- Главная
- Разное
- Дизайн
- Бизнес и предпринимательство
- Аналитика
- Образование
- Развлечения
- Красота и здоровье
- Финансы
- Государство
- Путешествия
- Спорт
- Недвижимость
- Армия
- Графика
- Культурология
- Еда и кулинария
- Лингвистика
- Английский язык
- Астрономия
- Алгебра
- Биология
- География
- Детские презентации
- Информатика
- История
- Литература
- Маркетинг
- Математика
- Медицина
- Менеджмент
- Музыка
- МХК
- Немецкий язык
- ОБЖ
- Обществознание
- Окружающий мир
- Педагогика
- Русский язык
- Технология
- Физика
- Философия
- Химия
- Шаблоны, картинки для презентаций
- Экология
- Экономика
- Юриспруденция
INSIDER THREAT KILL CHAIN презентация
Содержание
- 1. INSIDER THREAT KILL CHAIN
- 2. INSIDER THREAT KILL CHAIN DETECTING HUMAN INDICATORS OF COMPROMISE Ken Westin Product Marketing Manager kwestin@tripwire.com
- 3. Your organization’s greatest asset is also its greatest threat. People.
- 4. MY FIRST EXPERIENCE WITH TRIPWIRE ADMINISTRATOR BREAKING BAD
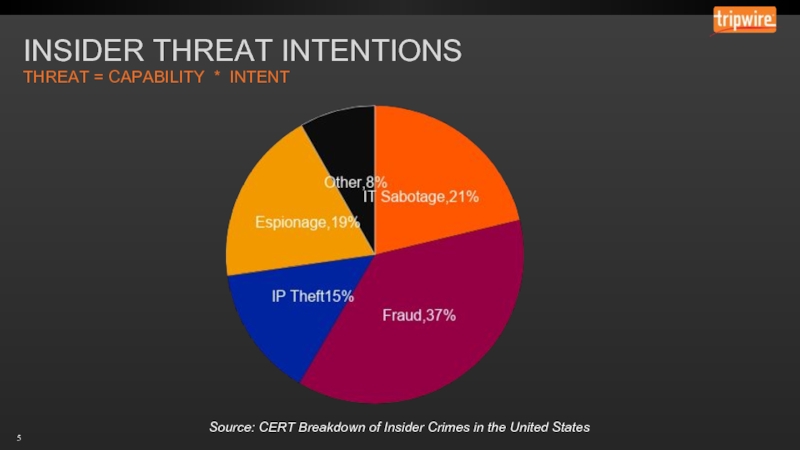
- 5. INSIDER THREAT INTENTIONS THREAT = CAPABILITY *
- 6. IT Contractor fired for but allowed to
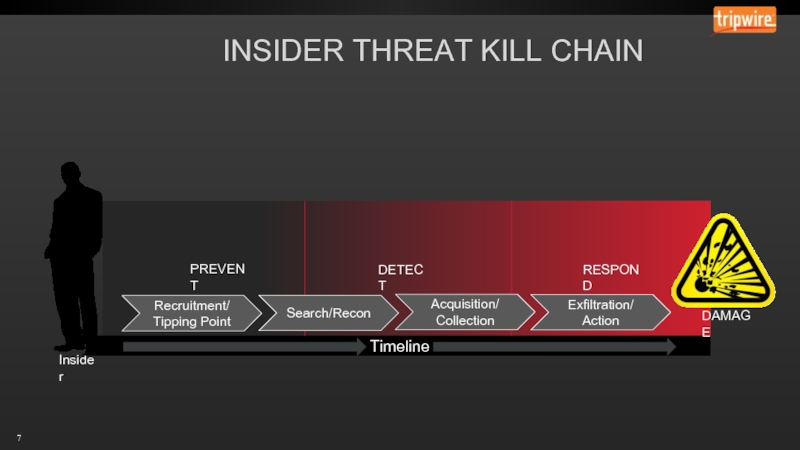
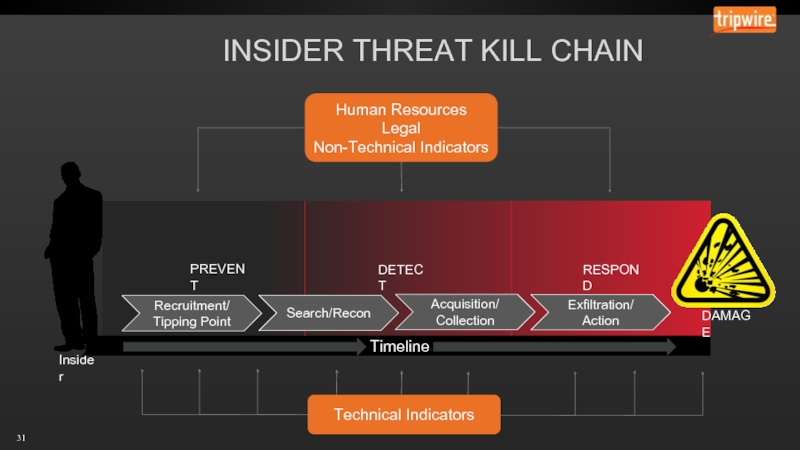
- 7. INSIDER THREAT KILL CHAIN Insider Timeline
- 8. INSIDER THREAT KILL CHAIN Insider Timeline
- 9. INSIDER THREAT KILL CHAIN Insider Timeline
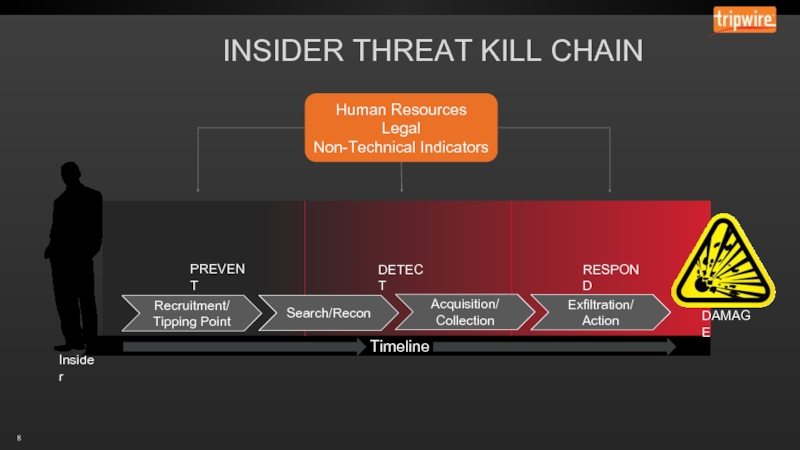
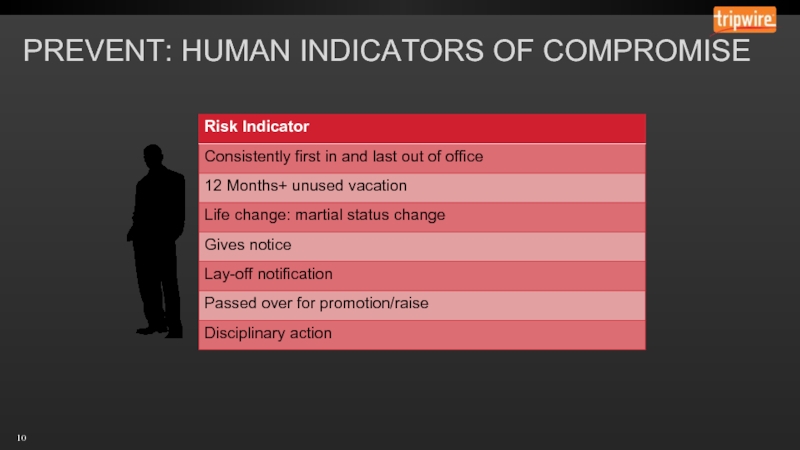
- 10. PREVENT: HUMAN INDICATORS OF COMPROMISE
- 11. PREVENT Consider threats from insiders and partners
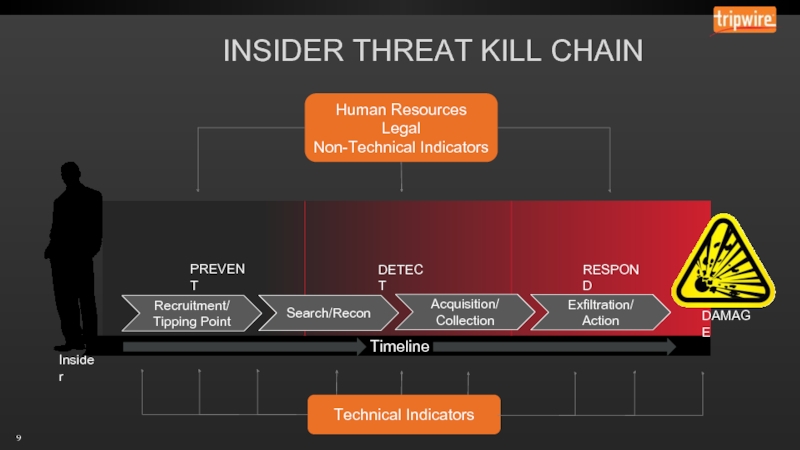
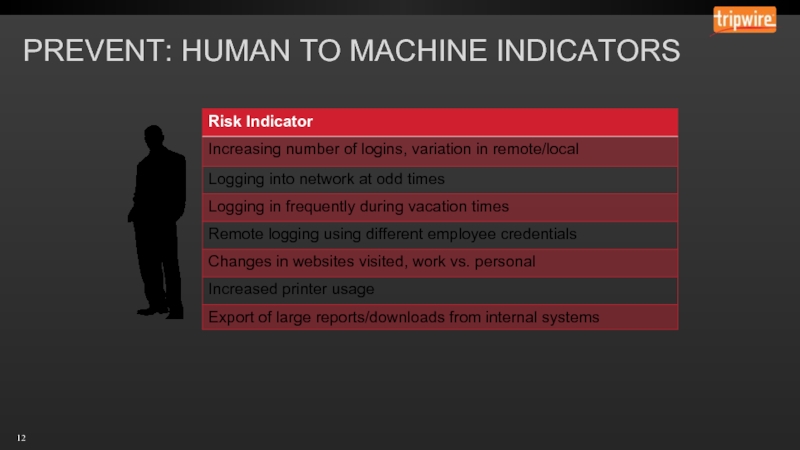
- 12. PREVENT: HUMAN TO MACHINE INDICATORS
- 13. PREVENT & DETECT Implement strict password
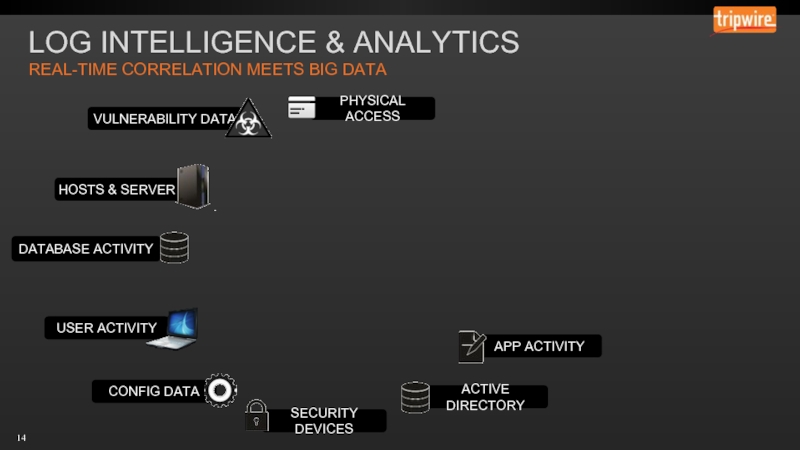
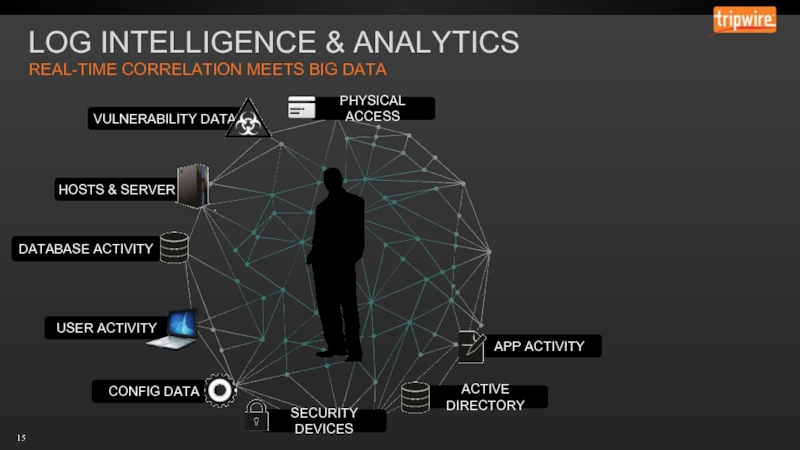
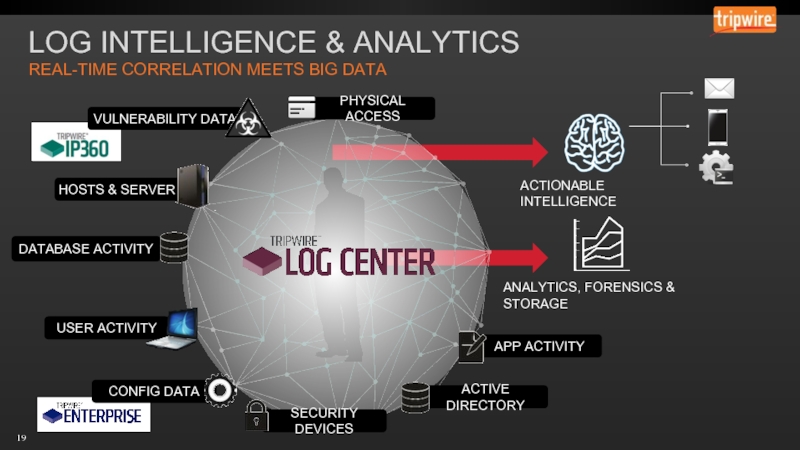
- 14. LOG INTELLIGENCE & ANALYTICS REAL-TIME CORRELATION MEETS BIG DATA
- 15. LOG INTELLIGENCE & ANALYTICS REAL-TIME CORRELATION MEETS BIG DATA
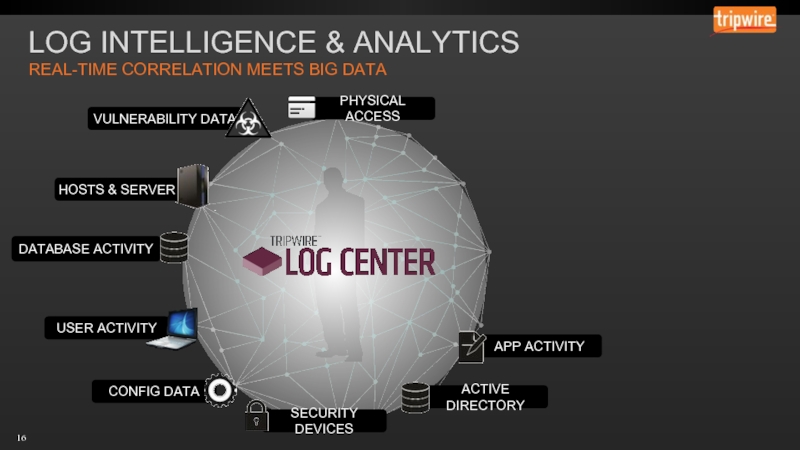
- 16. LOG INTELLIGENCE & ANALYTICS REAL-TIME CORRELATION MEETS BIG DATA
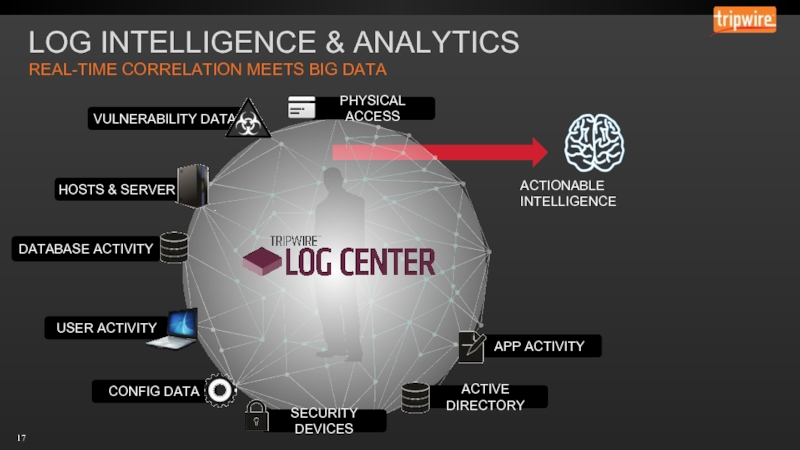
- 17. LOG INTELLIGENCE & ANALYTICS REAL-TIME CORRELATION MEETS BIG DATA
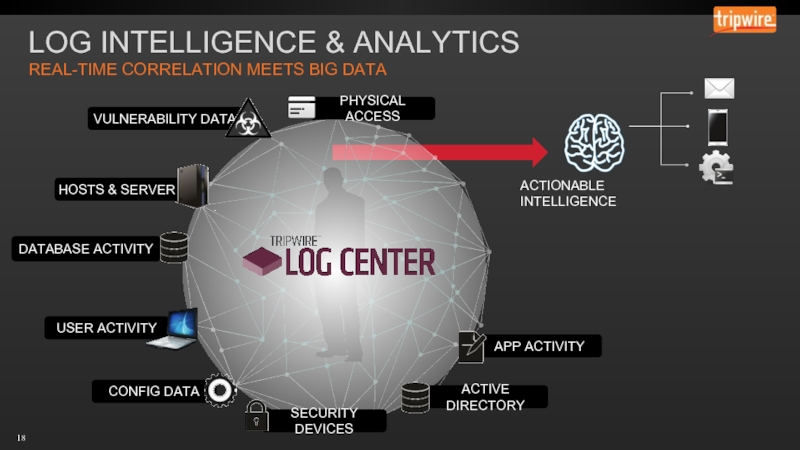
- 18. LOG INTELLIGENCE & ANALYTICS REAL-TIME CORRELATION MEETS BIG DATA
- 19. LOG INTELLIGENCE & ANALYTICS REAL-TIME CORRELATION MEETS BIG DATA
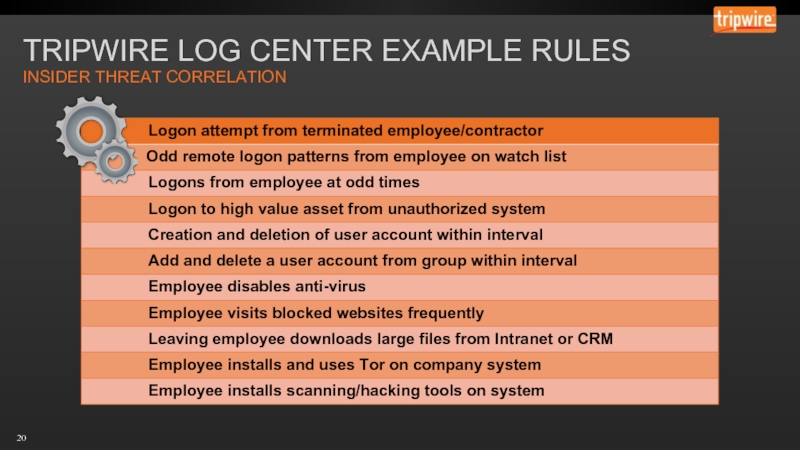
- 20. INSIDER THREAT CORRELATION TRIPWIRE LOG CENTER EXAMPLE RULES
- 21. WHAT TO LOG? Firewall logs Unsuccessful login
- 22. ALL LOGS CONSIDERED Determine log volume: Identify
- 23. LOGGING REAL PROBLEMS Employee behavior shows potential
- 24. LOGGING REAL PROBLEMS Employee behavior shows potential
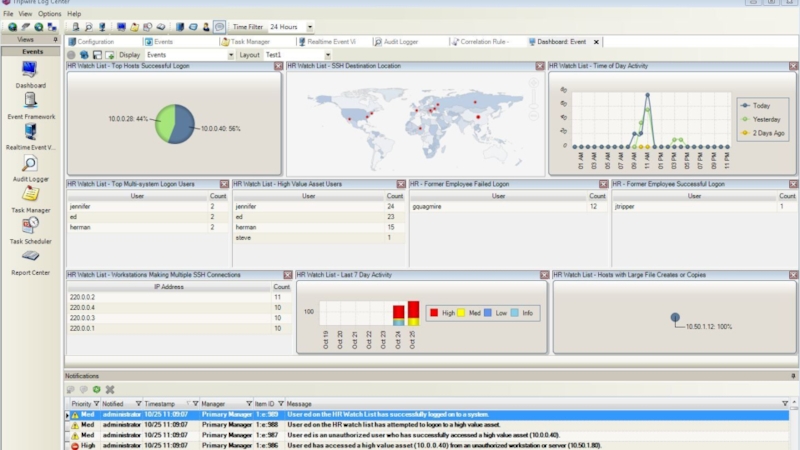
- 25. Tripwire Log Center Dashboard
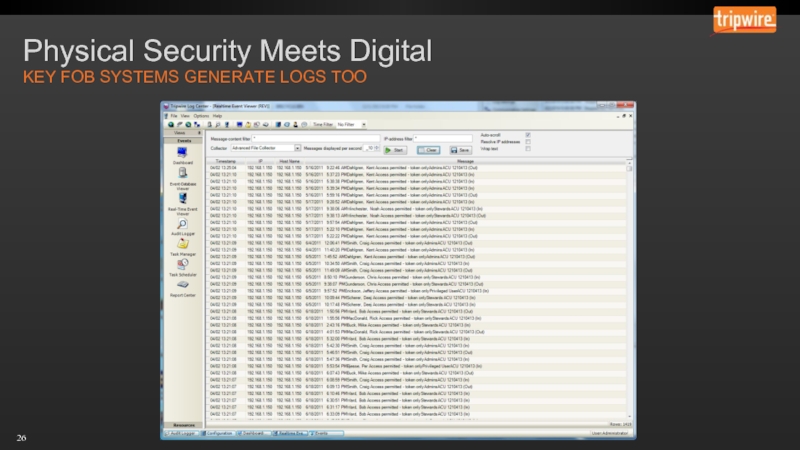
- 26. Physical Security Meets Digital KEY FOB SYSTEMS GENERATE LOGS TOO
- 27. CUSTOMER STORY: POWER COMPANY Deployment Tripwire Log
- 28. CUSTOMER STORY: DON’T TREAD ON ME Deployed
- 29. RESPOND Implement secure backup and recovery processes
- 30. I’m On A Boat! Network Admin Hacked Navy—While on an Aircraft Carrier http://www.wired.com/2014/05/navy-sysadmin-hacking/
- 31. INSIDER THREAT KILL CHAIN Insider Timeline
- 32. Questions? Ken Westin kwestin@tripwire.com Twitter: @kwestin
Слайд 2INSIDER THREAT KILL CHAIN
DETECTING HUMAN INDICATORS OF COMPROMISE
Ken Westin
Product Marketing Manager
kwestin@tripwire.com
Слайд 5INSIDER THREAT INTENTIONS
THREAT = CAPABILITY * INTENT
Source: CERT Breakdown of Insider
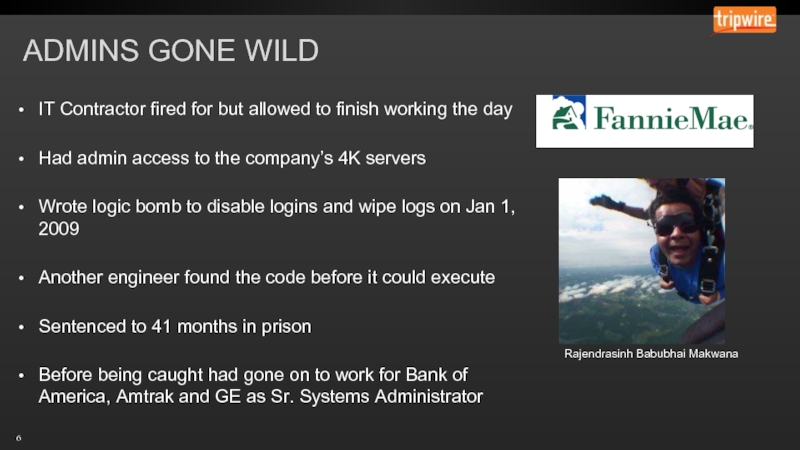
Слайд 6IT Contractor fired for but allowed to finish working the day
Had
Wrote logic bomb to disable logins and wipe logs on Jan 1, 2009
Another engineer found the code before it could execute
Sentenced to 41 months in prison
Before being caught had gone on to work for Bank of America, Amtrak and GE as Sr. Systems Administrator
Rajendrasinh Babubhai Makwana
ADMINS GONE WILD
Слайд 11PREVENT
Consider threats from insiders and partners in risk assessments
Background checks
Clearly document
Periodic security awareness training for all employees
Monitor and respond to suspicious or disruptive behavior
Anticipate and manage negative workplace issues
Track and secure physical environment
Establish clear lines of communication and procedures between HR, Legal and IT
AWARENESS & TRAINING
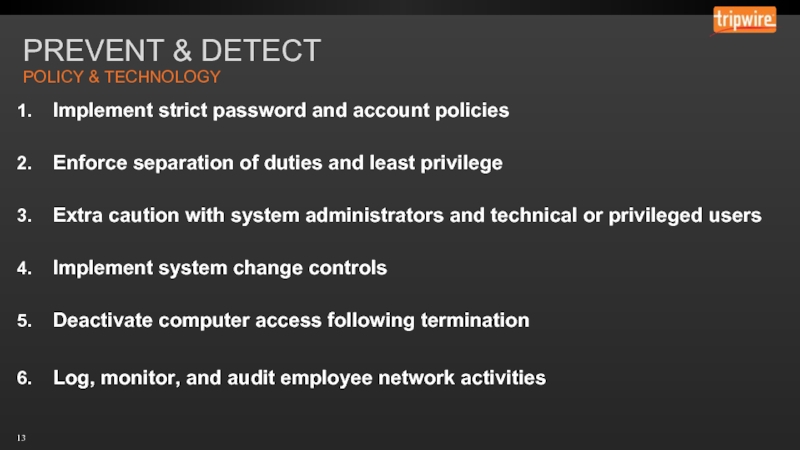
Слайд 13PREVENT & DETECT
Implement strict password and account policies
Enforce separation
Extra caution with system administrators and technical or privileged users
Implement system change controls
Deactivate computer access following termination
Log, monitor, and audit employee network activities
POLICY & TECHNOLOGY
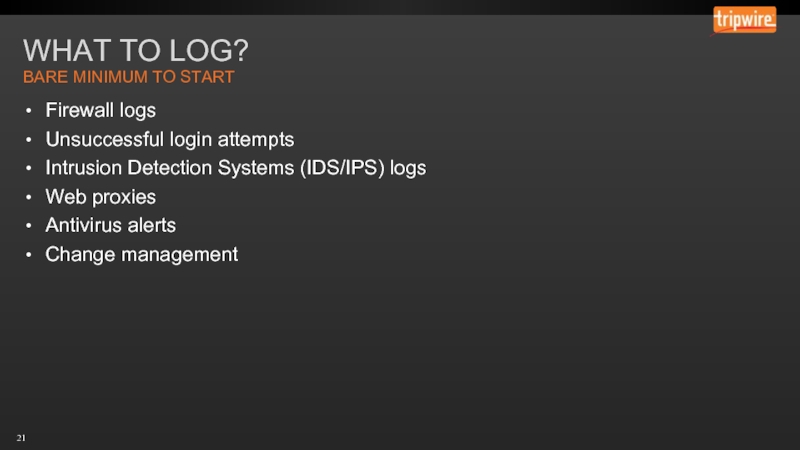
Слайд 21WHAT TO LOG?
Firewall logs
Unsuccessful login attempts
Intrusion Detection Systems (IDS/IPS) logs
Web proxies
Antivirus
Change management
BARE MINIMUM TO START
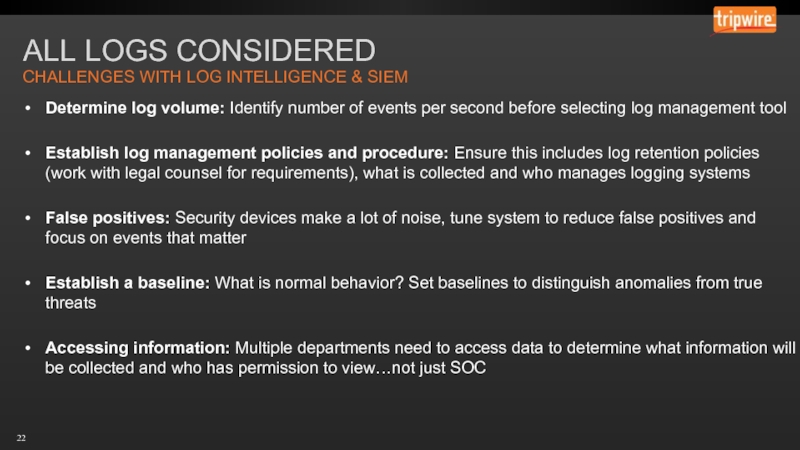
Слайд 22ALL LOGS CONSIDERED
Determine log volume: Identify number of events per second
Establish log management policies and procedure: Ensure this includes log retention policies (work with legal counsel for requirements), what is collected and who manages logging systems
False positives: Security devices make a lot of noise, tune system to reduce false positives and focus on events that matter
Establish a baseline: What is normal behavior? Set baselines to distinguish anomalies from true threats
Accessing information: Multiple departments need to access data to determine what information will be collected and who has permission to view…not just SOC
CHALLENGES WITH LOG INTELLIGENCE & SIEM
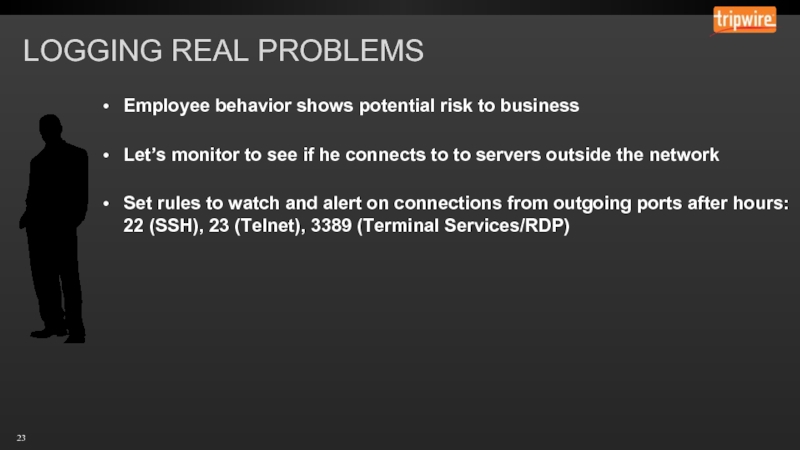
Слайд 23LOGGING REAL PROBLEMS
Employee behavior shows potential risk to business
Let’s monitor to
Set rules to watch and alert on connections from outgoing ports after hours: 22 (SSH), 23 (Telnet), 3389 (Terminal Services/RDP)
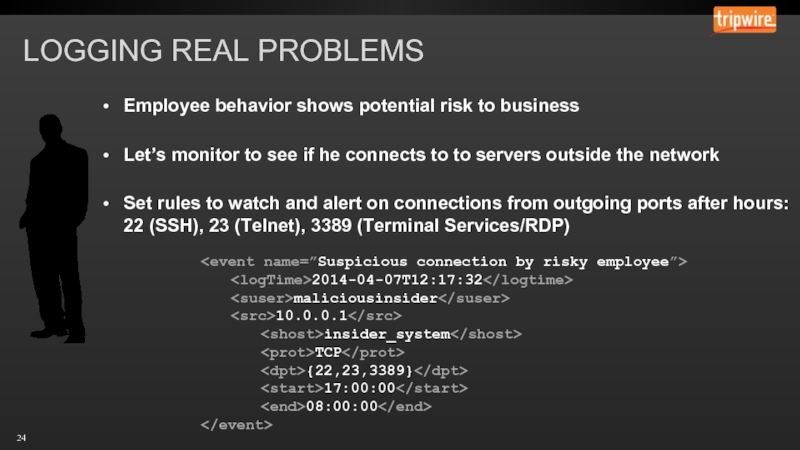
Слайд 24LOGGING REAL PROBLEMS
Employee behavior shows potential risk to business
Let’s monitor to
Set rules to watch and alert on connections from outgoing ports after hours: 22 (SSH), 23 (Telnet), 3389 (Terminal Services/RDP)
Слайд 27CUSTOMER STORY: POWER COMPANY
Deployment Tripwire Log Center immediately discovered account of
Account was logging into network at 4AM on a Wednesday
Also discovered logging disabled on key firewall
MALICIOUS INSIDERS UNVEILED
Слайд 28CUSTOMER STORY: DON’T TREAD ON ME
Deployed PoC of Tripwire Log Center
Discovered backdoor setup by terminated employee that was actively being accessed
MALICIOUS INSIDERS UNVEILED
Слайд 29RESPOND
Implement secure backup and recovery processes
Quickly audit user’s network behavior
Develop
Слайд 30I’m On A Boat!
Network Admin Hacked Navy—While on an Aircraft
http://www.wired.com/2014/05/navy-sysadmin-hacking/