- Главная
- Разное
- Дизайн
- Бизнес и предпринимательство
- Аналитика
- Образование
- Развлечения
- Красота и здоровье
- Финансы
- Государство
- Путешествия
- Спорт
- Недвижимость
- Армия
- Графика
- Культурология
- Еда и кулинария
- Лингвистика
- Английский язык
- Астрономия
- Алгебра
- Биология
- География
- Детские презентации
- Информатика
- История
- Литература
- Маркетинг
- Математика
- Медицина
- Менеджмент
- Музыка
- МХК
- Немецкий язык
- ОБЖ
- Обществознание
- Окружающий мир
- Педагогика
- Русский язык
- Технология
- Физика
- Философия
- Химия
- Шаблоны, картинки для презентаций
- Экология
- Экономика
- Юриспруденция
So You Want to be a Hacker? презентация
Содержание
- 1. So You Want to be a Hacker?
- 2. A BRIEF INTRODUCTION GOTTA START SOMEWHERE
- 3. Introduction The necessary prerequisites Immersing
- 4. DOWN IN FRONT Who Am I? Christopher
- 5. I currently have my dream job I’ve
- 6. 3 teams at SkyDogCon Duplicity CTF, got
- 7. We work in the coolest industry. Period.
- 8. Lots of debate around the term
- 9. THREE CHEERS FOR THE MEDIA What a Hacker Certainly Isn’t
- 10. THE APPROACH COMFORT ZONES TO THE WIND
- 11. Patience Enthusiasm Perseverance Interest
- 12. You will get frustrated. You
- 13. Becoming a “hacker” is not so much
- 14. THE ENVIRONMENT IN OVER Y(OUR) HEAD
- 15. Expertise requires a lot of technical knowledge.
- 16. Powerful message board Lots of infosec boards
- 17. Hang out on Freenode to talk through
- 18. Good way to keep track of the
- 19. Ghost in the Wires The Art of
- 20. Sneakers http://www.imdb.com/title/tt0105435/ Hackers http://www.imdb.com/title/tt0113243/ War
- 21. DEF CON https://www.defcon.org/ Black Hat https://www.blackhat.com/
- 22. Some of the venues listed previously are
- 23. LESSONS TO BE LEARNED STRAIGHT EDUMACATED
- 24. The hardest part is having the gumption
- 25. Incredibly-thorough course on Computer Science https://www.edx.org/course/harvardx/harvardx-cs50x-introduction-computer-1022
- 26. Fundamental understanding of networking is important
- 27. The ability to write code greatly helps
- 28. OpenSecurityTraining can be found online http://opensecuritytraining.info/ “Is
- 29. SecurityTube can be found online http://www.securitytube.net/ Large
- 30. Corelan can be found online https://www.corelan.be/ In-depth
- 31. Offensive Security can be found online http://www.offensive-security.com/
- 32. Has a number of certifications for security
- 33. Cisco has a number of certifications in
- 34. GO TO WORK GETTING YOUR HANDS NOT-SO-DIRTY
- 35. VulnHub can be found online: http://vulnhub.com/ A
- 36. Web application that is built specifically to
- 37. CTF365 can be found online: http://ctf365.com/ Touts
- 38. We Chall can be found online: https://www.wechall.net/
- 39. Managed service provider that consolidates bug bounty
- 40. TOOLS OF THE TRADE AN AWFULLY FULL BAG OF TRICKS
- 41. Used for monitoring local network traffic
- 42. An HTTP proxy with lots of hacky
- 43. Packaged in with all modern browsers
- 44. Good tool for generating password lists
- 45. Where LavaPasswordFactory generates password lists, John the
- 46. The de facto standard penetration testing Linux
- 47. Great platform for virtualization If you
- 48. MAKING IT COUNT WHAT NEXT?
- 49. Penetration testing Security analyst Security
- 50. Doing this stuff maliciously is a bad
- 51. REFERENCES A CENTRALIZED STORY
- 52. The Electronic Frontier Foundation on the Computer
- 53. VulnHub – Vulnerable by Design http://vulnhub.com/ CTF365
- 54. Atlanta OWASP https://www.owasp.org/index.php/Atlanta_Georgia Security Mailing Lists http://seclists.org/
- 55. War Games movie on IMDB http://www.imdb.com/title/tt0086567/ Hacking
- 56. Shmoocon http://www.shmoocon.org/ Harvard Introduction to Computer Science
- 57. OpenSecurityTraining http://opensecuritytraining.info/ Security Tube http://www.securitytube.net/ Corelan.be http://corelan.be/ Offensive Security http://www.offensive-security.com/ TAKE SIX References
- 58. SANS Security Training http://www.sans.org/ Cisco Security Training
- 59. Wireshark https://www.wireshark.org/ Burp Suite http://portswigger.net/burp/ Reddit http://www.reddit.com/ Freenode IRC http://freenode.net/ TAKE EIGHT References
- 60. QUESTIONS? HOPEFULLY YOU’VE GOT A FEW
- 61. THANK YOU @_LAVALAMP
Слайд 3Introduction
The necessary prerequisites
Immersing yourself
Educating yourself
Places to practice responsibly
Common tools
Making it count
THE
The Talk’s Agenda
Слайд 4DOWN IN FRONT
Who Am I?
Christopher Grayson
cgrayson@bishopfox.com
@_lavalamp
Senior Security Analyst at Bishop Fox
MSCS, BSCM from GT
Former Research Scientist from GT
Former president, GT hacking club
Слайд 5I currently have my dream job
I’ve never had to choose between
I had the good fortune of attending SkyDogCon in 2012
But the story continues…
LITTLE BIT OF LUCK, LITTLE BIT OF SKILL
Why am I Here Today?
Слайд 63 teams at SkyDogCon Duplicity CTF, got 2nd, 3rd and 4th
…out of 4 teams
Received tickets to Shmoocon 2013, Offensive Security training
Competed in TOOOL Master Keying competition
Received ticket to Shmoocon 2014
THE PLOT THICKENS…
Many Reasons
Слайд 7We work in the coolest industry. Period.
We need more talented individuals.
We
HOPEFULLY NOT BY ACCIDENT
Why are YOU Here?
Слайд 8Lots of debate around the term
Commonly used by the media to
Used in the community to show reverence towards another’s capabilities
NOT TO START A DEBATE…
The Term “Hacker”
Слайд 12
You will get frustrated.
You will not learn everything overnight.
You will get
NOTHING WORTH DOING WAS EVER EASY
Be Wary…
Слайд 13Becoming a “hacker” is not so much a profession as it
It requires mental fortitude and patience above all else.
Expertise comes slowly.
It’s entirely worth the journey.
STILL INTERESTED?
Takeaways
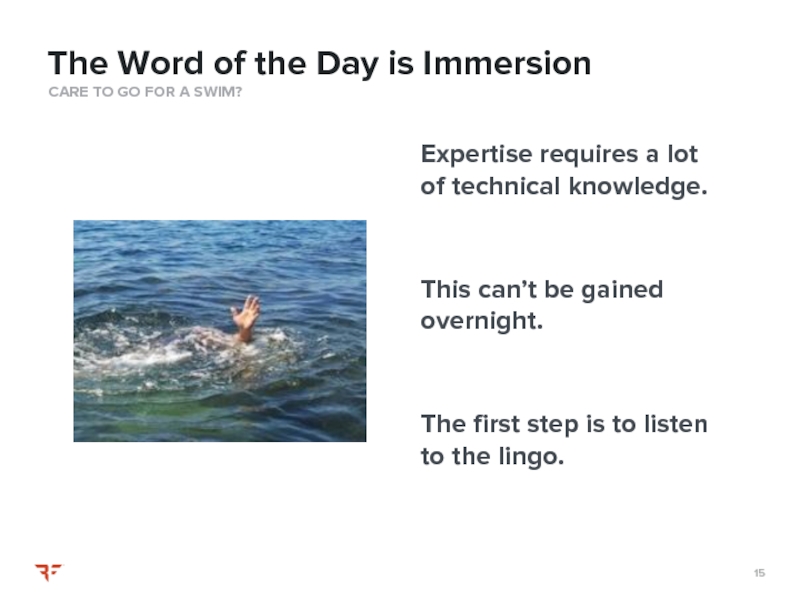
Слайд 15Expertise requires a lot of technical knowledge.
This can’t be gained overnight.
The
CARE TO GO FOR A SWIM?
The Word of the Day is Immersion
Слайд 16Powerful message board
Lots of infosec boards
/r/hacking
/r/netsec
/r/howtohack
/r/websec
/r/sysadmin
/r/blackhat
EVER HEARD OF IT BEFORE?
Reddit
Слайд 17Hang out on Freenode to talk through challenges and difficulties you
#metasploit – Metasploit developers
#corelan – Folks from Corelan team
#vulnhub – Folks from Vulnhub team
#offsec – Folks from Offensive Security
NOT ALL THAT DISSIMILAR TO PIRATE SHIPS
Freenode
Слайд 18Good way to keep track of the industry’s pulse
Lots of mailing
http://seclists.org/
#SPAMSPAMSPAM
Mailing Lists
Слайд 19Ghost in the Wires
The Art of Intrusion
The Art of Deception
Kingpin
The Cuckoo’s
Code
Hacking – The Art of Exploitation
WHAT ARE THOSE AGAIN?
Books
Слайд 20Sneakers
http://www.imdb.com/title/tt0105435/
Hackers
http://www.imdb.com/title/tt0113243/
War Games
http://www.imdb.com/title/tt0086567/
THE GOOD, THE BAD, AND THE UGLY
Movies
Слайд 21DEF CON
https://www.defcon.org/
Black Hat
https://www.blackhat.com/
Shmoocon
http://www.shmoocon.org/
MEET YOUR FELLOW NERDS
Conferences
Слайд 22Some of the venues listed previously are less friendly towards new-comers
General rule of thumb is to research any questions that you have prior to asking them.
Showing that you’ve done your own work before asking for the help of others goes a long way in this community.
ARMOR OF THICK SKIN+3
Disclaimer
Слайд 24The hardest part is having the gumption to stick with it.
Technical
Technical skills are required, and typically the more the better.
PERHAPS, PERHAPS, PERHAPS
So Now we Get Into the Difficult Stuff?
Слайд 25Incredibly-thorough course on Computer Science
https://www.edx.org/course/harvardx/harvardx-cs50x-introduction-computer-1022
LEARN FROM THE BEST OF THEM
Harvard Introduction
Слайд 26Fundamental understanding of networking is important
https://www.coursera.org/course/comnetworks
ONE BYTES TWO BYTES THREE BYTES
Computer Networks on Coursera
Слайд 27The ability to write code greatly helps in this field.
https://www.coursera.org/course/pythonlearn
FROM SCRIPT
Programming for Everybody on Coursera
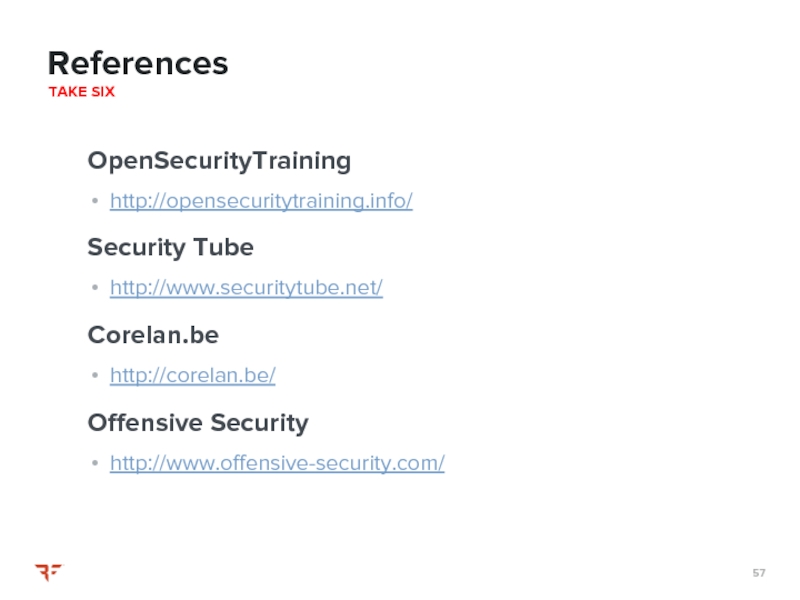
Слайд 28OpenSecurityTraining can be found online
http://opensecuritytraining.info/
“Is dedicated to sharing training material for
Has free, professional courses on all matters hacking
Even has course outlines and pre-requisites!
HARDLY KNOWN BUT HUGELY HELPFUL
OpenSecurityTraining.info
Слайд 29SecurityTube can be found online
http://www.securitytube.net/
Large amounts of free videos created by
Aggregation of conference videos and lectures
Full primers on lots of different hacking areas
AGGREGATE THOSE VIDEOS!
SecurityTube.net
Слайд 30Corelan can be found online
https://www.corelan.be/
In-depth tutorials detailing exploit-writing and binary exploitation
Tons
WRITE YOURSELF SOME EXPLOITS
Corelan.be
Слайд 31Offensive Security can be found online
http://www.offensive-security.com/
The group that created Backtrack and
Training is not free, but the training you get from their courses is top-notch and well-managed.
Has an IRC channel that you can hang out in!
THE AUTHORS OF KALI, BACKTRACK
Offensive Security
Слайд 32Has a number of certifications for security training
Not free, must pay
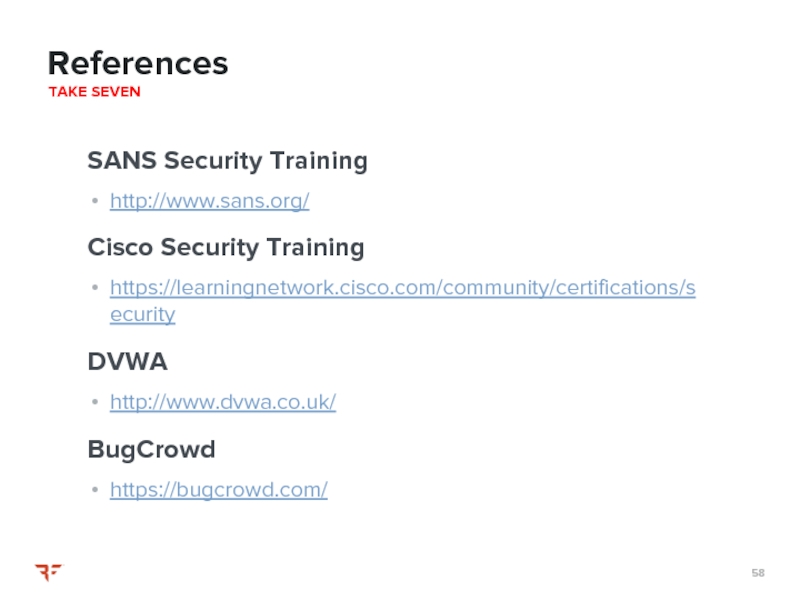
http://www.sans.org/
GETTING CERTIFIED
SANS Institute
Слайд 33Cisco has a number of certifications in the security space.
Not free,
https://learningnetwork.cisco.com/community/certifications/security
MOAR CERTIFICATIONS?!
Cisco Certifications
Слайд 35VulnHub can be found online:
http://vulnhub.com/
A large repository of software images that
Great place to get software packages to hack on
Has an IRC channel you can hang out in!
STAND UP YOUR OWN LAB
Vulnerable Images
Слайд 36Web application that is built specifically to have lots of vulnerabilities
Great
http://www.dvwa.co.uk/
EMPHASIS ON THE D
DVWA
Слайд 37CTF365 can be found online:
http://ctf365.com/
Touts a massive online, persistent CTF
CTFTime can
https://ctftime.org/
Keeps track of CTF competitions worldwide, maintains scores for teams across different CTFs
BRUTAL TRAINING GROUNDS
Ongoing Competitions
Слайд 38We Chall can be found online:
https://www.wechall.net/
Is an aggregation site for individual
Advertises a total of 133 challenges available
SHORT, SWEET, AND TO THE POINT
Stand-Alone Challenges
Слайд 39Managed service provider that consolidates bug bounty programs
Go and hack things
https://bugcrowd.com/
INDUSTRY EXPERIENCE
Bugcrowd
Слайд 41Used for monitoring local network traffic
Great way to learn more about
https://www.wireshark.org/
NETWORKS ARE CHATTIER THAN YOU MAY THINK
Wireshark
Слайд 42An HTTP proxy with lots of hacky bells and whistles
Used universally
http://portswigger.net/burp/
WEB APP HACKER’S SWISS ARMY KNIFE
Burp Suite
Слайд 43Packaged in with all modern browsers
Used mostly by developers for testing
REPURPOSING TOOLS FOR FUN AND PROFIT!
Browser Developer Tools
Слайд 44Good tool for generating password lists
Made by yours truly ☺
https://github.com/lavalamp-/LavaPasswordFactory
A GOOD
LavaPasswordFactory
Слайд 45Where LavaPasswordFactory generates password lists, John the Ripper cracks them!
http://www.openwall.com/john/
CRACK GOES
John the Ripper
Слайд 46The de facto standard penetration testing Linux distribution
Comes with all of
http://www.kali.org/
BELLS AND WHISTLES GALORE
Kali Linux
Слайд 47Great platform for virtualization
If you don’t know what virtualization, check it
http://www.vmware.com/
VIRTUALIZATION IS YOUR FRIEND
VMWare Fusion / Workstation
Слайд 49Penetration testing
Security analyst
Security engineer
All the technical things!
HACKING FOR GOOD
Positions in the
Слайд 50Doing this stuff maliciously is a bad idea
Far too many opportunities
Don’t let it go to waste
WE’VE ALREADY GOT ENOUGH BAD GUYS
Don’t Let it go to Waste
Слайд 52The Electronic Frontier Foundation on the Computer Fraud and Abuse Act
https://ilt.eff.org/index.php/Computer_Fraud_and_Abuse_Act_(CFAA)
Wikipedia
http://en.wikipedia.org/wiki/Aaron_Swartz
H3 at Georgia Tech Research Institute
http://h3.gatech.edu/
The UCSB iCTF
http://ictf.cs.ucsb.edu/
SECCDC
http://www.seccdc.org/
TAKE ONE
References
Слайд 53VulnHub – Vulnerable by Design
http://vulnhub.com/
CTF365
http://ctf365.com/
CTF Time!
https://ctftime.org/
WeChall – A Challenge Aggregation Site
http://www.wechall.net/
TAKE
References
Слайд 54Atlanta OWASP
https://www.owasp.org/index.php/Atlanta_Georgia
Security Mailing Lists
http://seclists.org/
Sneakers movie on IMDB
http://www.imdb.com/title/tt0105435/
Hackers movie on IMDB
http://www.imdb.com/title/tt0113243/
TAKE THREE
References
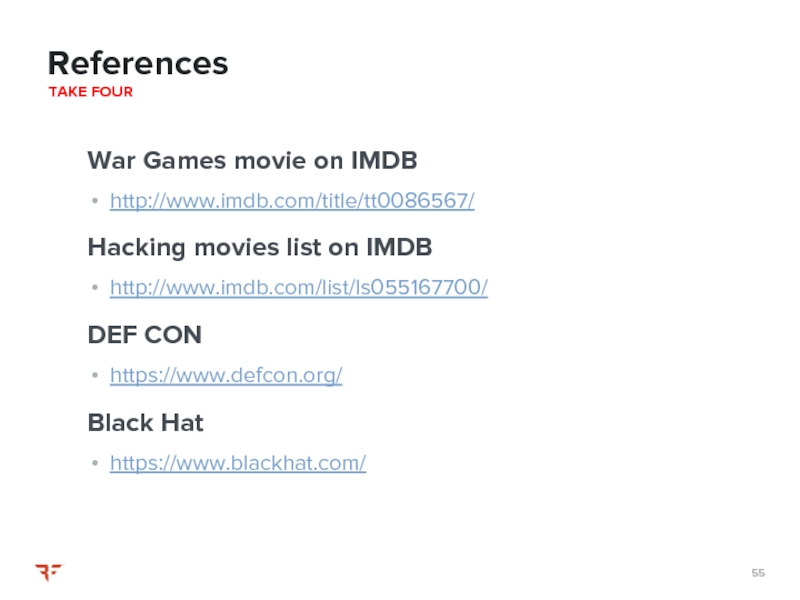
Слайд 55War Games movie on IMDB
http://www.imdb.com/title/tt0086567/
Hacking movies list on IMDB
http://www.imdb.com/list/ls055167700/
DEF CON
https://www.defcon.org/
Black Hat
https://www.blackhat.com/
TAKE
References
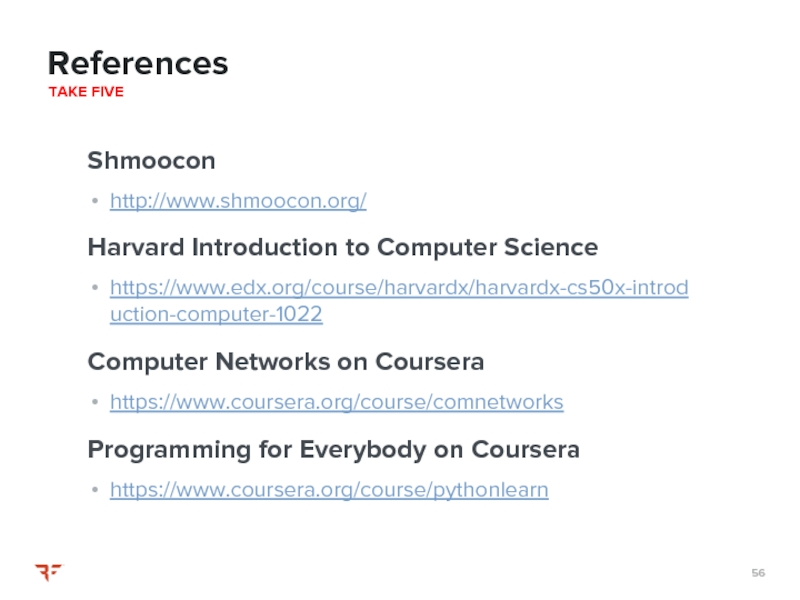
Слайд 56Shmoocon
http://www.shmoocon.org/
Harvard Introduction to Computer Science
https://www.edx.org/course/harvardx/harvardx-cs50x-introduction-computer-1022
Computer Networks on Coursera
https://www.coursera.org/course/comnetworks
Programming for Everybody on
https://www.coursera.org/course/pythonlearn
TAKE FIVE
References