- Главная
- Разное
- Дизайн
- Бизнес и предпринимательство
- Аналитика
- Образование
- Развлечения
- Красота и здоровье
- Финансы
- Государство
- Путешествия
- Спорт
- Недвижимость
- Армия
- Графика
- Культурология
- Еда и кулинария
- Лингвистика
- Английский язык
- Астрономия
- Алгебра
- Биология
- География
- Детские презентации
- Информатика
- История
- Литература
- Маркетинг
- Математика
- Медицина
- Менеджмент
- Музыка
- МХК
- Немецкий язык
- ОБЖ
- Обществознание
- Окружающий мир
- Педагогика
- Русский язык
- Технология
- Физика
- Философия
- Химия
- Шаблоны, картинки для презентаций
- Экология
- Экономика
- Юриспруденция
Legal aspects of Handling Cyber Frauds презентация
Содержание
- 1. Legal aspects of Handling Cyber Frauds
- 2. What is a Cyber Crime? An unlawful
- 3. “CYBERSPACE”
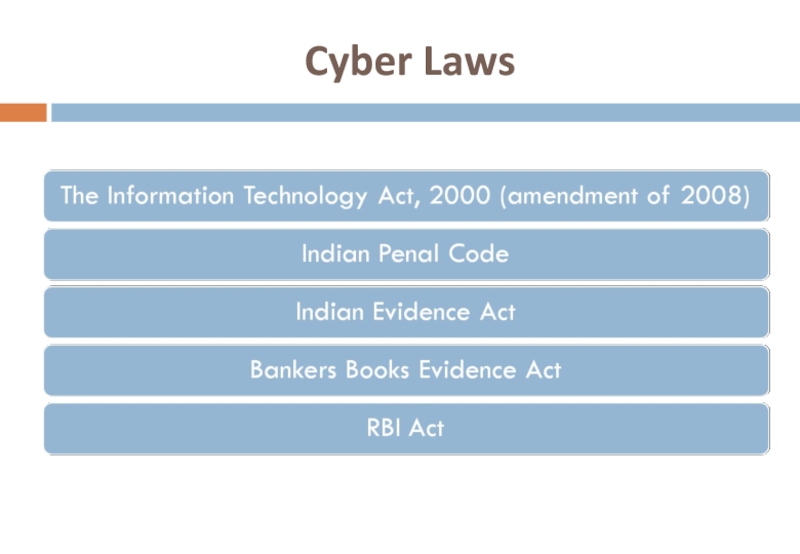
- 4. Cyber Laws
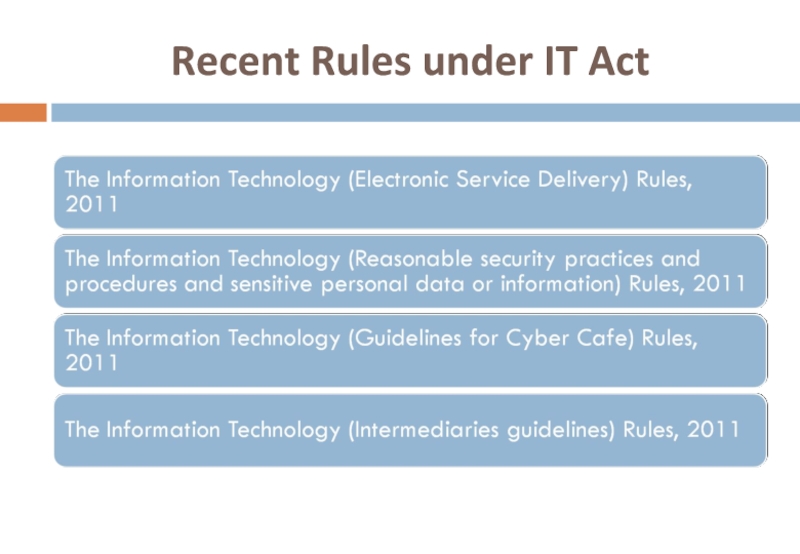
- 5. Recent Rules under IT Act
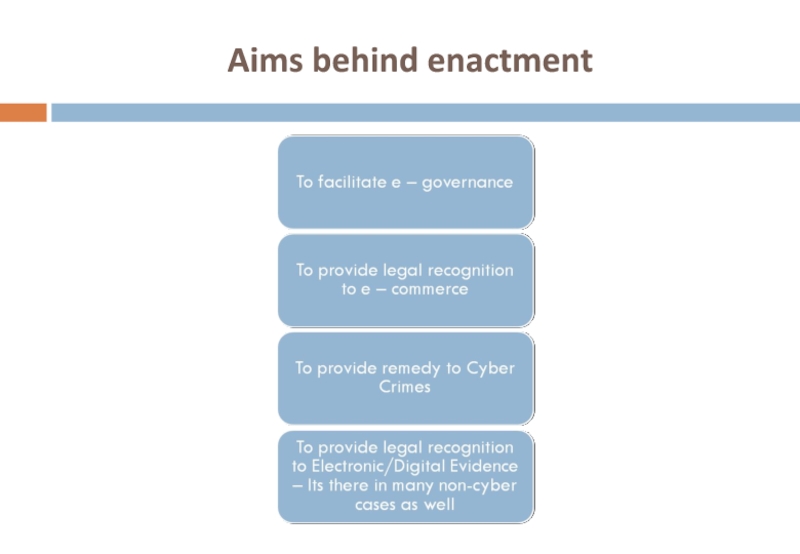
- 6. Aims behind enactment
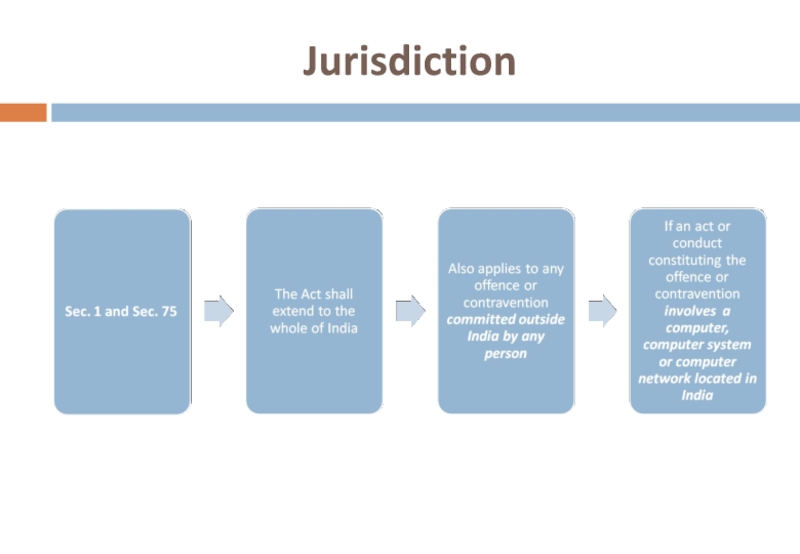
- 7. Jurisdiction
- 8. Virtual World Population Explosion : 1
- 9. 1 Dirty SMS = 3 Years of
- 10. Threatening email was sent from this cyber
- 11. Accounting Software worth crores is
- 12. Case Study 4 Stake
- 13. Case Study 5 LOSS
- 14. Where is the evidence ?
- 15. Forensics is the process of using scientific
- 16. Digital Evidence Digital evidence is information
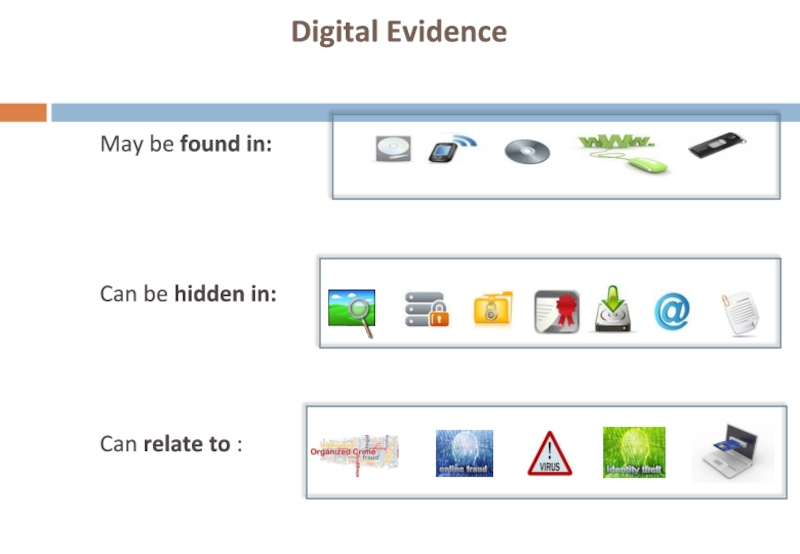
- 17. May be found in:
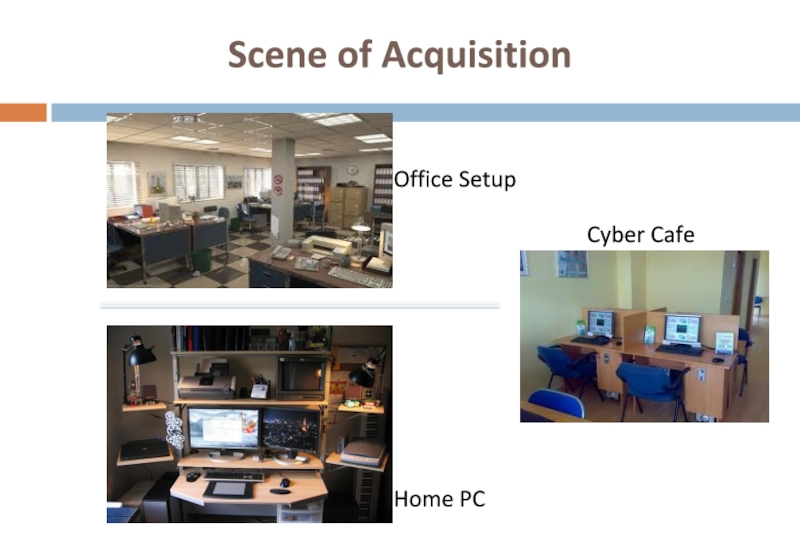
- 18. Office Setup Cyber Cafe Home PC Scene of Acquisition
- 19. Computer Forensics process would involve….. Forensic analysis
- 20. Steps in Computer Forensics Identification
- 21. THE A TEAM Domain Expert Computer Forensics expert Forensics Accounting expert Software expert Lawyer
- 22. Acquisition of Media
- 23. DOCUMENTATION….
- 24. Documentation & Reporting
- 25. Evidence Forms A detailed sheet about each
- 26. Chain of Custody The movement and location
- 27. Creating an Image of Media Image is
- 28. Write blockers & alternatives Write-blocker is a
- 29. Indian Evidence Act Sec. 3
- 30. Sec. 65B - Admissibility of electronic records
- 31. Sec. 88A - Presumption as to electronic
- 32. The Information Technology Act Sec. 79A -
- 33. CIVIL OFFENCES
- 34. Section 43 Unauthorised Access Remedy – Damages
- 35. Adjudication
- 37. Shri. Thomas Raju Vs ICICI Bank
- 38. Section 66 Removal of definition
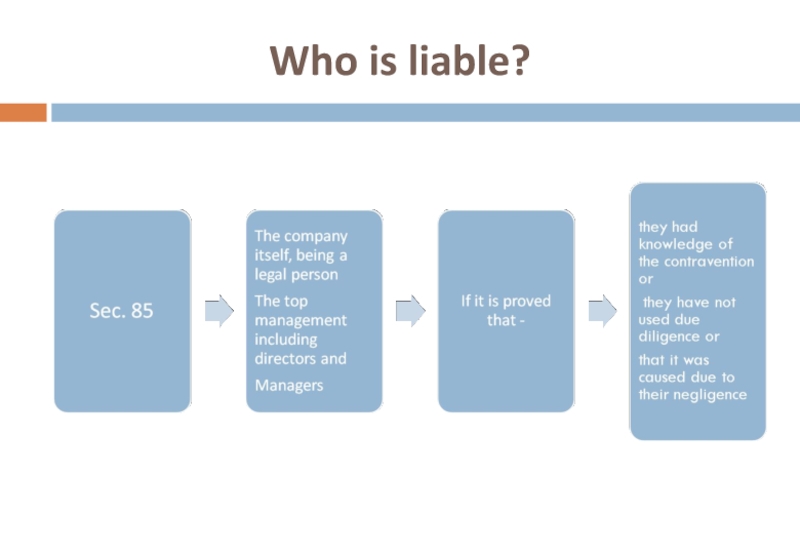
- 39. Section 43(A) – Compensation for failure to
- 40. HSBC - Nadeem Kashmiri case Based on
- 41. Who is liable?
- 42. Issues What is Sensitive Personal Information? What are Reasonable Security Practices and Procedures?
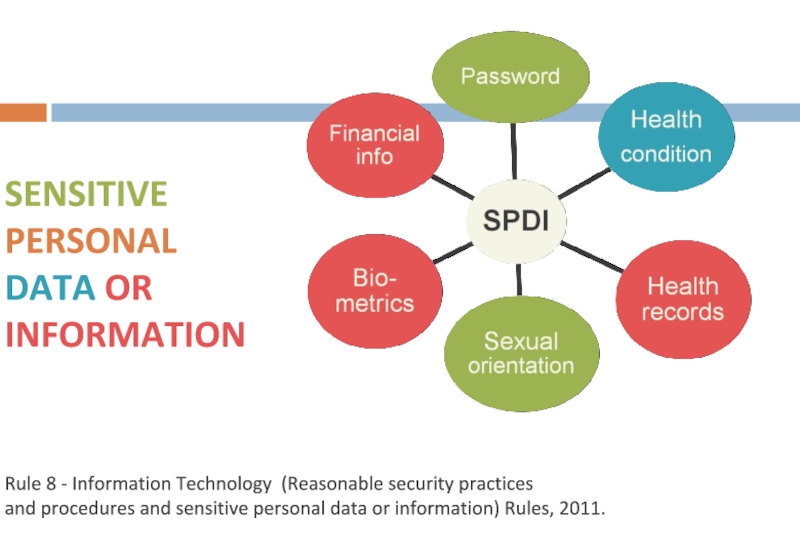
- 43. SENSITIVE PERSONAL DATA OR INFORMATION Rule
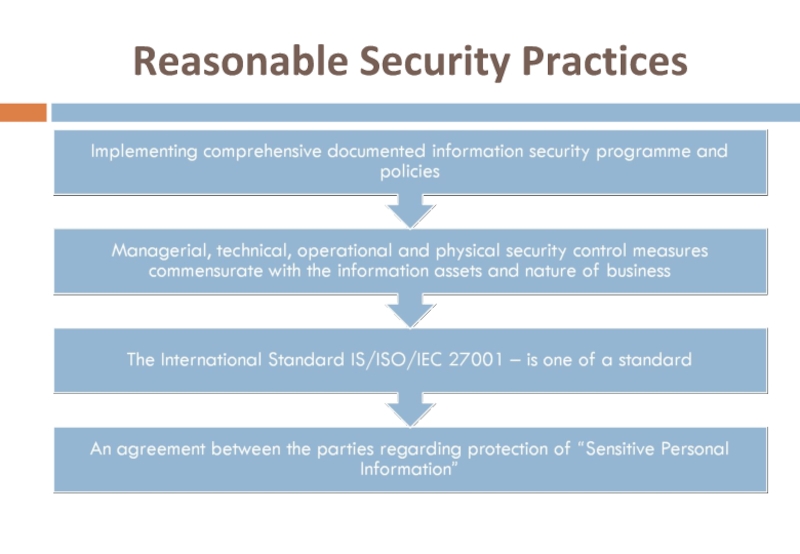
- 44. Reasonable Security Practices
- 45. Auditing
- 46. COMPLIANCE POLICIES
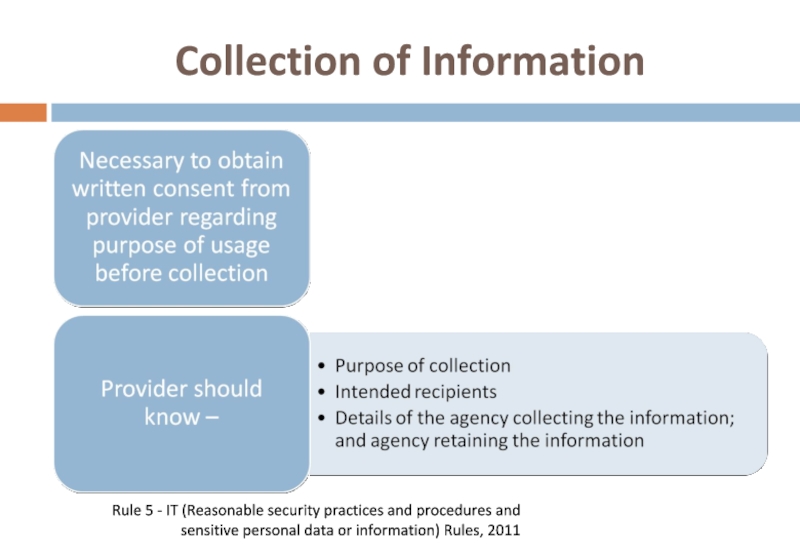
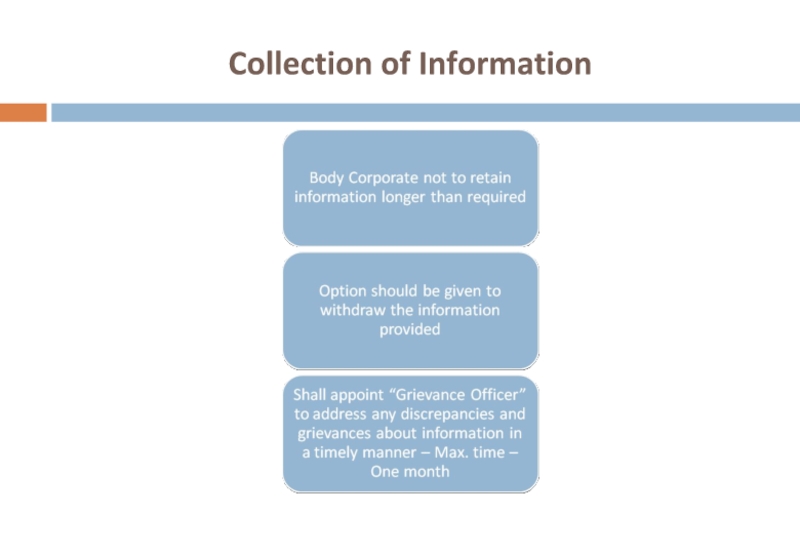
- 47. Collection of Information Rule 5 - IT
- 48. Collection of Information
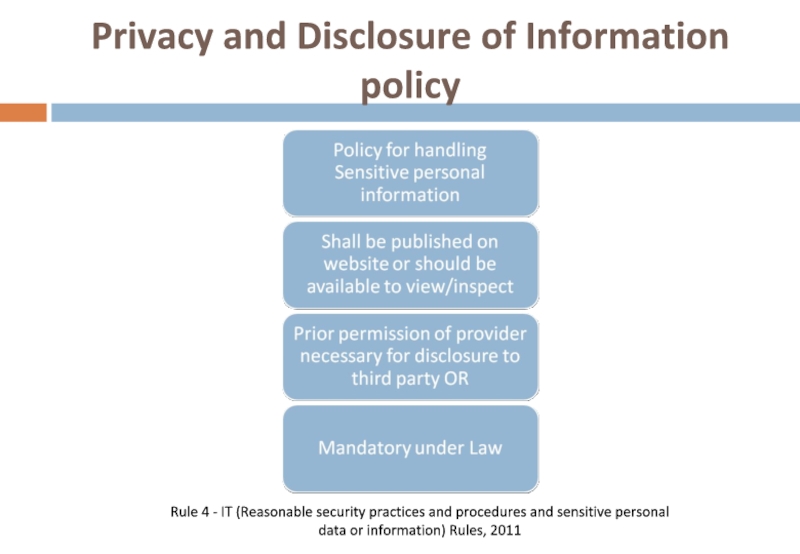
- 49. Privacy and Disclosure of Information policy Rule
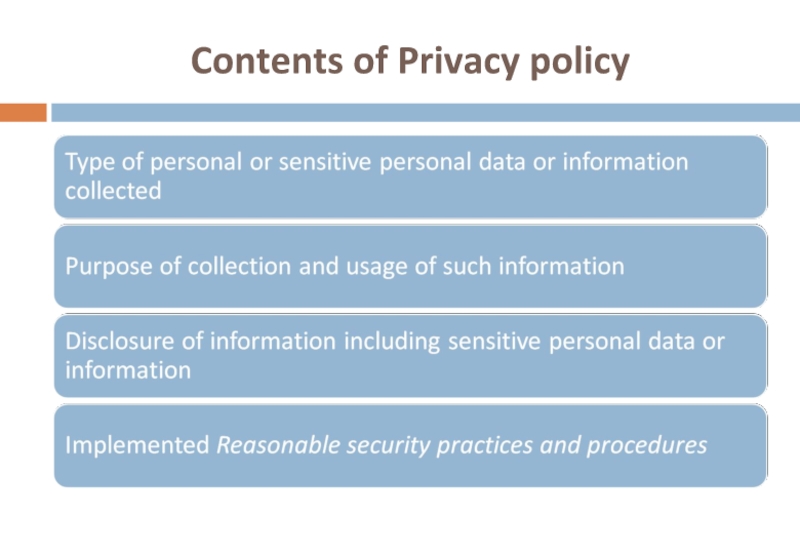
- 50. Contents of Privacy policy
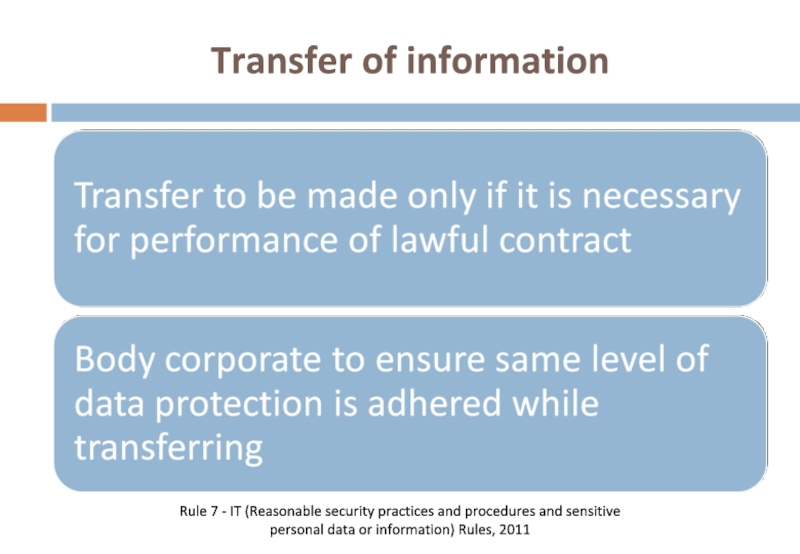
- 51. Disclosure Rule 6 - IT (Reasonable security
- 52. Transfer of information Rule 7 - IT
- 53. Sec 72(A) (Criminal offence) Punishment for Disclosure
- 54. CRIMINAL OFFENCES
- 55. Section 66 A Sending of offensive
- 56. Section 66 B Dishonestly receiving stolen computer
- 57. Section 66 C Identity theft Fraudulently or
- 58. Section 66 D Cheating by Personation Cheating
- 59. Investigation Powers Section 78 Cyber crime
- 60. Sec. 79 Liability of Intermediary Intermediary
- 61. Sec. 79 Liability of Intermediary Observing
- 62. Compounding of Offences Section 77 (A)
- 63. Issues
- 64. Possible Solutions
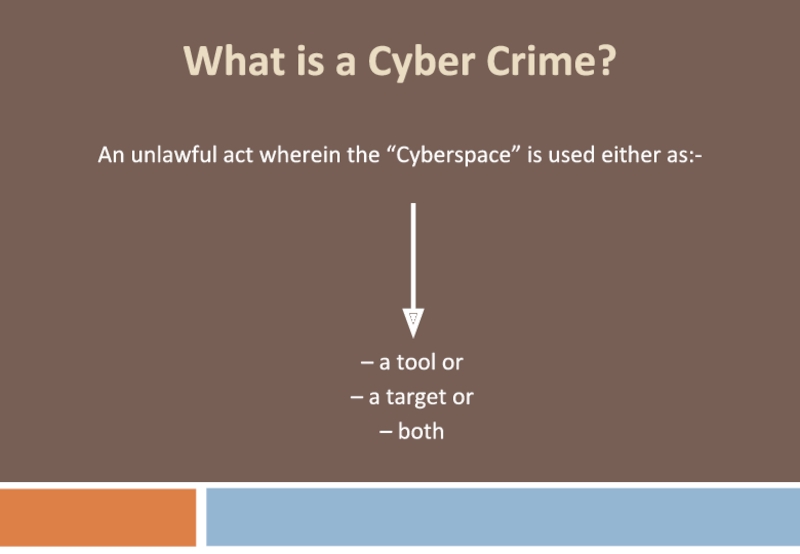
Слайд 2What is a Cyber Crime?
An unlawful act wherein the “Cyberspace” is
a tool or
a target or
both
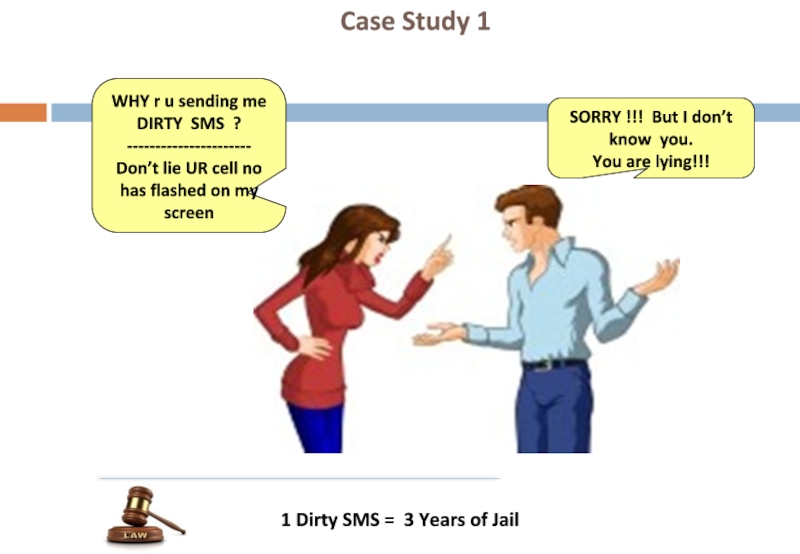
Слайд 91 Dirty SMS = 3 Years of Jail
Case Study 1
WHY
----------------------
Don’t lie UR cell no has flashed on my screen
SORRY !!! But I don’t know you.
You are lying!!!
Слайд 10Threatening email was sent from this cyber café.
POLICE
Cyber Café has
HOW do I Investigate. ?
1 Threatening Email = 3 Years of Jail
Case Study 2
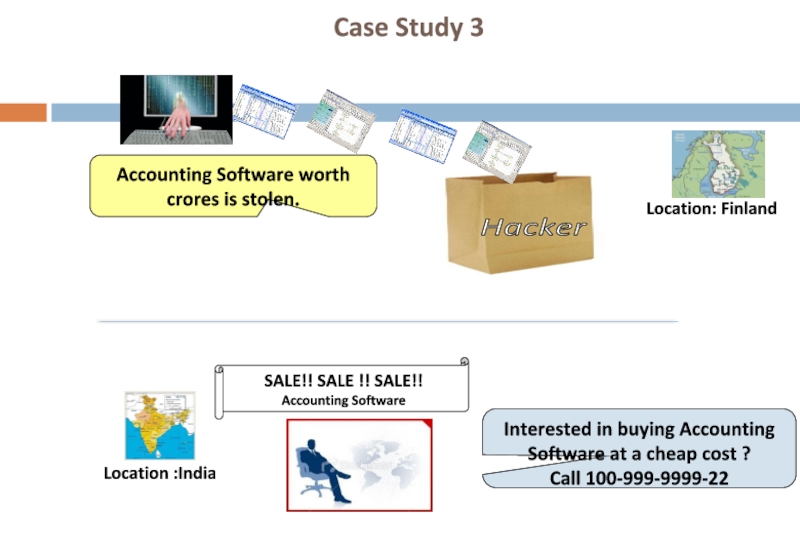
Слайд 11
Accounting Software worth crores is stolen.
Interested in buying Accounting Software at
Call 100-999-9999-22
Location :India
SALE!! SALE !! SALE!!
Accounting Software
Location: Finland
Case Study 3
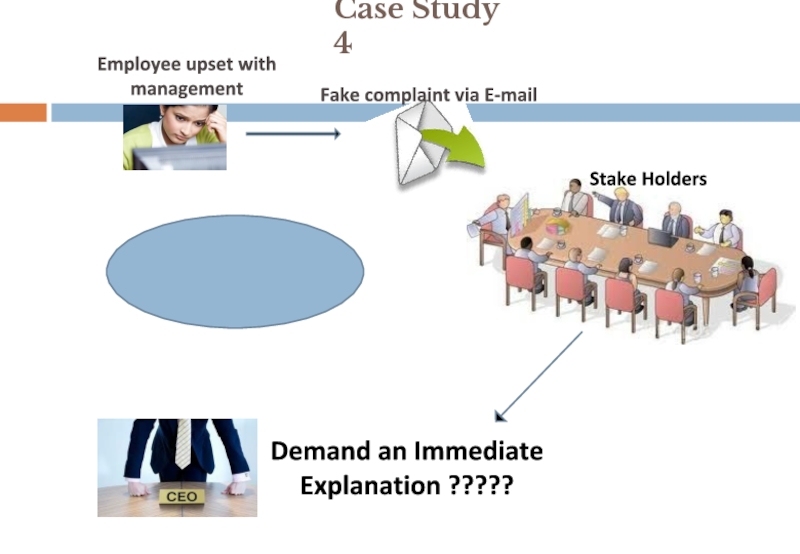
Слайд 12
Case Study 4
Stake Holders
Fake complaint via E-mail
Employee upset with
management
Demand
Explanation ?????
Disgruntled
Employee
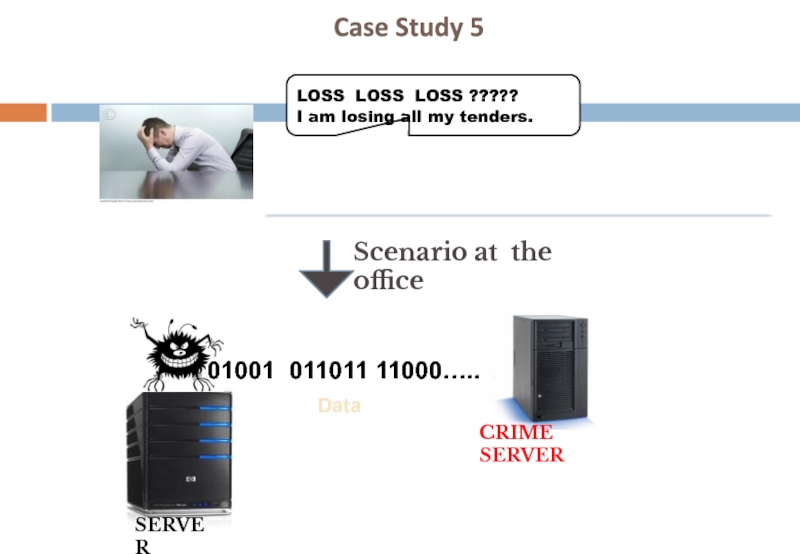
Слайд 13Case Study 5
LOSS LOSS LOSS ?????
I am losing all my
SERVER
Data
01001 011011 11000…..
CRIME SERVER
Scenario at the office
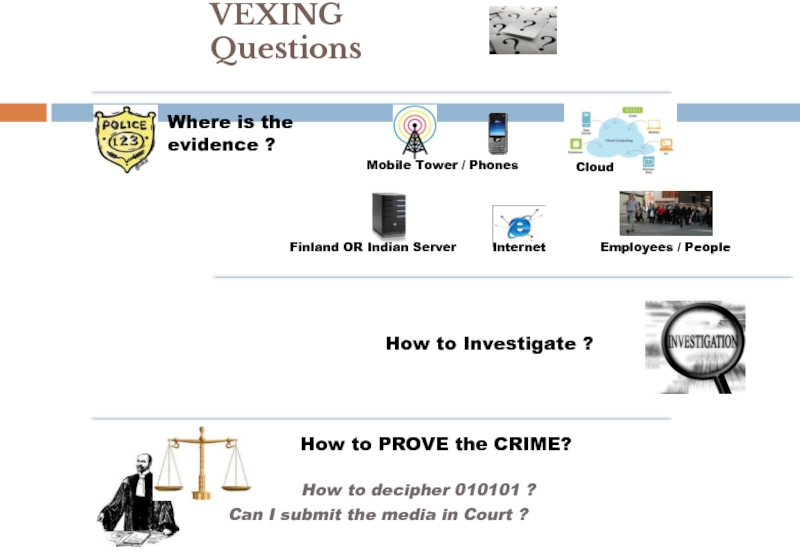
Слайд 14Where is the
evidence ?
Mobile Tower / Phones
Finland OR Indian Server
Cloud
Internet
How
Employees / People
How to PROVE the CRIME?
How to decipher 010101 ?
Can I submit the media in Court ?
VEXING Questions
Слайд 15Forensics is the process of using scientific knowledge for collecting, analyzing,
Computer Forensics as the discipline that combines elements of law and computer science to collect and analyze data from computer systems, networks, wireless communications, and storage devices in a way that is admissible as evidence in a court of law.
Source : http://www.us-cert.gov/reading_room/forensics.pdf
Forensics & Computer Forensics
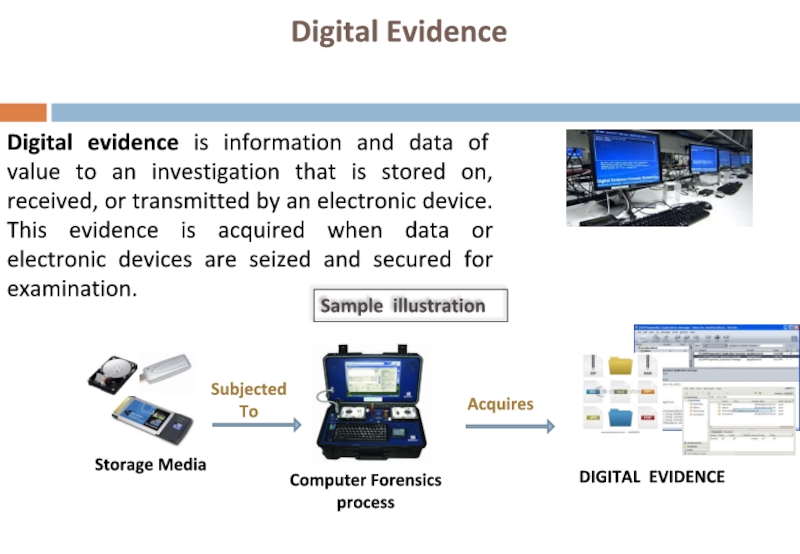
Слайд 16Digital Evidence
Digital evidence is information and data of value to an
Sample illustration
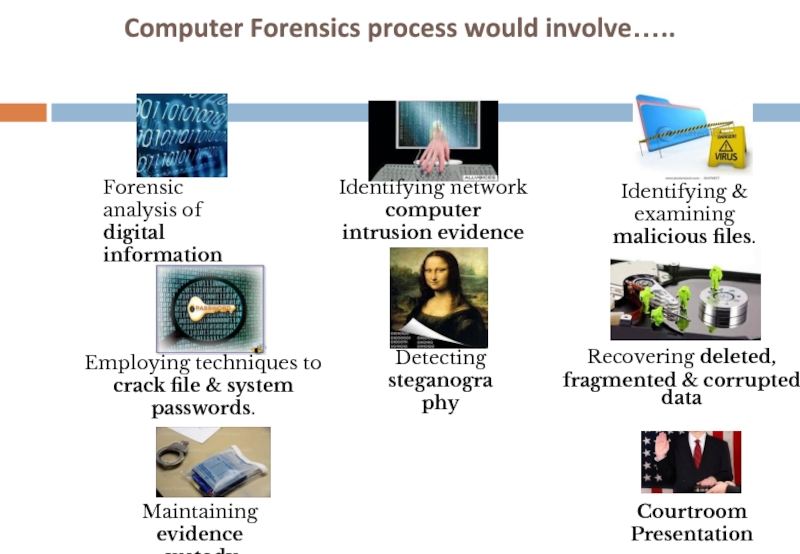
Слайд 19Computer Forensics process would involve…..
Forensic analysis of
digital information
Identifying network computer
intrusion evidence
Identifying & examining
malicious files.
Employing techniques to
crack file & system passwords.
Detecting
steganography
Recovering deleted,
fragmented & corrupted data
Maintaining evidence
custody procedures
Courtroom Presentation
Слайд 20Steps in Computer Forensics
Identification of Digital Evidence
Acquisition of Media
Forensic Analysis of
Documentation & Reporting
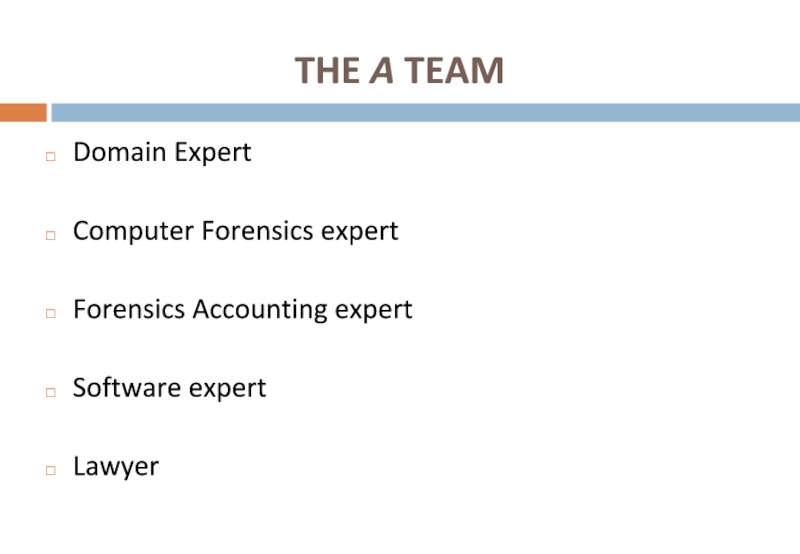
Слайд 21THE A TEAM
Domain Expert
Computer Forensics expert
Forensics Accounting expert
Software expert
Lawyer
Слайд 22
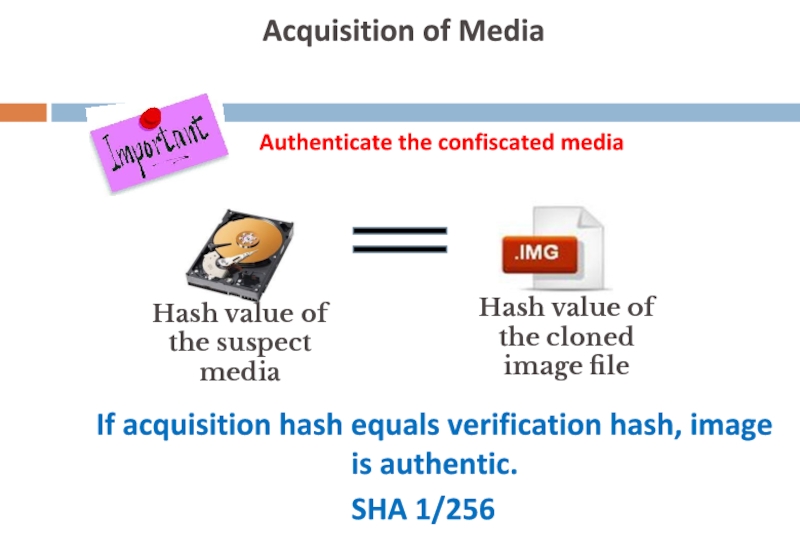
Acquisition of Media
Authenticate the confiscated media
Hash value of the
Hash value of the cloned image file
If acquisition hash equals verification hash, image is authentic.
SHA 1/256
Слайд 24
Documentation & Reporting
Broad outline of Computer Forensic Report
Introduction to the case
Background
Details of forensic analysis carried out
Certification
Слайд 25Evidence Forms
A detailed sheet about each evidence item
Item serial number
Item detailed
Type
Make
Model
Date and time collected
Notes
Any serial numbers, labels
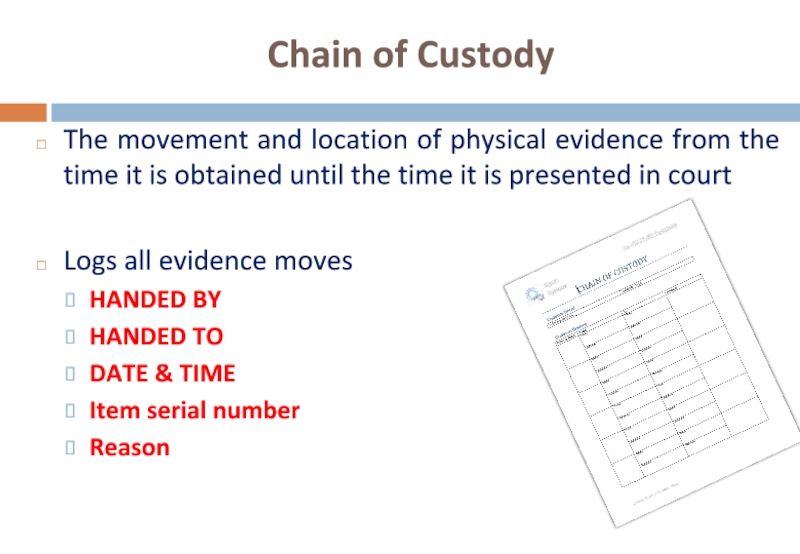
Слайд 26Chain of Custody
The movement and location of physical evidence from the
Logs all evidence moves
HANDED BY
HANDED TO
DATE & TIME
Item serial number
Reason
Слайд 27Creating an Image of Media
Image is a bit-for-bit copy of the
If a disk has 5000 sectors, then the image created will have an exact copy of all 5000 sectors in the same order
Media (evidence) must be protected from accidental writes / alterations
Hard disk (media)
Write-blocker Device
Imaging workstation
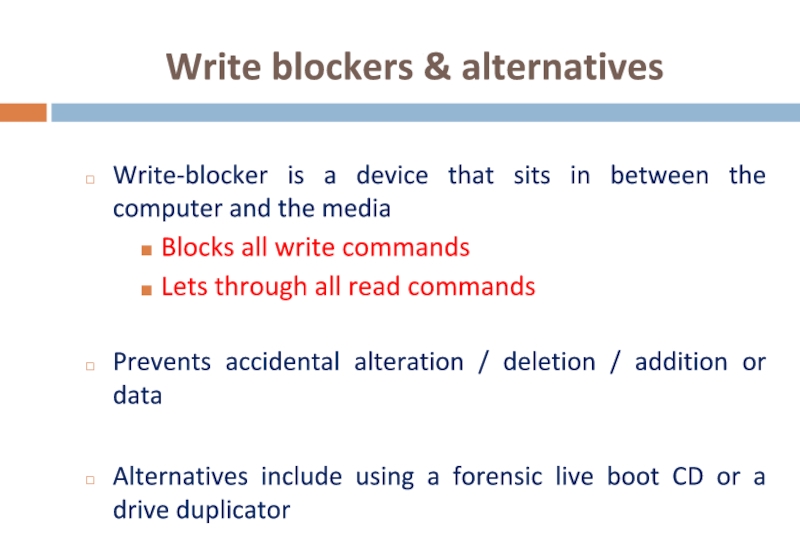
Слайд 28Write blockers & alternatives
Write-blocker is a device that sits in between
Blocks all write commands
Lets through all read commands
Prevents accidental alteration / deletion / addition or data
Alternatives include using a forensic live boot CD or a drive duplicator
Слайд 29Indian Evidence Act
Sec. 3 (a) – Scope of definition of evidence
Слайд 30Sec. 65B - Admissibility of electronic records
The person owning or in-charge
INDIAN EVIDENCE ACT
Слайд 31Sec. 88A - Presumption as to electronic messages
The Court may presume
INDIAN EVIDENCE ACT
Слайд 32The Information Technology Act
Sec. 79A - Central Government to notify Examiner
The Central Government may, for the purposes of providing expert opinion on electronic evidence before any court or other authority specify, by notification in the Official Gazette, any Department, body or agency of the Central Government or a State Government as an Examiner of Electronic Evidence
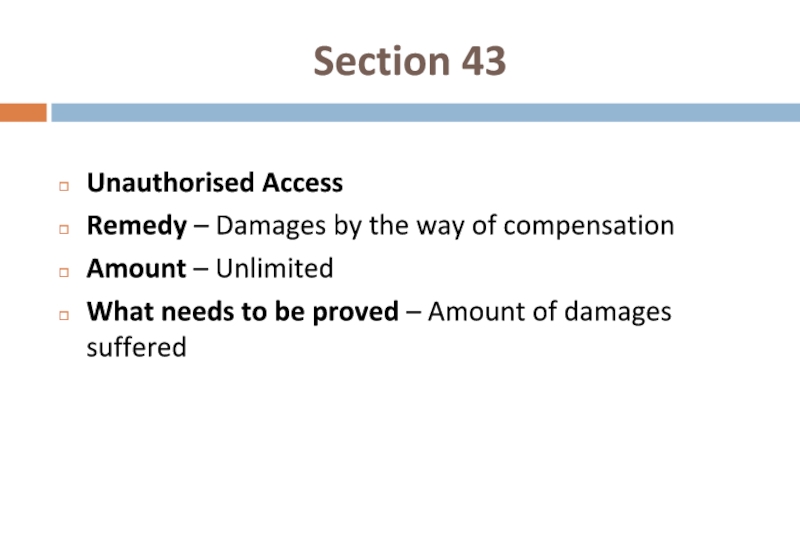
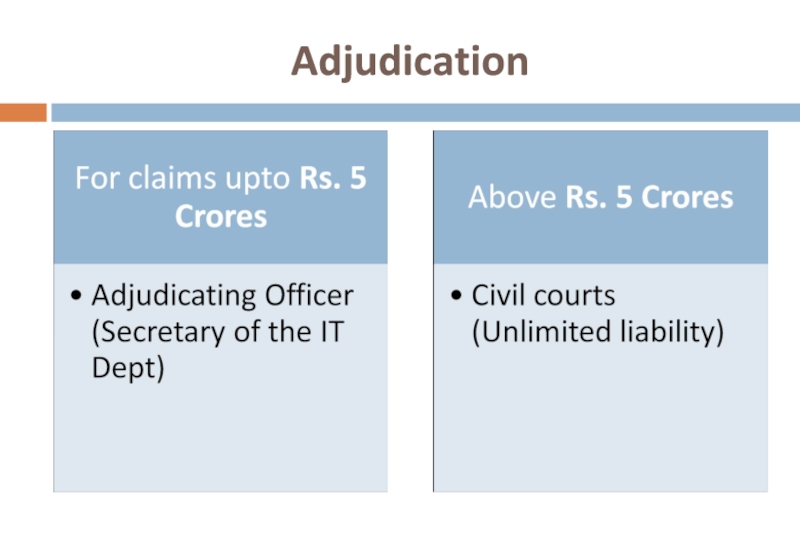
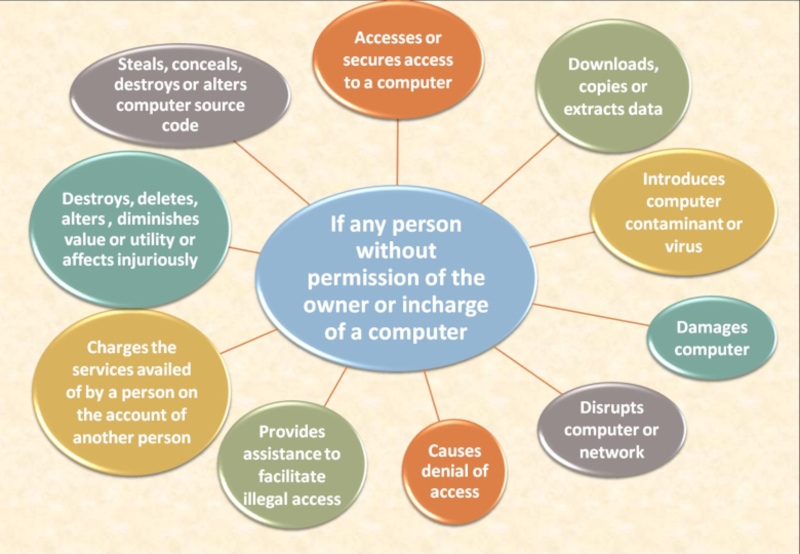
Слайд 34Section 43
Unauthorised Access
Remedy – Damages by the way of compensation
Amount –
What needs to be proved – Amount of damages suffered
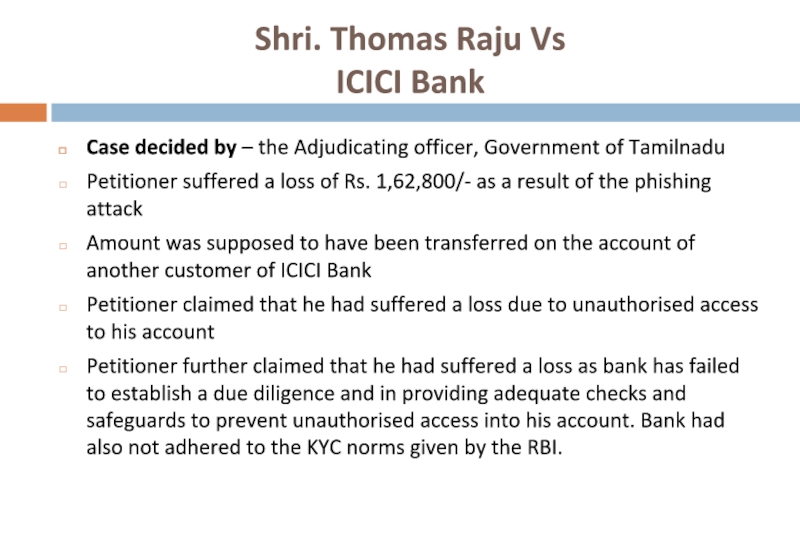
Слайд 37Shri. Thomas Raju Vs
ICICI Bank
Case decided by – the Adjudicating
Petitioner suffered a loss of Rs. 1,62,800/- as a result of the phishing attack
Amount was supposed to have been transferred on the account of another customer of ICICI Bank
Petitioner claimed that he had suffered a loss due to unauthorised access to his account
Petitioner further claimed that he had suffered a loss as bank has failed to establish a due diligence and in providing adequate checks and safeguards to prevent unauthorised access into his account. Bank had also not adhered to the KYC norms given by the RBI.
Слайд 38
Section 66
Removal of definition of “hacking”
Section renamed as Computer related offences
All
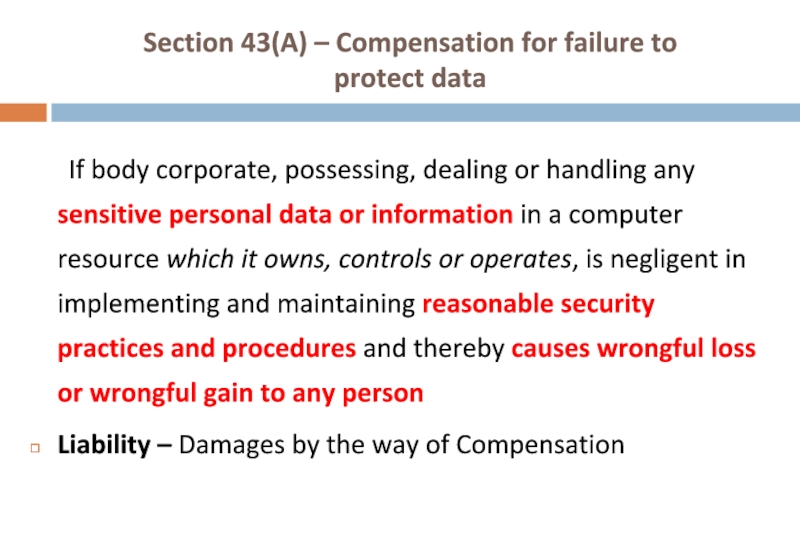
Слайд 39Section 43(A) – Compensation for failure to
protect data
If body corporate, possessing,
Liability – Damages by the way of Compensation
Слайд 40HSBC - Nadeem Kashmiri case
Based on complaints from customers - HSBC
Involvement of Call centre employee (Nadeem Kashmiri)
He was arrested U/Sec. 66 & 72
HSBC also sued Call centre for the loss
Слайд 42Issues
What is Sensitive Personal Information?
What are Reasonable Security Practices and Procedures?
Слайд 43SENSITIVE
PERSONAL
DATA OR INFORMATION
Rule 8 - Information Technology (Reasonable security practices
Слайд 47Collection of Information
Rule 5 - IT (Reasonable security practices and procedures
Слайд 49Privacy and Disclosure of Information policy
Rule 4 - IT (Reasonable security
Слайд 51Disclosure
Rule 6 - IT (Reasonable security practices and procedures and sensitive
Слайд 52Transfer of information
Rule 7 - IT (Reasonable security practices and procedures
Слайд 53Sec 72(A) (Criminal offence)
Punishment for Disclosure of information in breach of
Knowingly or intentionally disclosing “Personal Information" in breach of lawful contract
Imprisonment up to 3 years or fine up to 5 lakh or with both (Cognizable but Bailable)
Слайд 55 Section 66 A
Sending of offensive or false messages
Covers
grossly offensive messages
menacing messages
false information sent for causing annoyance, inconvenience, danger, obstruction, insult, injury, criminal intimidation, enmity, hatred or ill will..
phishing, email spoofing, Spam mails, Threat mails
Punishment – imprisonment upto 3 years and fine
Слайд 56Section 66 B
Dishonestly receiving stolen computer
resource or communication
Covers use of stolen Computers,
mobile phones, SIM Cards, etc
Punishment – imprisonment upto 3 years
and fine
Слайд 57Section 66 C
Identity theft
Fraudulently or dishonestly using someone else’s electronic signature,
Punishment - imprisonment
upto 3 years and fine
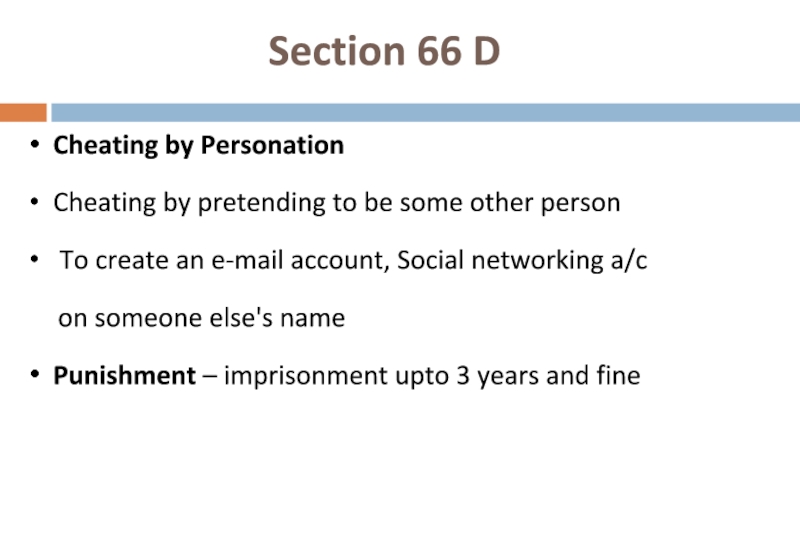
Слайд 58Section 66 D
Cheating by Personation
Cheating by pretending to be some other
To create an e-mail account, Social networking a/c
on someone else's name
Punishment – imprisonment upto 3 years and fine
Слайд 59Investigation Powers
Section 78
Cyber crime cases can now be investigated by Inspector
Earlier such powers were with the “DYSP/ACP”
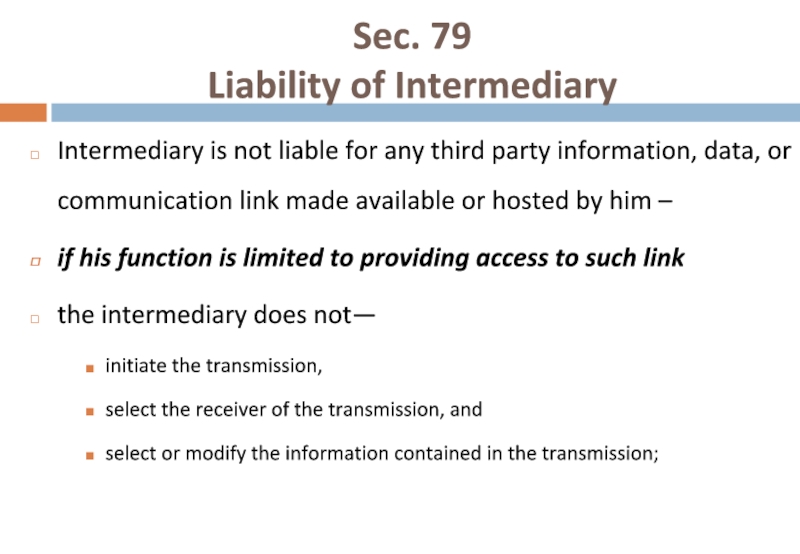
Слайд 60Sec. 79
Liability of Intermediary
Intermediary is not liable for any third
if his function is limited to providing access to such link
the intermediary does not—
initiate the transmission,
select the receiver of the transmission, and
select or modify the information contained in the transmission;
Слайд 61Sec. 79
Liability of Intermediary
Observing due diligence –
The Information Technology (Intermediaries
Слайд 62Compounding of Offences
Section 77 (A)
Compounding – “Out of court settlement”
Offences -
for
has been provided and
Which are not committed against women or children
can be compounded