is estimated to be around 30 billion by 2017, with content security, which includes email security, representing only 8% of that spend.
• Content Security is projected to have the smallest annual growth at 6.7%. In comparison Network Security is projected at 7.7% annual growth.
Email security is a critical component of your security
• Email is a core component of business processes
• Although it may not be high on security topical issues today it must be secured
• Compliance issues such as HIPPA and PCI mandates make email security a necessity for many
• Increase of targeted attacks and data breaches put more pressure on all organizations
From here down in this cell should be under the water:
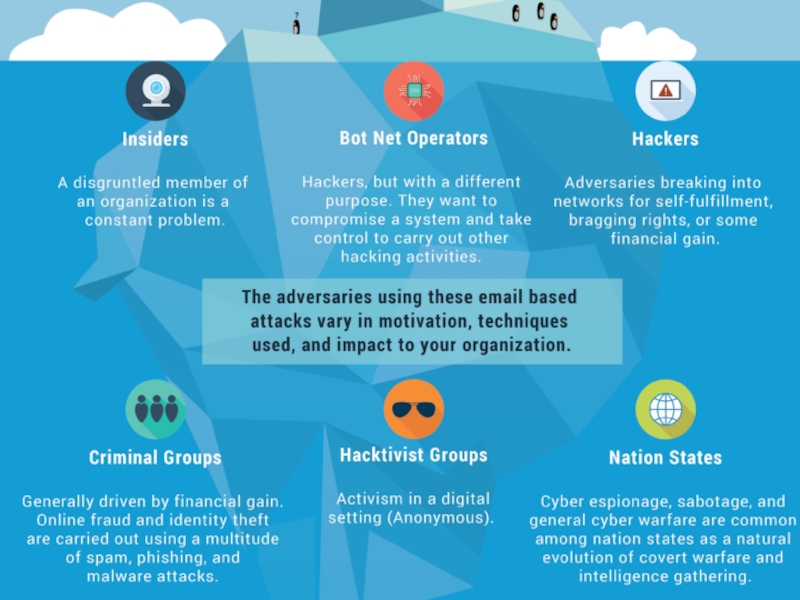
The adversaries using these email based attacks vary in motivation, techniques used and impact to your organization (each group could get a visual with a similar colour and graphic theme among the groups.)
- Hackers – Adversaries breaking into networks for self-fulfillment, bragging rights or some financial gain.
- Nation states – Cyber espionage, sabotage and general cyber warfare are common among nation states as a natural evolution of covert warfare and intelligence gathering.
- Criminal Groups – Generally driven by financial gain. Online fraud and identity theft are carried out using a multitude of spam, phishing and malware attacks.
- Hacktivist Groups – Activism in a digital setting. (Anonymous)
- Bot Net Operators - Hackers, but with a different purpose. They want to compromise a system and take control to carry out other hacking activities.
- Insiders - A disgruntled member of an organization is a constant problem nowadays.
Spam
- Spam and bulk style emails make up the largest volume of emails and are the greatest potential harm to productivity
- Spam is no longer about selling but stealing. It lures people into disclosing personal information or company information. Spam is used to spread bots in order to capture user information and send back to command and control server.
Phishing
- Phishing is the act of attempting to acquire information such as user names, passwords, or any other sensitive or valuable information by disguising as a trustworthy email address.
- Hackers are trending towards the use of social media content based phishing.
- 15.2% of spam was social media, short of email claiming to be from financial institutions at 15.9%
Targeted Attacks
- Targeted attacks are becoming more and more mainstream and have beat out spam and viruses as what is considered the main security concern.
- Spear phishing is the tactic of using social engineering to craft an email that appears to be from an individual or business to a specific target.
- 95% of targeted attacks, including APTs, began with a spear-phishing attack in 2013
- 31% of targeted attacks are at organizations less than 250
These random Facts that can be used if needed anywhere really:
- In 2012:
o 1 in 414 emails was a phishing attack
o 1 in 291 emails contained a virus
o 23% of email based malware is a URL
o In Q3 2013 global spam volume spiked 125%, almost 4 trillion messages, highest since august 2010
o 77% of security practitioners saw an increase in external threats
o 55% security professionals say securing new technologies is their number one organizational spend showing the industry trend to adopting more technology solutions
o 39% saying they will continue to spend the same
o Only 6% saying they will spend less This statement is used to identify the target audience and the challenge they are trying to overcome Specifically identify the member/role.
Should be adapted from our initial member understanding document. Max length at the analyst’s discretion.
Move your email to the cloud:
- Many back end business operations have already moved to the cloud. More and more functions will move as vendors develop and diversify their offerings for more customers.
- Email security has the benefit of either being with your cloud email provider, or just moving your ESG to the cloud for reduced in house IT strain.
- With cloud security developing as rapidly as it is, there is not much more room for hesitation. It makes sense: if Google can’t protect your email, do you think you can?
This overall insight is the central idea of the Blueprint. The overall insight should also drive the overall creative vision of the document. A well-crafted insight statement is key here. Try to make this statement short and sweet.
Member Understanding Insights:
- Assume you are a target – size, industry, doesn’t matter anymore. Whether you have valuable information, or are connected, or are just an average user, you’re a target.
- Growth rate of email usage are decreasing due to increase in other communication forms like instant messaging, texting, and social networks. But regardless of some decreasing growth trends, email overall usage is still on the rise and it here to stay. With that undisputable truth you need email communication security: Email Security Gateway (ESG).
- The only constant in security is change. The fact that you are secure one day may not mean anything the next day. The fact of the matter is that you are under attack. You may not know it, but your systems, network, data and users are all under threat and risk to be compromised with some malicious intention.
- Главная
- Разное
- Дизайн
- Бизнес и предпринимательство
- Аналитика
- Образование
- Развлечения
- Красота и здоровье
- Финансы
- Государство
- Путешествия
- Спорт
- Недвижимость
- Армия
- Графика
- Культурология
- Еда и кулинария
- Лингвистика
- Английский язык
- Астрономия
- Алгебра
- Биология
- География
- Детские презентации
- Информатика
- История
- Литература
- Маркетинг
- Математика
- Медицина
- Менеджмент
- Музыка
- МХК
- Немецкий язык
- ОБЖ
- Обществознание
- Окружающий мир
- Педагогика
- Русский язык
- Технология
- Физика
- Философия
- Химия
- Шаблоны, картинки для презентаций
- Экология
- Экономика
- Юриспруденция