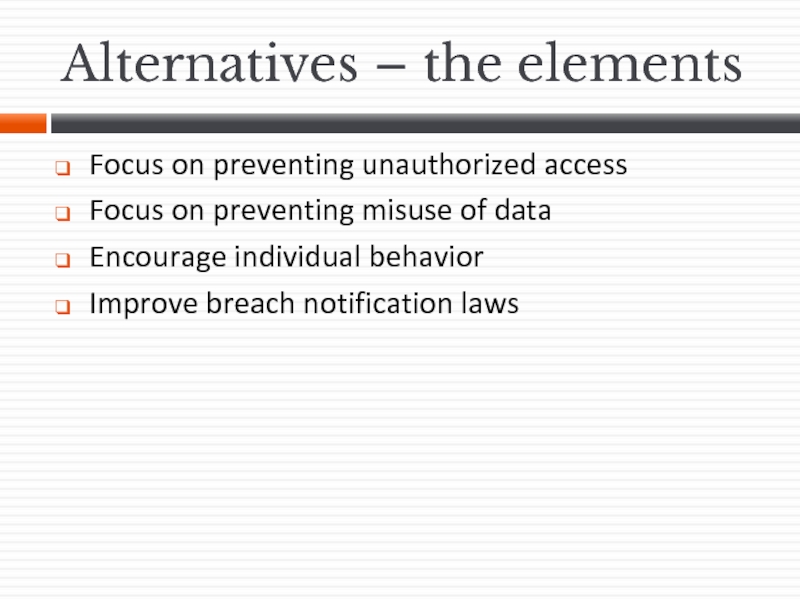
- 48. Alternatives – the elements Focus on preventing
- 49. Prevent unauthorized access Mandate or encourage
- 50. Prevent misuse of data Focus on preventing
- 51. Encourage individual behavior Preventive Use unique passwords
- 52. Improve breach notification laws Increase scope beyond
- 53. Improve breach notification laws Consistent reporting format
- 54. Improve breach notification laws Tiered notification Tier
- 55. Questions and discussion ?
- 56. Contact me @.com @stevewerby 3 blocks from 29.431057° N, 98.490522° W
Слайд 1Data Breach Notification Laws
Time for a Pimp Slap
10/21/2011
Steve Werby
Chief Information
University of Texas at San Antonio
Слайд 3@stevewerby
Favorite color: Cadet blue
Hobby: Stalking divorcees under age 25
Favorite number: 6.0221415
Pet’s name: Cujo
Favorite movie: Santa with Muscles
Last 4 of my SSN: 6497
Place of birth: Delta City
Слайд 4Infosec since ’99 - ran 2 IT consultancies ’99-’04
Analyst at a
Infosec since ’99 - ran 2 IT consultancies ’99-’04
Analyst at a university, CISO at state agency
@stevewerby
Infosec since ’99 - ran 2 IT consultancies ’99-’04
Analyst at a university, CISO at state agency,
CISO at a university
Infosec since ’99 - ran 2 IT consultancies ’99-’04
Analyst at a university, CISO at state agency,
CISO at a university^2
Слайд 5Today’s menu
Incidents I was involved in
Data breach notification laws - what
Issues
Alternatives to achieve desired goal
Слайд 6Definitions
Exposed
Made accessible to unauthorized person
Breached / compromised
Access gained by unauthorized person
Misused
Used
Potential
Possible != actual
Слайд 7Getting to know you
Received a data breach notification?
Been involved in handling
Investigated the incident that led to it?
Participated in decision about whether to notify?
Identified contact information?
Wrote notification content?
Handled notification logistics?
Answered calls from affected individuals?
Caused an incident that led to a notification?
Слайд 8Example exposures…maybe
Data sanitization vendor’s driver sold laptops
Medical provider’s computers stolen
Grade processing
Personal info exposed to unauthorized employees
Web hosting provider’s password DB compromised
Data sanitization vendor’s driver sold laptops
Medical provider’s computers stolen
Grade processing system stolen
Personal info exposed to unauthorized employees
Web hosting provider’s password DB compromised
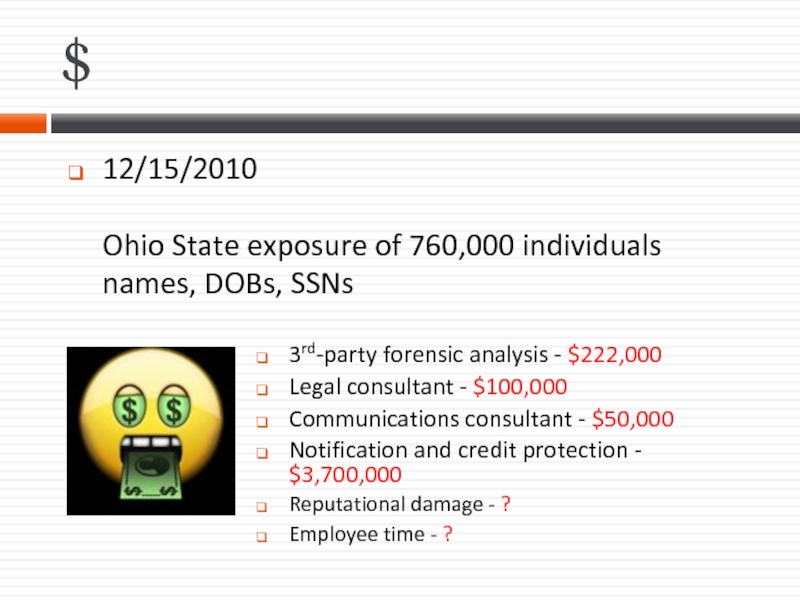
Слайд 103rd-party forensic analysis - $222,000
Legal consultant - $100,000
Communications consultant - $50,000
Notification
Reputational damage - ?
Employee time - ?
$
12/15/2010
Ohio State exposure of 760,000 individuals names, DOBs, SSNs
Слайд 13In the beginning
Enacted in 2002, effective in 2003
Limited to data related
Слайд 14Motivation
Perception that breaches of electronic data involving personally identifiable information was
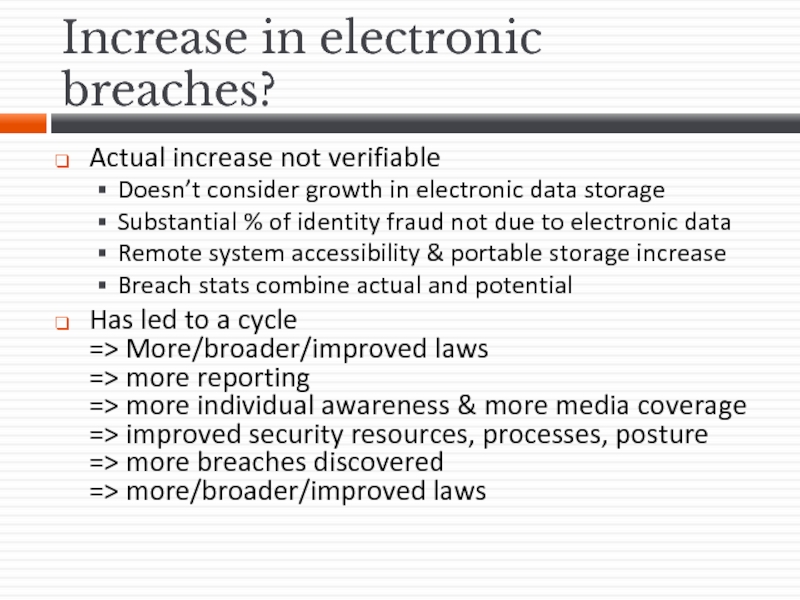
Слайд 15Increase in electronic breaches?
Actual increase not verifiable
Doesn’t consider growth in electronic
Substantial % of identity fraud not due to electronic data
Remote system accessibility & portable storage increase
Breach stats combine actual and potential
Has led to a cycle => More/broader/improved laws => more reporting => more individual awareness & more media coverage => improved security resources, processes, posture => more breaches discovered => more/broader/improved laws
Слайд 16Rationale
Provides necessary information for affected individuals to make informed decisions to
Negative consequences associated with disclosure will result in improved security practices
Слайд 18Types of harm
Death and physical harm
Financial loss
Loss of $, loss of
Credit score damage
Financial identity fraud
Account takeover
Account creation
Social harm
Loss of job, damage to professional opportunities
Relationships, embarrassment
Слайд 19AYCE notification
Death and physical harm
Murderers, violent offenders, mentally unstable
People with contagious
Financial loss
Robbery, burglary, vandalism (robber, burglar, vandal)
Fraud, customer complaints, charlatans
Social harm
Insecure Wi-Fi APs, people who own binoculars
Provides necessary information for at risk individuals to make informed decisions to mitigate impact
Negative consequences associated with disclosure will result in reduction in risk
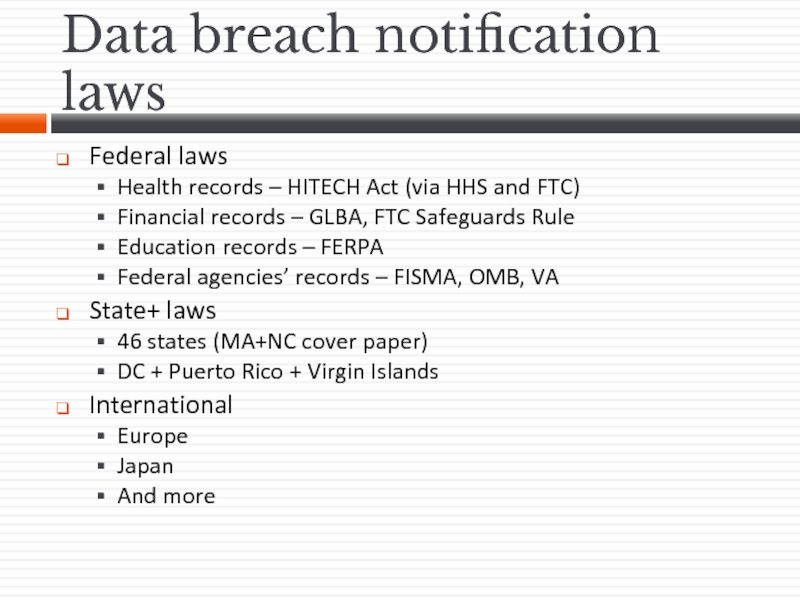
Слайд 20Data breach notification laws
Federal laws
Health records – HITECH Act (via HHS
Financial records – GLBA, FTC Safeguards Rule
Education records – FERPA
Federal agencies’ records – FISMA, OMB, VA
State+ laws
46 states (MA+NC cover paper)
DC + Puerto Rico + Virgin Islands
International
Europe
Japan
And more
Слайд 22Data breach laws - future
Federal laws
Existing laws are in flux
Overarching national
State+ laws
Scope and other details changing
Alabama, Kentucky, New Mexico, South Dakota
Texas healthcare, California beefing theirs up
International
Europe considering expanding beyond telecom
Canada
Taiwan
Слайд 23Components
Who the law applies to
Types of data covered
State/format of data covered
What
Disclosure obligations
Non-compliance ramifications
Exceptions
Слайд 24Who the law applies to
Entity || individual
Conducts biz in state || Maintains data of residents of state || Resulted in or may result in a type of harm to a resident of the state
Слайд 25Types of data covered
(First name || first initial) && last name
+
(SSN
Слайд 26State/format of data covered
Electronic In some cases
Unencrypted || Encrypted, but key breached || Not redacted or altered SSN <5, DL last 4
Слайд 27What constitutes a breach
Unauthorized access and acquisition that compromises
security || confidentiality
Слайд 28Disclosure obligations - who
Notify affected individual
|| the affected owner/licensee
Notify Office of
Notify consumer reporting agencies
Слайд 29Disclosure obligations - when
Without reasonable delay
Sometimes immediately || within specific timeframe
Can
Слайд 30Disclosure obligations - method
Written notice
Email notice if email address is valid
&&
Telephone
Media || email || org’s website if cost > defined threshold || # of recipients > defined threshold || contact info is unreliable or unknown || can’t identify affected individuals
Слайд 31Disclosure obligations - detail
General incident overview
Type of personally identifiable information
Steps that
Contact phone number (if one exists)
Advice to review account information and free credit reports
Слайд 32Non-compliance ramifications
Attorney general may bring action to
Obtain actual damages
Seek civil penalty
Federal agencies can sanction orgs
Mandate controls
Mandate audits
Affected individual can seek to recover direct economic damages
But not $ for the time they put into doing so
Слайд 33Exceptions
Notification not required if affected individuals unlikely to experience fraud as
Some types of organization/sectors excluded
Слайд 35Issues – scope
Not comprehensive enough
Mostly electronic – 30% of reported breaches
What about spoken word…and smoke signals?
Focus almost entirely on financial identity fraud
Excessive notification
Only 3% of those notified of a breach experience identity fraud as a result
Leads to ignoring, considering all the same, failure to take action
Слайд 36Issues – ambiguity
Reasonable
Without reasonable delay
Likely
May result in harm
Likely to result in
Validity of contact information
Must other states’ laws be adhered to?
Слайд 37Issues – difficulty complying
Inconsistencies
Follow each state’s requirement or adhere to the
Incompatibilities
LEA allows for delay in notification, but another state doesn’t allow for that
Individual / small org vs. large org
Слайд 38Issues – inequitable treatment
Single incident could result in
Notification not required for
Some individuals provided different information
Some individuals less likely to receive notification
Слайд 39Issues – miscellaneous
Ways of identifying a person are myopic
Username, email address,
Don’t always know residency of individual
Residency information not collected
Residency information could be stale
Phone # portability
Слайд 41Issues - rationale reality
Provides necessary information for affected individuals to make
Information overload – useless information
Many actions should be taken regularly anyway
Account review, credit report review
Some actions can’t be taken
Can’t get issued new SSN or stop doing biz with gov
Risk is overblown – impact likelihood / liability
Слайд 42Issues - rationale reality
Many incidents are people failures
Affected individuals’ memories are
Orgs’ efforts like Iridium-192
Orgs’ efforts sub-optimized
Proof’s in the pudding
Negative consequences associated with disclosure will result in improved security practices
Слайд 48Alternatives – the elements
Focus on preventing unauthorized access
Focus on preventing misuse
Encourage individual behavior
Improve breach notification laws
Слайд 49Prevent unauthorized access
Mandate or encourage
Limiting access to unauthorized personnel
Limiting use
Protection and transmission of data
Risk management
Educate authorized personnel
Increase personnel’s accountability
Слайд 50Prevent misuse of data
Focus on preventing misuse of data
Make it more
Make it more difficult to create financial accounts
Make it more difficult to access any accounts
Increase penalties for data theft and misuse
Слайд 51Encourage individual behavior
Preventive
Use unique passwords everywhere
Use unique usernames (I don’t eat
Protect your email account – keys to the kingdom
Protect the personal information you control
Detective
Check financial accounts routinely
Check credit reports routinely
Слайд 52Improve breach notification laws
Increase scope beyond financial fraud risk
Oh, Canada!
And include
Increase consistency in state laws
Risk-based approach
Likelihood of access, likelihood of misuse, potential impact, org’s ability to mitigate, compensating controls, affected individual’s ability to mitigate
Compliance status – infosec program, risk-based approach
Sanction status
Leave up to org? Or scoring system
Слайд 53Improve breach notification laws
Consistent reporting format
Increase information that’s shared
Reduce PR speak
Clearly
Clearly describe recommended actions
Слайд 54Improve breach notification laws
Tiered notification
Tier 1 – track internally, make available
Tier 2 – notify national authority and internal personnel
Tier 3 – notify affected individuals
Notification methods
To affected individual – base on org’s size
National database – public and private views