- Главная
- Разное
- Дизайн
- Бизнес и предпринимательство
- Аналитика
- Образование
- Развлечения
- Красота и здоровье
- Финансы
- Государство
- Путешествия
- Спорт
- Недвижимость
- Армия
- Графика
- Культурология
- Еда и кулинария
- Лингвистика
- Английский язык
- Астрономия
- Алгебра
- Биология
- География
- Детские презентации
- Информатика
- История
- Литература
- Маркетинг
- Математика
- Медицина
- Менеджмент
- Музыка
- МХК
- Немецкий язык
- ОБЖ
- Обществознание
- Окружающий мир
- Педагогика
- Русский язык
- Технология
- Физика
- Философия
- Химия
- Шаблоны, картинки для презентаций
- Экология
- Экономика
- Юриспруденция
Partner Program презентация
Содержание
- 1. Partner Program
- 2. Technology Law: Regulations on the Internet and
- 3. Regulatory Environment Contractual Issues
- 4. Regulatory Environment Speed of Regulation Comparison over last 10 years
- 5. State in 2003 E-contracting Cybercrime/hacking
- 6. Personal Information FEDERAL FTC Act COPPA CAN-SPAM
- 7. Regulatory Environment - Background Terminology Data Privacy
- 8. A Bit of Historical Context…. Not actually
- 9. Regulatory Environment – Disclaimer Data Privacy and
- 10. Regulatory Environment Understand applicable obligations Geographic Source
- 11. Regulatory Environment Understand Applicable Obligations Personal Information
- 12. Regulatory Environment New Bills Location Privacy
- 13. Regulatory Environment Understand Applicable Obligations Personal Information
- 14. Regulatory Environment Understand Applicable Obligations Health Information
- 15. Regulatory Environment Understand Applicable Obligations Financial Information
- 16. Regulatory Environment Understand Applicable Obligations Employee Information
- 17. Regulatory Environment Understand Applicable Obligations EU
- 18. Regulatory Environment Credit Card Data PCI DSS
- 19. Regulatory Environment Security Audit “systematic, measurable technical
- 20. Regulatory Environment WISP Consider Insurance Options
- 21. Regulatory Environment Internal Privacy Program Data Retention Schedule Regularly Review
- 22. Why Do We Care The Regulators are
- 23. Why Do We Care Corporate Governance Issues
- 24. Why Do We Care Valuation Reputational Value
- 25. Why Do We Care Vendor Relationships Implicates
- 26. Why Do We Care Mobile App Development
- 27. Why Do We Care Ask Questions
- 28. Why Do We Care Key Provisions to
- 29. Why Do We Care Responsibility for breach
- 30. Other Considerations IP law trailing the technology
- 31. Other Considerations Ownership of Data Preservation of
- 32. Other Considerations Determine accountability for data preservation
- 33. Other Considerations Intellectual Property Whose software Whose
- 34. Other Considerations Service Levels Online contracting –
- 35. Questions??? Thank you for your partnership!
Слайд 2Technology Law: Regulations on the Internet and Emerging Technologies
Heather L. Buchta
Quarles
& Brady LLP
September 4, 2014
September 4, 2014
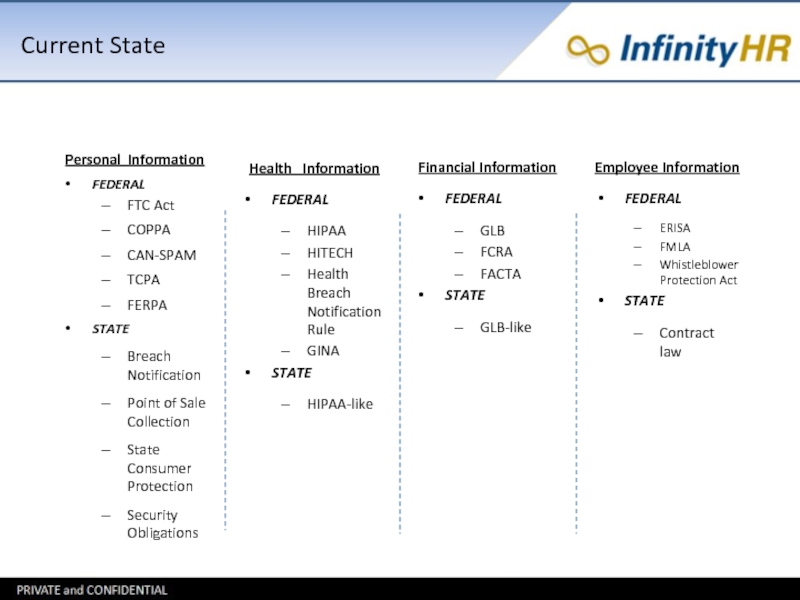
Слайд 6Personal Information
FEDERAL
FTC Act
COPPA
CAN-SPAM
TCPA
FERPA
STATE
Breach Notification
Point of Sale Collection
State Consumer Protection
Security Obligations
Health
Information
FEDERAL
HIPAA
HITECH
Health Breach Notification Rule
GINA
STATE
HIPAA-like
FEDERAL
HIPAA
HITECH
Health Breach Notification Rule
GINA
STATE
HIPAA-like
Financial Information
FEDERAL
GLB
FCRA
FACTA
STATE
GLB-like
Employee Information
FEDERAL
ERISA
FMLA
Whistleblower Protection Act
STATE
Contract law
Current State
Слайд 7Regulatory Environment - Background
Terminology
Data Privacy
Data Security
Cybersecurity
Co-Lo
Cloud
Legal Framework
Sectoral
Comprehensive
Слайд 8A Bit of Historical Context….
Not actually a new topic
Warren and Brandeis
– 1890
Prosser – 1960
Fair Information Practices – 1973
Guidelines Governing the Protection of Privacy and Transborder Data Flows of Personal Data – 1980
Council of Europe – 1981
EU Data Protection Directive – 1995
APEC Privacy Framework – 2004
Prosser – 1960
Fair Information Practices – 1973
Guidelines Governing the Protection of Privacy and Transborder Data Flows of Personal Data – 1980
Council of Europe – 1981
EU Data Protection Directive – 1995
APEC Privacy Framework – 2004
Слайд 9Regulatory Environment – Disclaimer
Data Privacy and Protection
Health Care
Financial
Labor & Employment
Trade Secrets
Internet
of Things
BYOD
Other Regulations
Online contracting
All other offline business regulations – FCC, FTC, etc.
BYOD
Other Regulations
Online contracting
All other offline business regulations – FCC, FTC, etc.
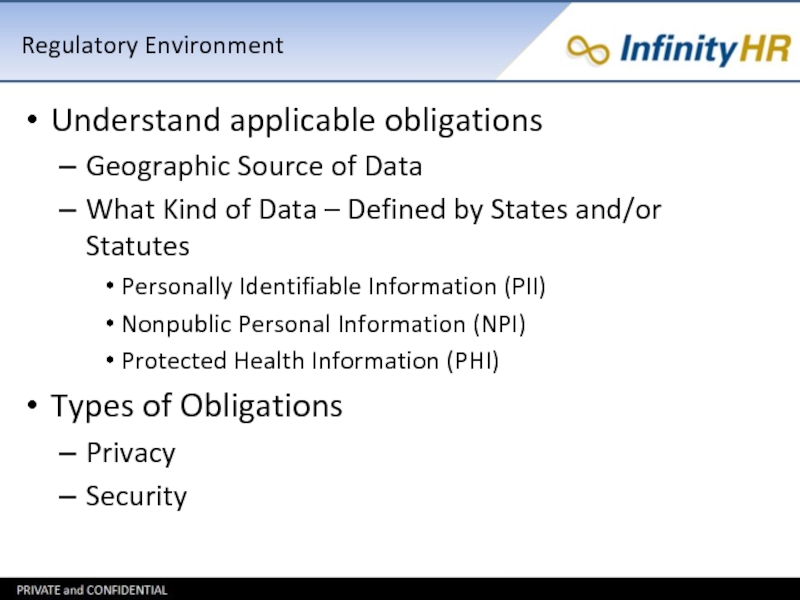
Слайд 10Regulatory Environment
Understand applicable obligations
Geographic Source of Data
What Kind of Data –
Defined by States and/or Statutes
Personally Identifiable Information (PII)
Nonpublic Personal Information (NPI)
Protected Health Information (PHI)
Types of Obligations
Privacy
Security
Personally Identifiable Information (PII)
Nonpublic Personal Information (NPI)
Protected Health Information (PHI)
Types of Obligations
Privacy
Security
Слайд 11Regulatory Environment
Understand Applicable Obligations
Personal Information
Federal
FTC
Section 5 of the FTC Act
Telemarketing
Sales Rule
COPPA
CAN-SPAM
FCC
Telephone Consumer Protection Act
USDOE
FERPA
Electronic Communications Privacy Act
COPPA
CAN-SPAM
FCC
Telephone Consumer Protection Act
USDOE
FERPA
Electronic Communications Privacy Act
Слайд 12Regulatory Environment
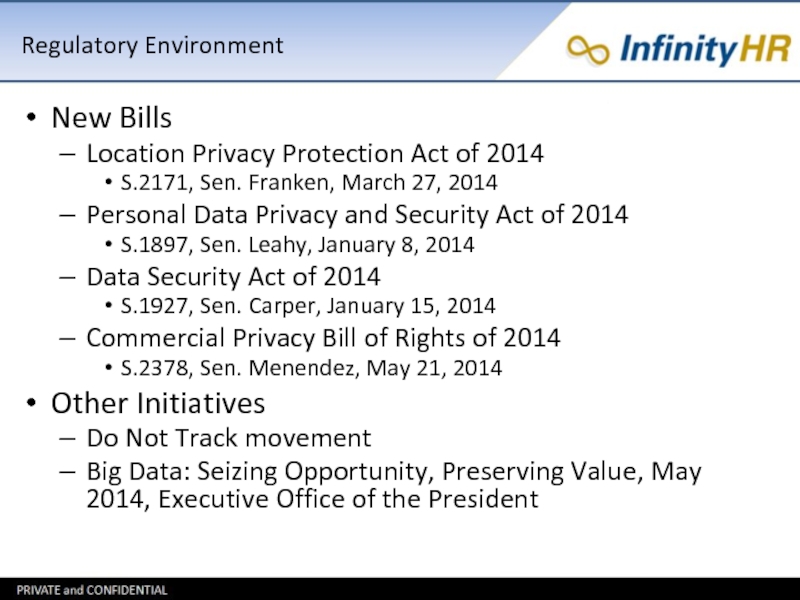
New Bills
Location Privacy Protection Act of 2014
S.2171, Sen. Franken,
March 27, 2014
Personal Data Privacy and Security Act of 2014
S.1897, Sen. Leahy, January 8, 2014
Data Security Act of 2014
S.1927, Sen. Carper, January 15, 2014
Commercial Privacy Bill of Rights of 2014
S.2378, Sen. Menendez, May 21, 2014
Other Initiatives
Do Not Track movement
Big Data: Seizing Opportunity, Preserving Value, May 2014, Executive Office of the President
Personal Data Privacy and Security Act of 2014
S.1897, Sen. Leahy, January 8, 2014
Data Security Act of 2014
S.1927, Sen. Carper, January 15, 2014
Commercial Privacy Bill of Rights of 2014
S.2378, Sen. Menendez, May 21, 2014
Other Initiatives
Do Not Track movement
Big Data: Seizing Opportunity, Preserving Value, May 2014, Executive Office of the President
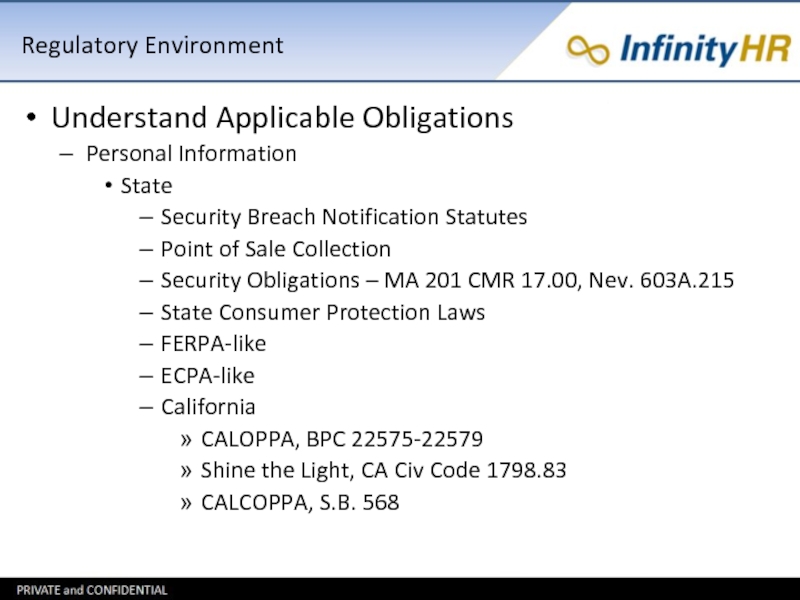
Слайд 13Regulatory Environment
Understand Applicable Obligations
Personal Information
State
Security Breach Notification Statutes
Point of Sale Collection
Security
Obligations – MA 201 CMR 17.00, Nev. 603A.215
State Consumer Protection Laws
FERPA-like
ECPA-like
California
CALOPPA, BPC 22575-22579
Shine the Light, CA Civ Code 1798.83
CALCOPPA, S.B. 568
State Consumer Protection Laws
FERPA-like
ECPA-like
California
CALOPPA, BPC 22575-22579
Shine the Light, CA Civ Code 1798.83
CALCOPPA, S.B. 568
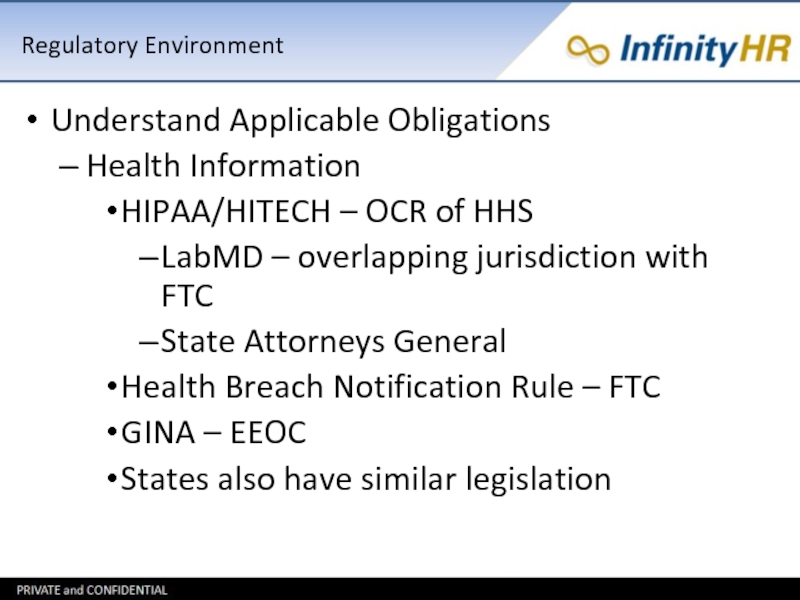
Слайд 14Regulatory Environment
Understand Applicable Obligations
Health Information
HIPAA/HITECH – OCR of HHS
LabMD – overlapping
jurisdiction with FTC
State Attorneys General
Health Breach Notification Rule – FTC
GINA – EEOC
States also have similar legislation
State Attorneys General
Health Breach Notification Rule – FTC
GINA – EEOC
States also have similar legislation
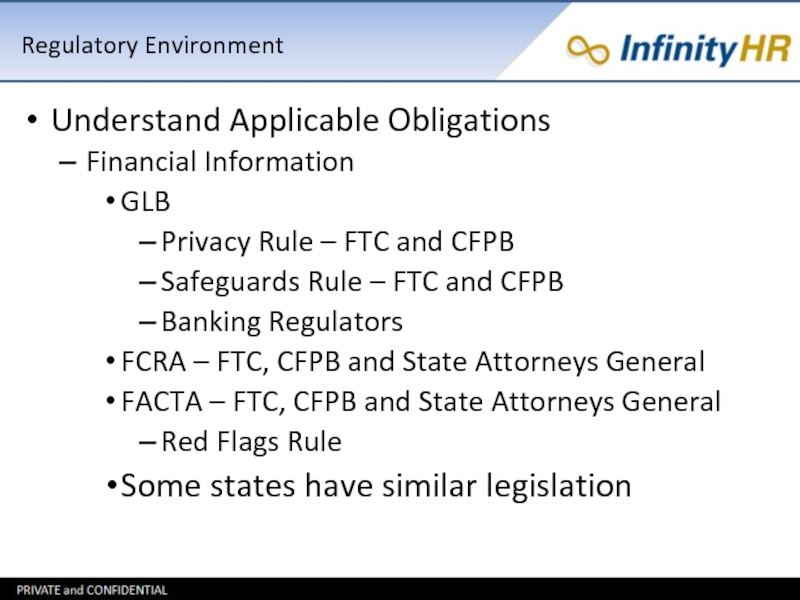
Слайд 15Regulatory Environment
Understand Applicable Obligations
Financial Information
GLB
Privacy Rule – FTC and CFPB
Safeguards Rule
– FTC and CFPB
Banking Regulators
FCRA – FTC, CFPB and State Attorneys General
FACTA – FTC, CFPB and State Attorneys General
Red Flags Rule
Some states have similar legislation
Banking Regulators
FCRA – FTC, CFPB and State Attorneys General
FACTA – FTC, CFPB and State Attorneys General
Red Flags Rule
Some states have similar legislation
Слайд 16Regulatory Environment
Understand Applicable Obligations
Employee Information
ADA
HIPAA
State Specific Rules – social media
Employee Handbooks
Union
Agreements/Collective Bargaining Agreements
Слайд 17Regulatory Environment
Understand Applicable Obligations
EU
Directives – Personal Information and Cookie
DPAs
Works Councils
Canada
PIPEDA
CASL
Australia
Privacy Amendment Act 2012
Слайд 18Regulatory Environment
Credit Card Data
PCI DSS v.3
Nevada 603A.215
Minnesota 325E.64
Online Tracking
Digital Advertising Alliance
OBA
and retargeting
NIST
Media Sanitization
Cybersecurity Framework
NERC
Contractual obligations and self-imposed obligations
NIST
Media Sanitization
Cybersecurity Framework
NERC
Contractual obligations and self-imposed obligations
Слайд 19Regulatory Environment
Security Audit
“systematic, measurable technical assessment of how the organization's security
policy is employed at a specific site” (Symantec 2003)
“appropriate” and “reasonable”
What is involved?
Personal interviews
Vulnerability scans (pen-testing)
Examinations of operating system settings
Analyses of network shares and other data
Go to the experts
Find the right vendor
Set parameters
“appropriate” and “reasonable”
What is involved?
Personal interviews
Vulnerability scans (pen-testing)
Examinations of operating system settings
Analyses of network shares and other data
Go to the experts
Find the right vendor
Set parameters
Слайд 20Regulatory Environment
WISP
Consider Insurance Options
Identify Key Team Members
Key Executives
Compliance – CISO?
Legal
Marketing/HR
PR
IT/Forensics
Incident
Response Vendor?
Incident Response Plan
Tabletop Exercises
Incident Response Plan
Tabletop Exercises
Слайд 22Why Do We Care
The Regulators are Coming….
FTC
Attorneys’ General
And they are bringing
bad press, fines and Enforcement Orders
Слайд 23Why Do We Care
Corporate Governance Issues
SEC Investigations
Officer Liability
Have to Stay Informed
NACD
White Paper – Cybersecurity Boardroom Implications (2014)
SEC Cybersecurity Roundtable Transcript, 3/28/14, available at www.sec.gov
SEC Cybersecurity Roundtable Transcript, 3/28/14, available at www.sec.gov
Слайд 24Why Do We Care
Valuation
Reputational Value
Corporate Deals - M&A
High Profile Deals
WhatsApp, Moves,
Nest
Impacting the Bottom Line
Restricting Ability to Transfer
Impacting the Bottom Line
Restricting Ability to Transfer
Слайд 25Why Do We Care
Vendor Relationships
Implicates both privacy and security
Outsourcing does not
mean relinquishing obligations or liability
Must do due diligence
Appropriate contractual provisions
Maintain level of control and knowledge of activities
Must do due diligence
Appropriate contractual provisions
Maintain level of control and knowledge of activities
Слайд 26Why Do We Care
Mobile App Development
Privacy By Design
Hosting Facilities
Security Requirements
Breach
Notifications
SaaS
Data Ownership/Access/Return
Data Usage
Marketing
Retargeting
OBA
SaaS
Data Ownership/Access/Return
Data Usage
Marketing
Retargeting
OBA
Слайд 27Why Do We Care
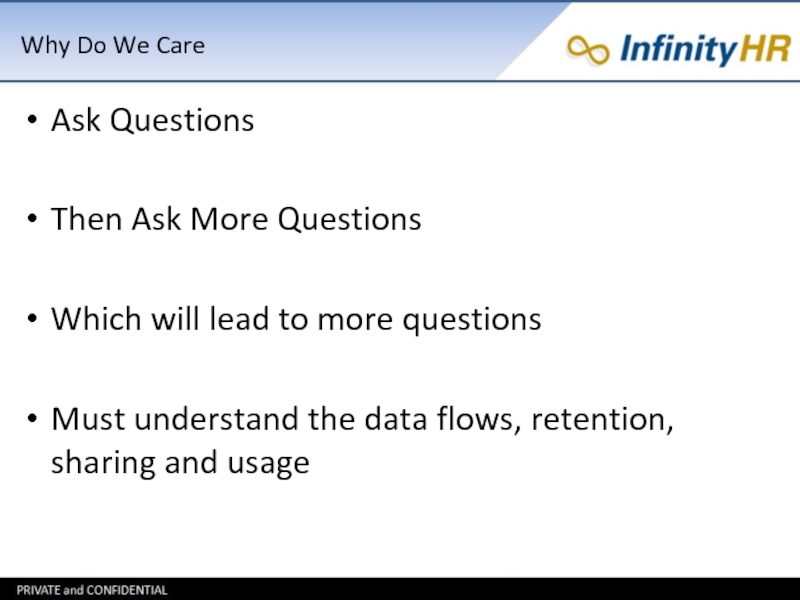
Ask Questions
Then Ask More Questions
Which will lead to
more questions
Must understand the data flows, retention, sharing and usage
Must understand the data flows, retention, sharing and usage
Слайд 28Why Do We Care
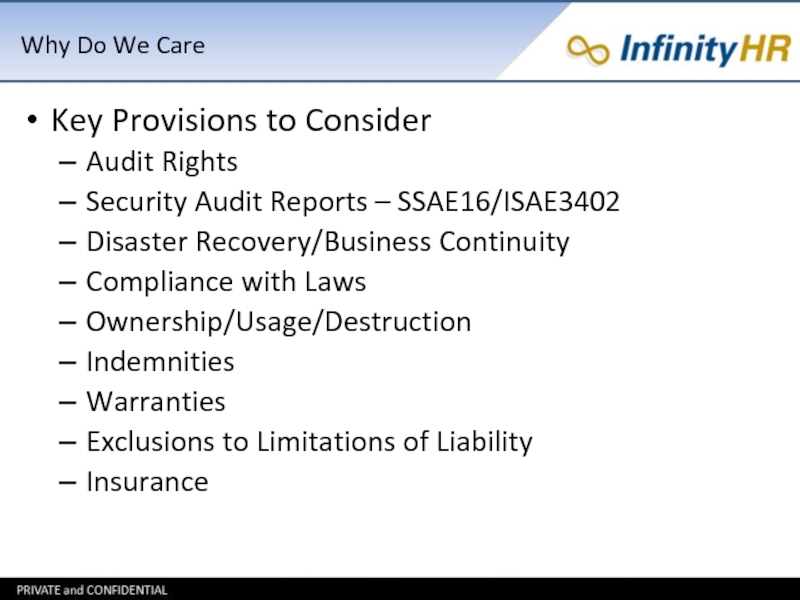
Key Provisions to Consider
Audit Rights
Security Audit Reports –
SSAE16/ISAE3402
Disaster Recovery/Business Continuity
Compliance with Laws
Ownership/Usage/Destruction
Indemnities
Warranties
Exclusions to Limitations of Liability
Insurance
Disaster Recovery/Business Continuity
Compliance with Laws
Ownership/Usage/Destruction
Indemnities
Warranties
Exclusions to Limitations of Liability
Insurance
Слайд 29Why Do We Care
Responsibility for breach of security is a function
of who controls the data
Liability for breach of security is a function of the contract
Compliance with laws may be a domestic and/or foreign matter
Liability for breach of security is a function of the contract
Compliance with laws may be a domestic and/or foreign matter
Слайд 30Other Considerations
IP law trailing the technology evolution of the Cloud
Trade Secrets
and the Cloud may be incompatible
Potential third-party disclosures
US PATRIOT Act
Evolving licensing models
Potential data location issues
Legacy software and systems issues
Potential third-party disclosures
US PATRIOT Act
Evolving licensing models
Potential data location issues
Legacy software and systems issues
Слайд 31Other Considerations
Ownership of Data
Preservation of Data
Preservation may be easier on the
cloud…or not
Courts may not distinguish servers in the cloud
Physical location of Data may be unknown
Compliance with e-discovery and litigation holds
Spoliation
Data Integrity
Must be free from corruption
Courts may not distinguish servers in the cloud
Physical location of Data may be unknown
Compliance with e-discovery and litigation holds
Spoliation
Data Integrity
Must be free from corruption
Слайд 32Other Considerations
Determine accountability for data preservation
Who is liable for stolen data
What
does indemnification cover
What happens in bankruptcy
What notice is provided for security breach
What happens if lose co-lo contract or lose lease
What happens in bankruptcy
What notice is provided for security breach
What happens if lose co-lo contract or lose lease
Слайд 33Other Considerations
Intellectual Property
Whose software
Whose network
Ownership
Customizations or configurations
Works made for hire
Same contractual
provisions come into play – now from an IP perspective