2013
Vladimir Katalov, ElcomSoft Co. Ltd.
- Главная
- Разное
- Дизайн
- Бизнес и предпринимательство
- Аналитика
- Образование
- Развлечения
- Красота и здоровье
- Финансы
- Государство
- Путешествия
- Спорт
- Недвижимость
- Армия
- Графика
- Культурология
- Еда и кулинария
- Лингвистика
- Английский язык
- Астрономия
- Алгебра
- Биология
- География
- Детские презентации
- Информатика
- История
- Литература
- Маркетинг
- Математика
- Медицина
- Менеджмент
- Музыка
- МХК
- Немецкий язык
- ОБЖ
- Обществознание
- Окружающий мир
- Педагогика
- Русский язык
- Технология
- Физика
- Философия
- Химия
- Шаблоны, картинки для презентаций
- Экология
- Экономика
- Юриспруденция
Cracking and Analyzing Apple iCloud презентация
Содержание
- 1. Cracking and Analyzing Apple iCloud
- 2. The need for iOS forensics More
- 3. iOS data protection Device passcode Protect
- 4. iOS forensics Logical acquisition (iTunes backups) Physical acquisition iCloud backups and storage
- 5. iOS forensics - logical acquisition “Ask”
- 6. iOS forensics - physical acquisition Boot-time exploit
- 7. iOS Data Protection Every iOS device contains
- 8. iOS data protection (cont-d) Content grouped by
- 9. iOS 4+ passcode Passcode is used to
- 10. iOS 4+ passcode (cont-d) Passcode-to-Key transformation
- 11. iOS 4+ passcode (cont-d)
- 12. iOS 5 Keychain SQLite3 DB, all
- 13. iOS 5 Storage Only User partition
- 14. iCloud Introduced in Oct 2011 Introduced
- 15. iCloud services
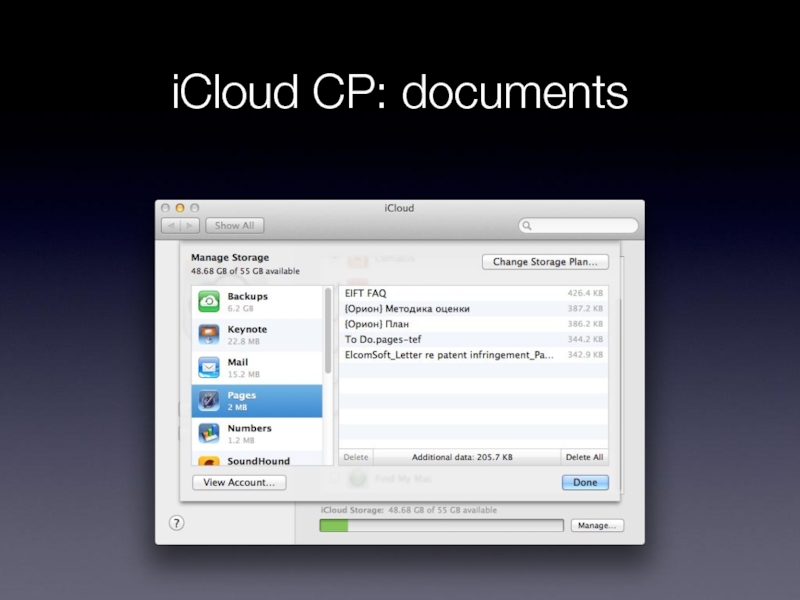
- 16. iCloud Control Panel
- 17. iPhone backup - why?
- 18. Mission: impossible :)
- 19. iCloud backup - what Messages (including iMessages)
- 20. iCloud backup - when Backup runs
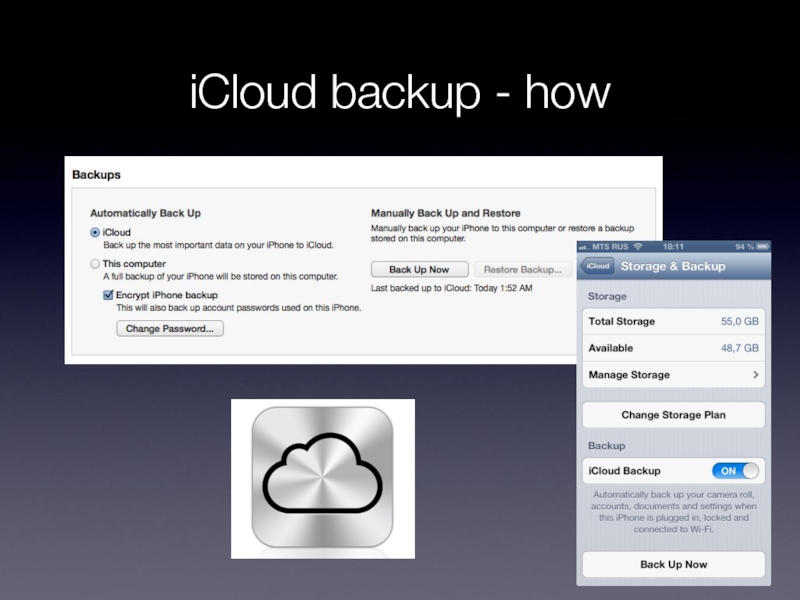
- 21. iCloud backup - how
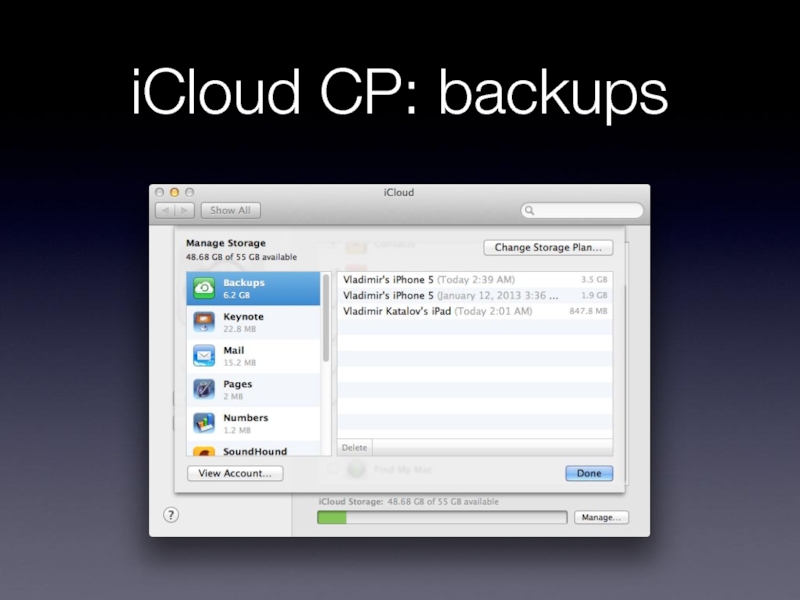
- 22. iCloud CP: backups
- 23. iCloud backup protocol flow Dynamic: endpoints
- 24. iCloud backup protocol flow (cont-d) /mbs/
- 25. iCloud encryption Data stored at 3rd-party storage
- 26. iCloud backups - summary There is
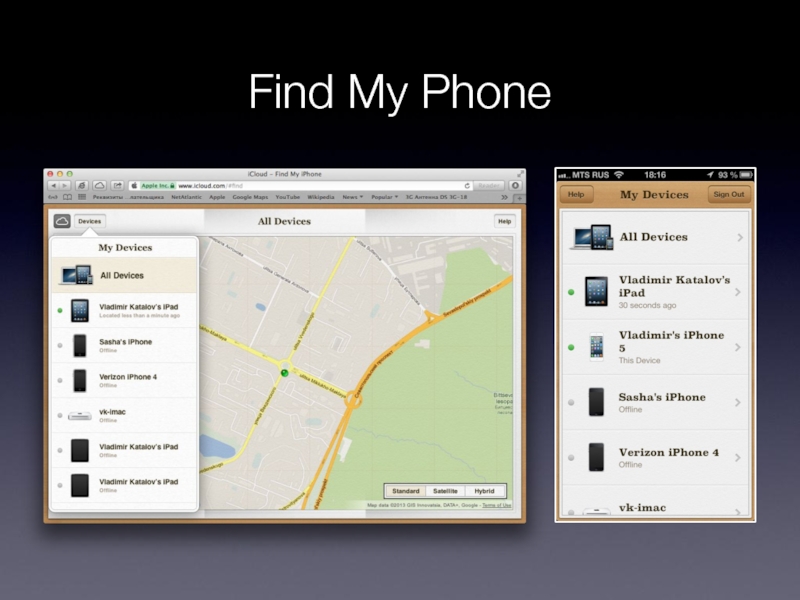
- 27. Find My Phone
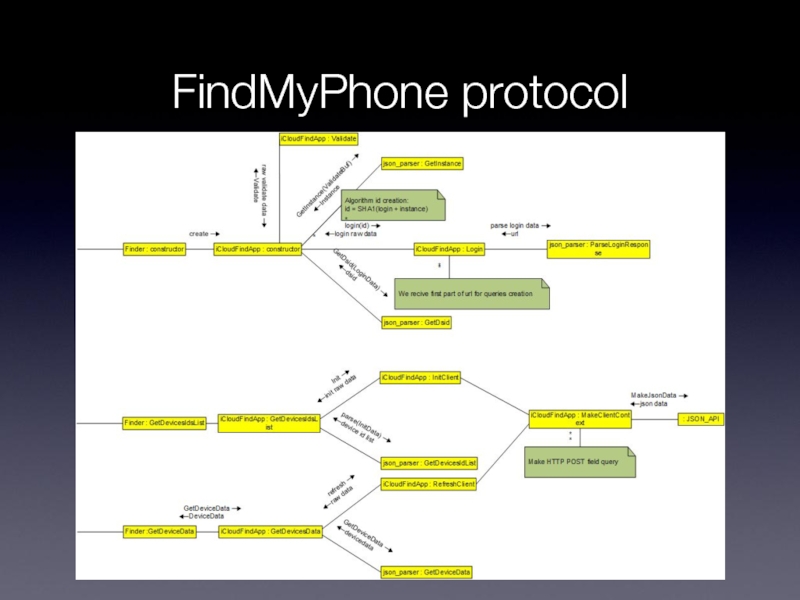
- 28. FindMyPhone protocol
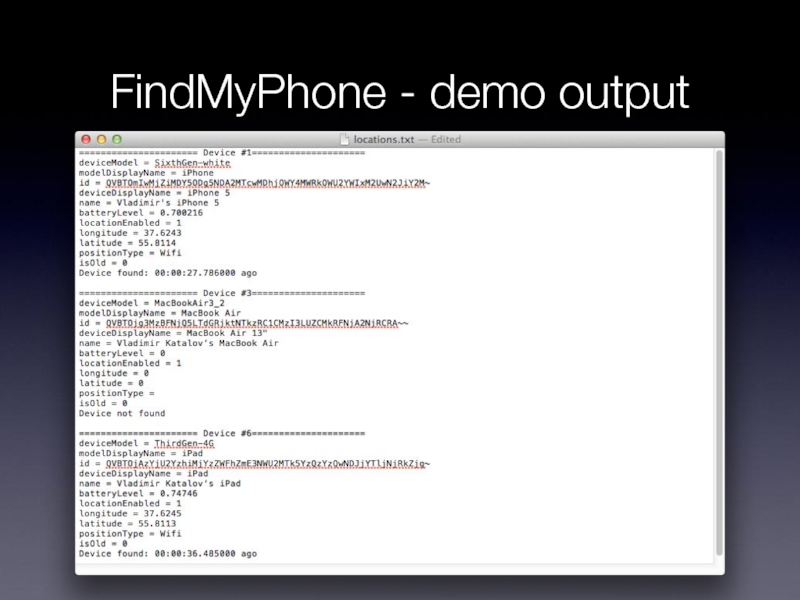
- 29. FindMyPhone - demo output
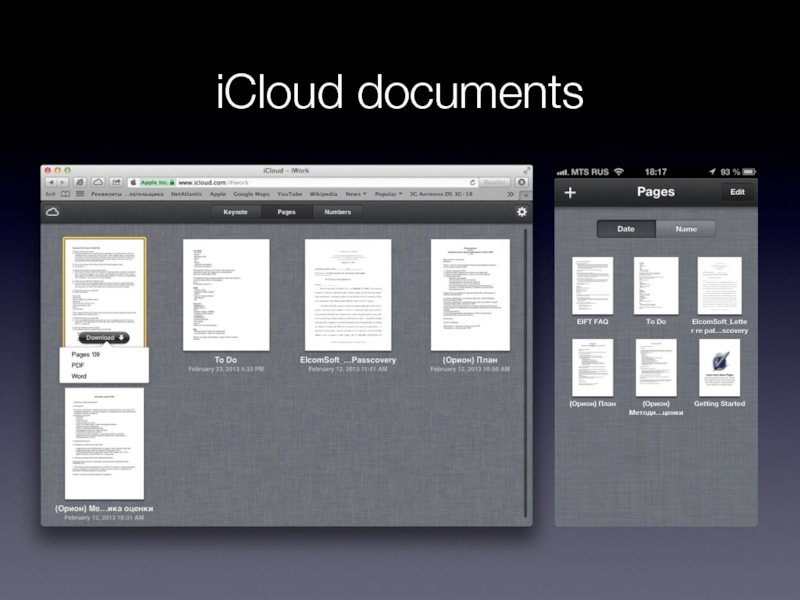
- 30. iCloud documents
- 31. iCloud CP: documents
- 32. Get files from iCloud To get list
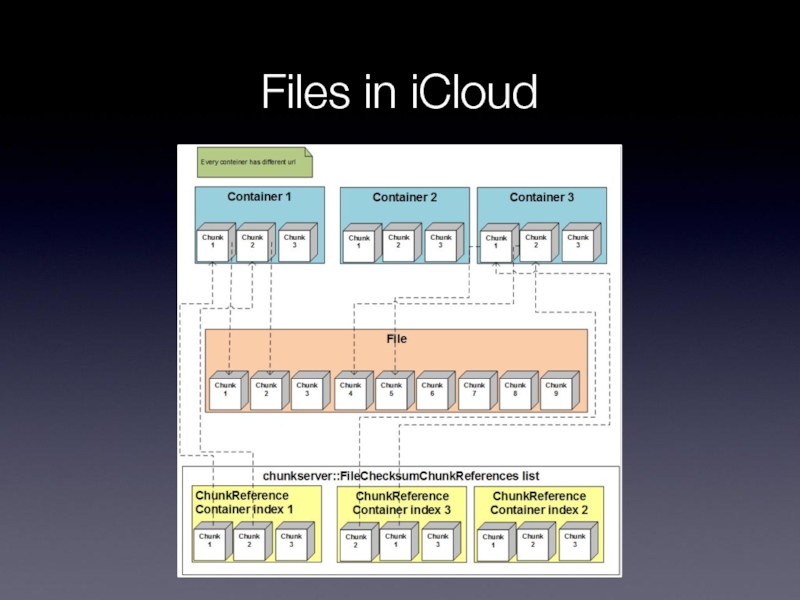
- 33. Files in iCloud
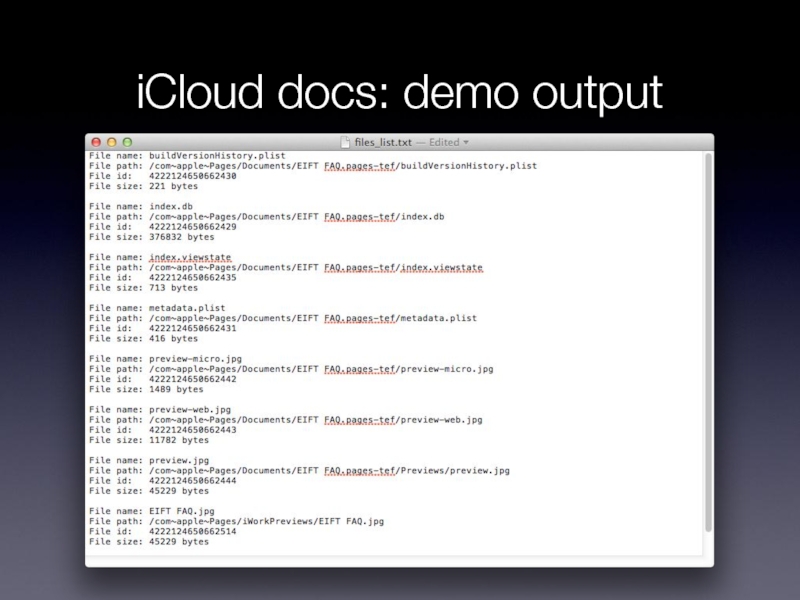
- 35. iCloud docs: demo output
- 36. Possible usage Backups in iCloud near-realtime acquisition
- 37. Conclusion Balance between security, privacy and convenience
- 38. Thank you! Cracking and Analyzing Apple
Слайд 2The need for iOS forensics
More than 5 years on the market
7
iPhones, 5 iPods, 5 iPads
320+ million iPhones, 280+ million iPods, 120+ million iPads sold worldwide
“Smart devices” – they do carry a lot of sensitive data
Corporate deployments are increasing
320+ million iPhones, 280+ million iPods, 120+ million iPads sold worldwide
“Smart devices” – they do carry a lot of sensitive data
Corporate deployments are increasing
Слайд 3iOS data protection
Device passcode
Protect unauthorized access to the device
Bypassing is not
enough (used in encryption)
Disk encryption
Keychain
System-wide storage for sensitive data (keys, passwords etc)
Data is encrypted
Disk encryption
Keychain
System-wide storage for sensitive data (keys, passwords etc)
Data is encrypted
Слайд 4iOS forensics
Logical acquisition (iTunes backups)
Physical acquisition
iCloud backups and storage
Слайд 5iOS forensics
- logical acquisition
“Ask” device to produce backup
Device must be unlocked
(by passcode or iTunes)
Device may produce encrypted backup
Limited amount of information
Device may produce encrypted backup
Limited amount of information
Слайд 6iOS forensics
- physical acquisition
Boot-time exploit to run unsigned code
or
Jailbreak
Device lock state
isn’t relevant, can bruteforce passcode
Can get all information from the device
Can get all information from the device
Слайд 7iOS Data Protection
Every iOS device contains secure AES engine with two
embedded keys:
GID – shared by all devices of same “family”
UID – unique per device
Newer devices have additional UID+ key
There is no known way to extract GID or UID
GID – shared by all devices of same “family”
UID – unique per device
Newer devices have additional UID+ key
There is no known way to extract GID or UID
Слайд 8iOS data protection (cont-d)
Content grouped by accessibility requirements:
Available only when device
is unlocked
Available after first device unlock (and until power off)
Always available
Each protection class has a master key
Master keys are protected by device key and passcode
Protected master keys form system keybag
New keys created during device restore
Available after first device unlock (and until power off)
Always available
Each protection class has a master key
Master keys are protected by device key and passcode
Protected master keys form system keybag
New keys created during device restore
Слайд 9iOS 4+ passcode
Passcode is used to compute passcode key
Computation is tied
to hardware key (UID/UID+)
Same passcode will yield different passcode keys on different devices!
Passcode key is required to unlock most keys from the system keybag
Most files are protected with NSProtectionNone and don’t require a passcode
Most keychain items are protected with ...WhenUnlocked or ...AfterFirstUnlock and require a passcode
Same passcode will yield different passcode keys on different devices!
Passcode key is required to unlock most keys from the system keybag
Most files are protected with NSProtectionNone and don’t require a passcode
Most keychain items are protected with ...WhenUnlocked or ...AfterFirstUnlock and require a passcode
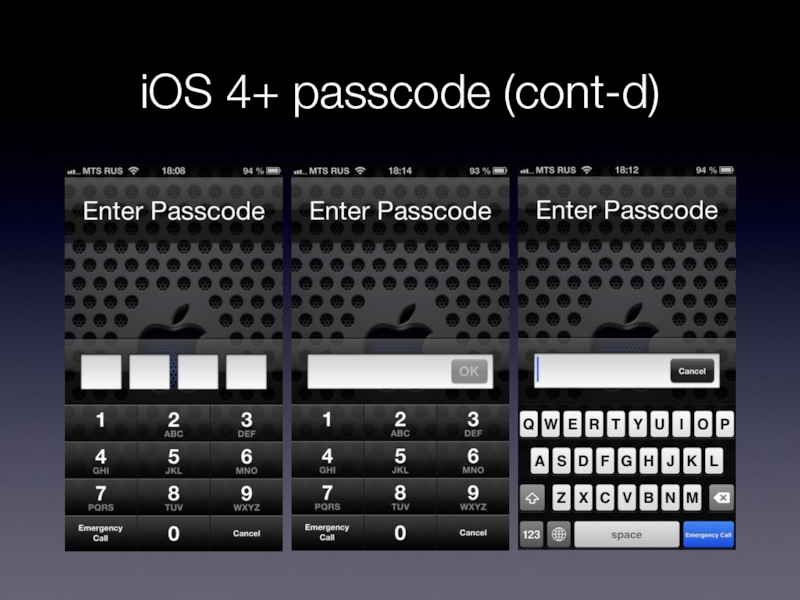
Слайд 10iOS 4+ passcode (cont-d)
Passcode-to-Key transformation is slow
Offline brute-force currently is not
possible
Requires extracting UID/UID+ key
On-device bruteforce is slow
2 p/s on iPhone 3G, 7 p/s on iPad
System keybag contains hint on password complexity
Requires extracting UID/UID+ key
On-device bruteforce is slow
2 p/s on iPhone 3G, 7 p/s on iPad
System keybag contains hint on password complexity
Слайд 12iOS 5 Keychain
SQLite3 DB, all columns are encrypted Available protection classes
kSecAttrAccessibleWhenUnlocked
(+ ...ThisDeviceOnly)
kSecAttrAccessibleAfterFirstUnlock (+ ...ThisDeviceOnly)
kSecAttrAccessibleAlways (+ ...ThisDeviceOnly)
Random key for each item (AES)
Item key is protected with corresponding protection class master key
kSecAttrAccessibleAfterFirstUnlock (+ ...ThisDeviceOnly)
kSecAttrAccessibleAlways (+ ...ThisDeviceOnly)
Random key for each item (AES)
Item key is protected with corresponding protection class master key
Слайд 13iOS 5 Storage
Only User partition is encrypted
Available protection classes:
NSProtectionNone
NSProtectionComplete
NSFileProtectionCompleteUntilFirstUserAuthentication
NSFileProtectionCompleteUnlessOpen
Per-file random encryption
key
File key protected with master key is stored in extended attributes (pretty much like Microsoft EFS)
No protection class - partition key is used
File system metadata and unprotected files
Transparent encryption and decryption (same as pre-iOS 4)
File key protected with master key is stored in extended attributes (pretty much like Microsoft EFS)
No protection class - partition key is used
File system metadata and unprotected files
Transparent encryption and decryption (same as pre-iOS 4)
Слайд 14iCloud
Introduced in Oct 2011
Introduced with iOS 5
Successor to MobileMe, .Mac, iTools
5
GB free storage
Up to 50 GB paid storage
Over 125 million users in April 2012
Up to 50 GB paid storage
Over 125 million users in April 2012
Слайд 19iCloud backup - what
Messages (including iMessages)
Application data
Device settings
Camera roll (photos and
videos)
Visual voicemails
Purchases (music, movies, TV, apps, books)
Home screen arrangement
Ringtones
Visual voicemails
Purchases (music, movies, TV, apps, books)
Home screen arrangement
Ringtones
Слайд 20iCloud backup - when
Backup runs daily when device is:
Connected to the
Internet over Wi-Fi
Connected to a power source
Locked
Can force backup
[Settings] | [iCloud] | [Storage & Backup] | [Back Up Now]
Connected to a power source
Locked
Can force backup
[Settings] | [iCloud] | [Storage & Backup] | [Back Up Now]
Слайд 23iCloud backup protocol flow
Dynamic: endpoints depend on Apple ID
Built on Google
Protocol Buffers (mostly)
Files are split into chunks
Apple provides file-to-chunks mapping, chunk encryption keys, and full request info to 3rd-party storage provider (Amazon/Microsoft)
Encryption key depends on chunk data (deduplication?)
Files are split into chunks
Apple provides file-to-chunks mapping, chunk encryption keys, and full request info to 3rd-party storage provider (Amazon/Microsoft)
Encryption key depends on chunk data (deduplication?)
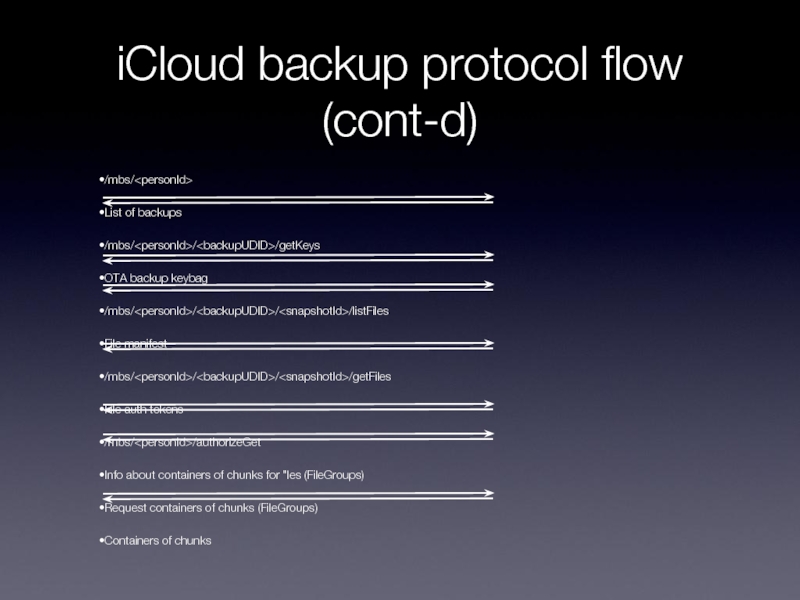
Слайд 24iCloud backup protocol flow (cont-d)
/mbs/
List of backups
/mbs///getKeys
OTA backup keybag
/mbs////listFiles
File manifest
/mbs////getFiles
File auth
tokens
/mbs//authorizeGet
Info about containers of chunks for "les (FileGroups)
Request containers of chunks (FileGroups)
Containers of chunks
/mbs/
Info about containers of chunks for "les (FileGroups)
Request containers of chunks (FileGroups)
Containers of chunks
Слайд 25iCloud encryption
Data stored at 3rd-party storage providers is encrypted
Apple has encryption
keys to that data
Few files are further encrypted using keys from OTA backup keybag
Keychain items are encrypted using keys from OTA backup keybag
Need key 0x835 (securityd) to decrypt most keys from OTA backup keybag
Few files are further encrypted using keys from OTA backup keybag
Keychain items are encrypted using keys from OTA backup keybag
Need key 0x835 (securityd) to decrypt most keys from OTA backup keybag
Слайд 26iCloud backups - summary
There is no user-con"gurable encryption for iCloud backups
iCloud
backups are stored in Microsoft and Amazon clouds in encrypted form
Apple holds encryption keys and thus have access to data in iCloud backups
If Apple stores 0x835 keys then it can also have access to Keychain data (i.e. passwords)
Apple may have legal obligations to do this (e.g. LE)
Apple holds encryption keys and thus have access to data in iCloud backups
If Apple stores 0x835 keys then it can also have access to Keychain data (i.e. passwords)
Apple may have legal obligations to do this (e.g. LE)
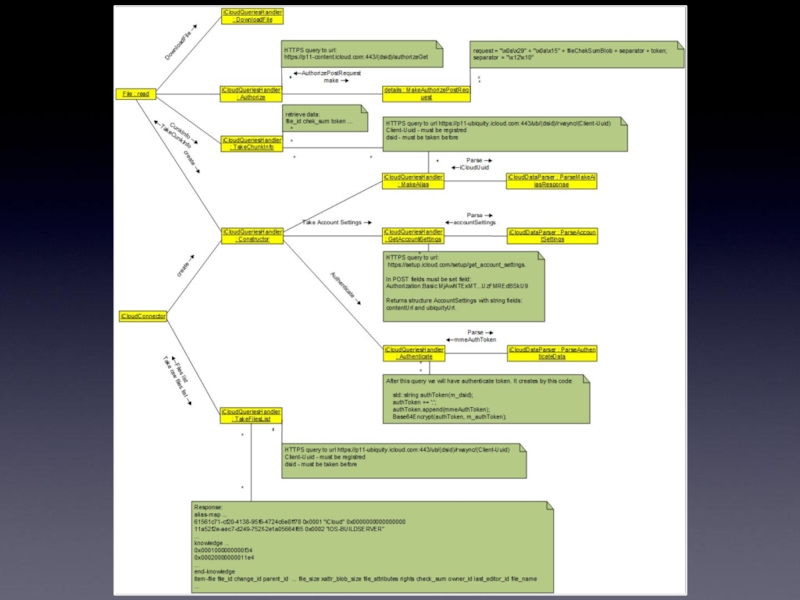
Слайд 32Get files from iCloud
To get list of files
Authentication request (with given
AppleID & password). Client gets mmeAuthToken in return; which, in order, is used to create authentication token (together with dsid). dsid (Destination Signaling IDentifier) is an unique ID assigned to the user when registering at iCloud.com.
Request to get AccountSettings. Client gets an URL (ubiquityUrl) with an address to get UUID (unique user identifier), file list, info on file tokens and for authorization.
Request to get file list (POST). Output (for every file):
file name
file id
parent folder id
last change time
checksum
access rights
To download given file
Request to get file token (using file id, checksum and aliasMap).
Authorization request. Returns information on file chunks and containers. Output: container list (with URLs) and chunk information.
Request to get AccountSettings. Client gets an URL (ubiquityUrl) with an address to get UUID (unique user identifier), file list, info on file tokens and for authorization.
Request to get file list (POST). Output (for every file):
file name
file id
parent folder id
last change time
checksum
access rights
To download given file
Request to get file token (using file id, checksum and aliasMap).
Authorization request. Returns information on file chunks and containers. Output: container list (with URLs) and chunk information.
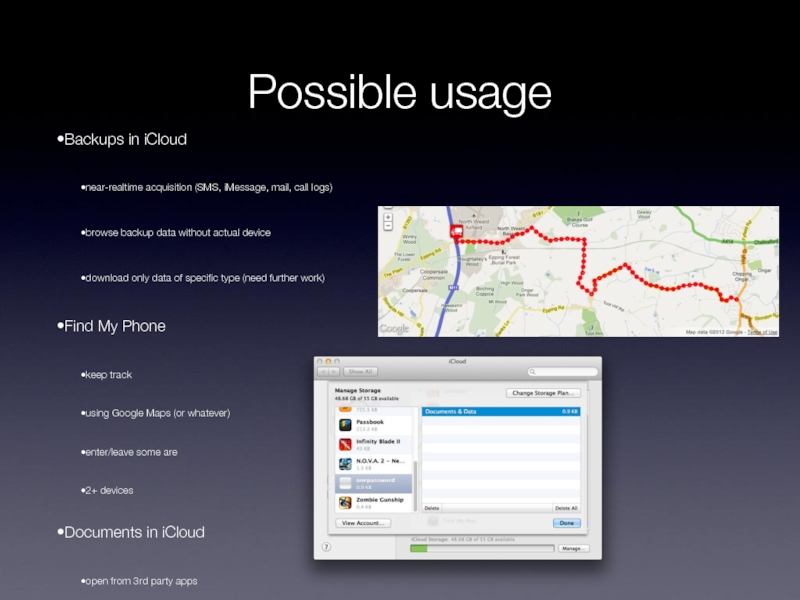
Слайд 36Possible usage
Backups in iCloud
near-realtime acquisition (SMS, iMessage, mail, call logs)
browse backup
data without actual device
download only data of specific type (need further work)
Find My Phone
keep track
using Google Maps (or whatever)
enter/leave some are
2+ devices
Documents in iCloud
open from 3rd party apps
track changes
download unsupported document data
Forensics!
download only data of specific type (need further work)
Find My Phone
keep track
using Google Maps (or whatever)
enter/leave some are
2+ devices
Documents in iCloud
open from 3rd party apps
track changes
download unsupported document data
Forensics!
Слайд 37Conclusion
Balance between security, privacy and convenience
iCloud security risks
Use additional encryption
Need further
work (contacts, calendar, mode documents, converting documents, partial backup download, decrypting keychain, photo stream, 3rd party apps data: 1Password etc)
Слайд 38Thank you!
Cracking and Analyzing Apple iCloud backups, Find My iPhone, Document
Storage
CanSecWest 2013
Vladimir Katalov, ElcomSoft Co. Ltd.
http://www.elcomsoft.com
http://blog.crackpassword.com
Facebook: ElcomSoft
Twitter: @elcomsoft