- Главная
- Разное
- Дизайн
- Бизнес и предпринимательство
- Аналитика
- Образование
- Развлечения
- Красота и здоровье
- Финансы
- Государство
- Путешествия
- Спорт
- Недвижимость
- Армия
- Графика
- Культурология
- Еда и кулинария
- Лингвистика
- Английский язык
- Астрономия
- Алгебра
- Биология
- География
- Детские презентации
- Информатика
- История
- Литература
- Маркетинг
- Математика
- Медицина
- Менеджмент
- Музыка
- МХК
- Немецкий язык
- ОБЖ
- Обществознание
- Окружающий мир
- Педагогика
- Русский язык
- Технология
- Физика
- Философия
- Химия
- Шаблоны, картинки для презентаций
- Экология
- Экономика
- Юриспруденция
2011 Cyber Security & Social Technology презентация
Содержание
- 1. 2011 Cyber Security & Social Technology
- 2. Donald E. Hester CISSP, CISA, CAP, MCT,
- 3. Rev2/28/2011 © 2011 Maze & Associates
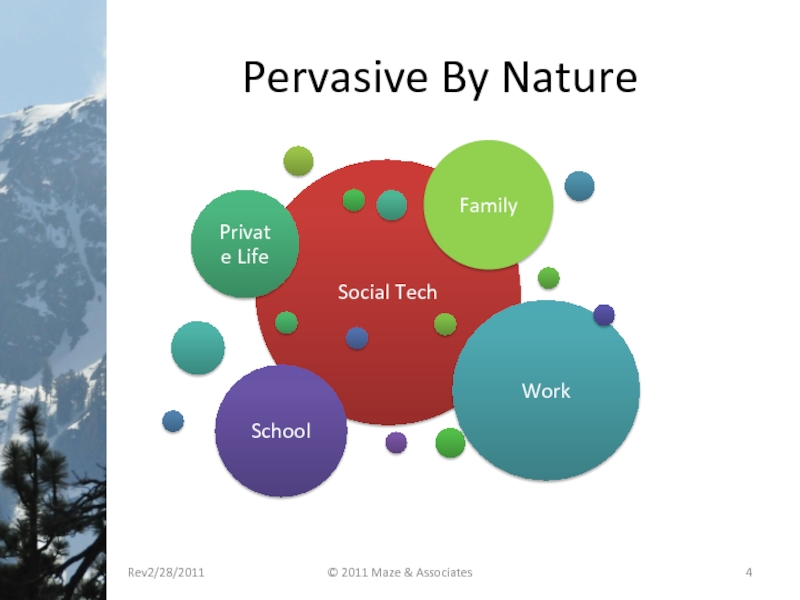
- 4. Pervasive By Nature Rev2/28/2011 © 2011 Maze & Associates
- 5. Social Tech Issues Rev2/28/2011 © 2011 Maze & Associates
- 6. MARKETING & BRANDING USES Rev2/28/2011 © 2011 Maze & Associates
- 7. Brand Protection - Concerns Fear of losing
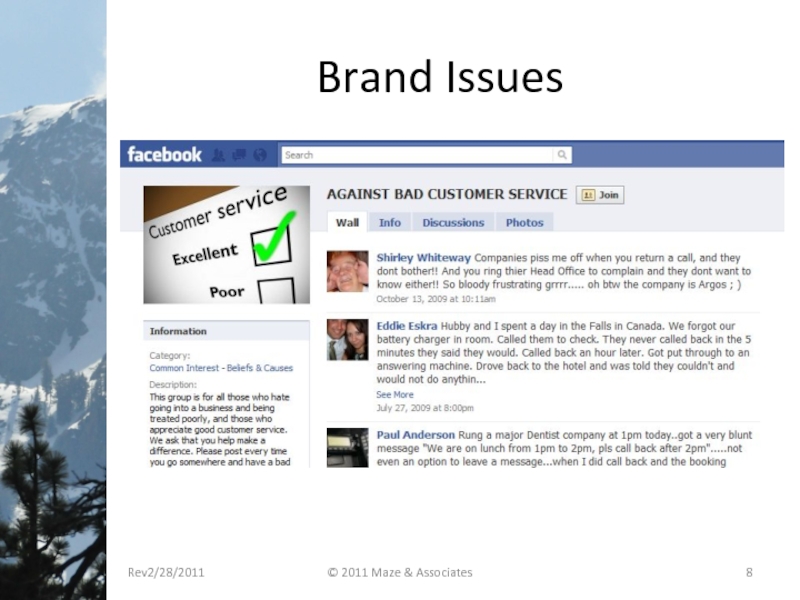
- 8. Brand Issues Rev2/28/2011 © 2011 Maze & Associates
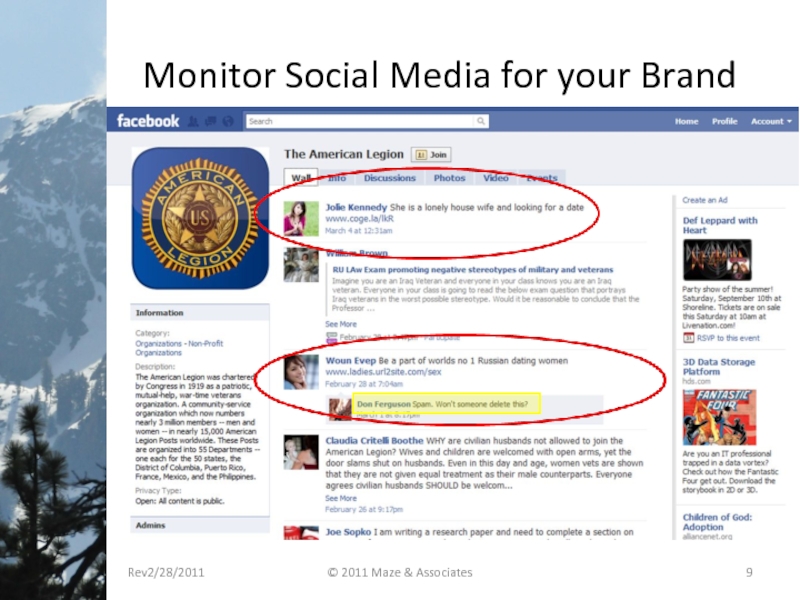
- 9. Monitor Social Media for your Brand Rev2/28/2011 © 2011 Maze & Associates
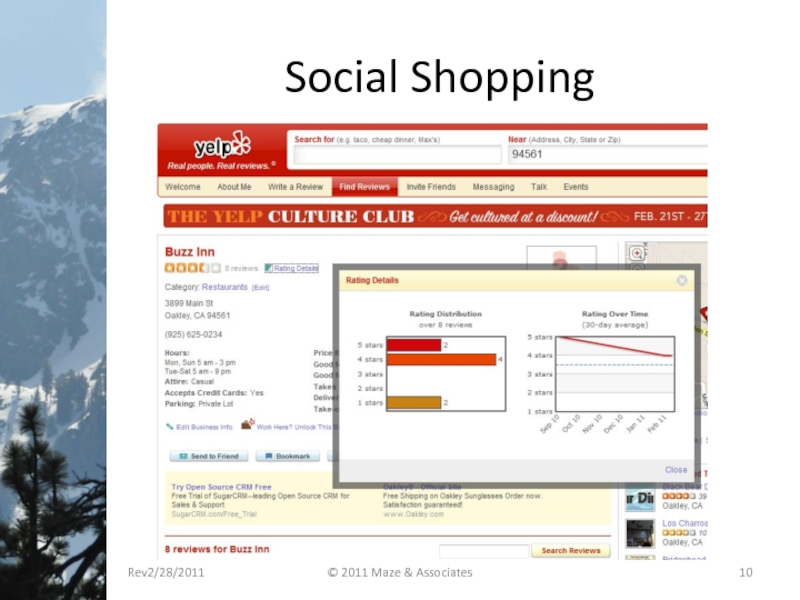
- 10. Social Shopping Rev2/28/2011 © 2011 Maze & Associates
- 11. How to get started Social Technology The
- 12. Marketing Manger's Guide to Social Media
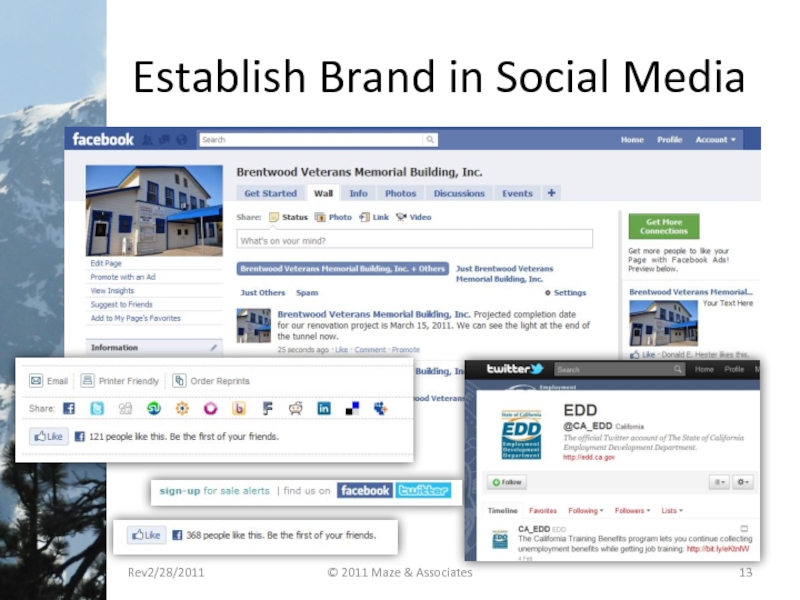
- 13. Establish Brand in Social Media Rev2/28/2011 © 2011 Maze & Associates
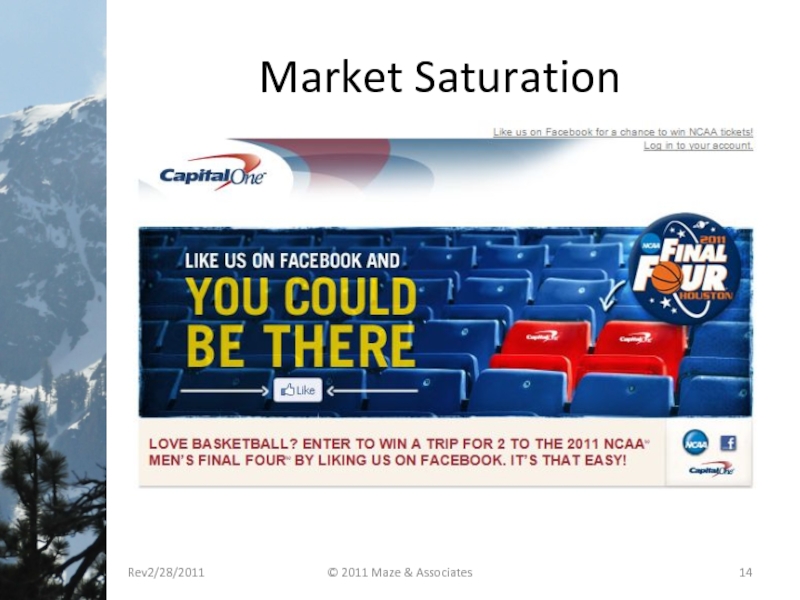
- 14. Market Saturation Rev2/28/2011 © 2011 Maze & Associates
- 15. Integration Rev2/28/2011 © 2011 Maze & Associates
- 16. Deceptive Marketing Rev2/28/2011 © 2011 Maze & Associates
- 17. Endorsements If you are being paid to
- 18. HUMAN RESOURCES USES Rev2/28/2011 © 2011 Maze & Associates
- 19. Social Media Uses in HR The use
- 20. http://www.ajc.com/news/barrow-teacher-fired-over-733625.html Rev2/28/2011 © 2011 Maze & Associates
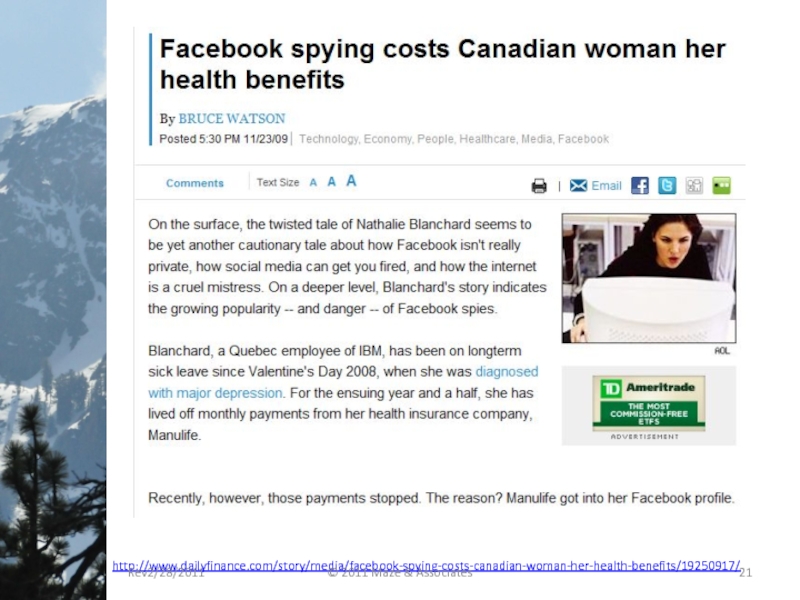
- 21. http://www.dailyfinance.com/story/media/facebook-spying-costs-canadian-woman-her-health-benefits/19250917/ Rev2/28/2011 © 2011 Maze & Associates
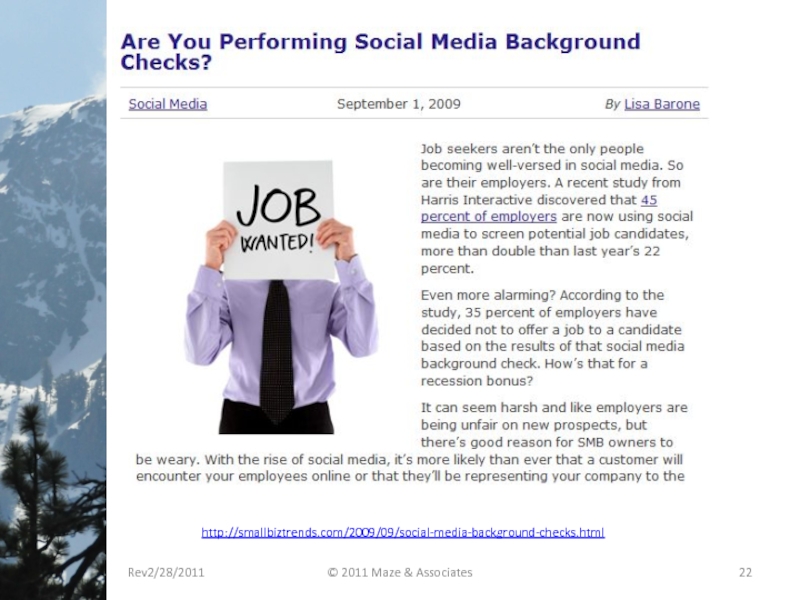
- 22. Rev2/28/2011 © 2011 Maze & Associates http://smallbiztrends.com/2009/09/social-media-background-checks.html
- 23. Horns of a dilemma If employers use
- 24. Horns of a dilemma If employers don’t
- 25. Use of Social Media at Work Does
- 26. PERSONAL USES Rev2/28/2011 © 2011 Maze & Associates
- 27. Computer Security: Malware Rev2/28/2011 © 2011 Maze & Associates
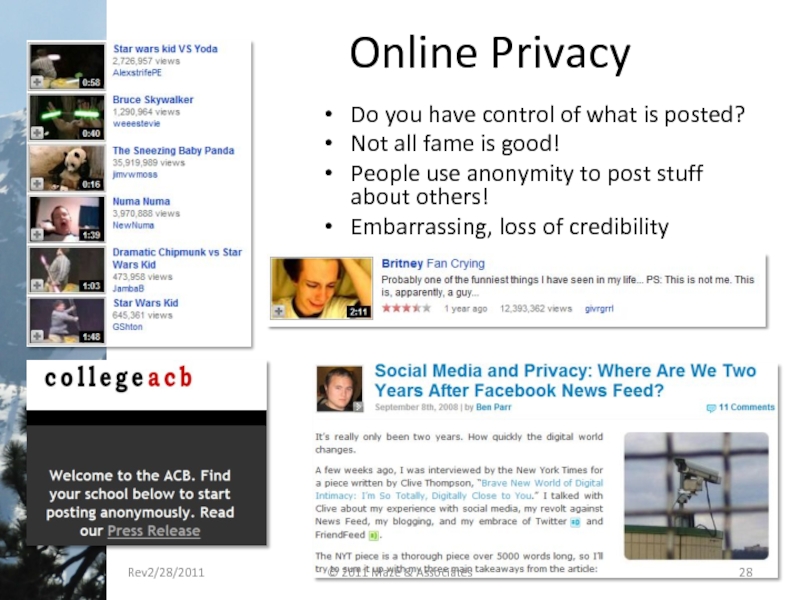
- 28. Online Privacy Do you have control of
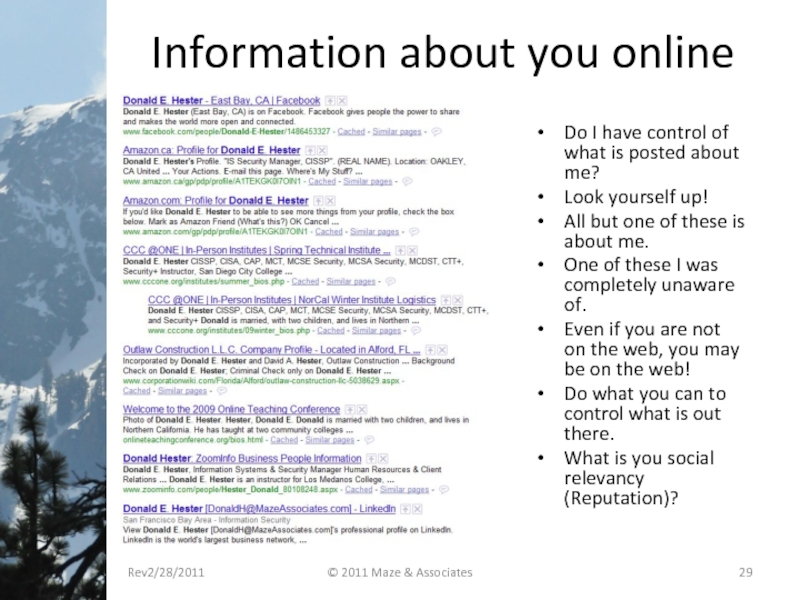
- 29. Information about you online Do I have
- 30. Sony Play Station Network Breach Rev2/28/2011 © 2011 Maze & Associates
- 31. SOCIAL MEDIA & POLITICS Rev2/28/2011 © 2011 Maze & Associates
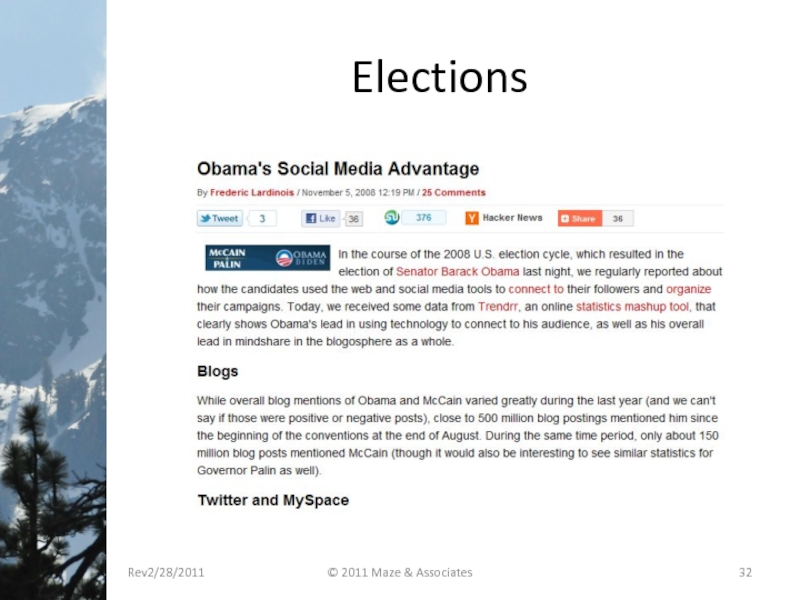
- 32. Elections Rev2/28/2011 © 2011 Maze & Associates
- 33. Social Media and Politics Rev2/28/2011 © 2011 Maze & Associates
- 34. IDENTITY THEFT Rev2/28/2011 © 2011 Maze & Associates
- 35. Social Media (Web 2.0) Services are extremely
- 36. Online Privacy Would you invite a stranger
- 37. Situation Why does someone want your personal
- 38. What is PII Personally Identifiable Information Name
- 39. ID Theft vs. ID Fraud “Identity fraud,"
- 40. March 20th 2001, MSNBC reported the first
- 41. ID Theft & Fraud PII exposed by
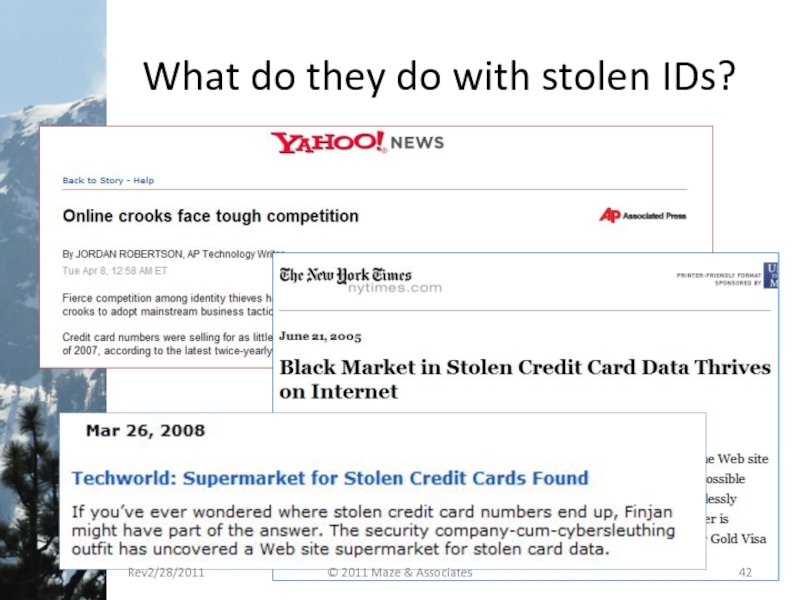
- 42. What do they do with stolen IDs? Rev2/28/2011 © 2011 Maze & Associates
- 43. Drug Trafficking and ID Theft Meth users
- 44. FTC 2009 Stats Top counties with ID
- 45. HOW MIGHT YOU EXPOSE YOUR PII Rev2/28/2011 © 2011 Maze & Associates
- 46. Watch what you put online Rev2/28/2011 © 2011 Maze & Associates http://www.youtube.com/watch?v=Soq3jzttwiA
- 47. Can someone use what you post against you? Rev2/28/2011 © 2011 Maze & Associates
- 48. P2P (Peer to Peer file sharing) Napster
- 49. HOW BAD GUYS MIGHT GET YOUR PII Rev2/28/2011 © 2011 Maze & Associates
- 50. Malware Malware (Viruses, Worms, Spyware, etc…) 1999
- 51. Viruses In the past they were primarily
- 52. Phishing: Internet Fraud Oldest trick in the
- 53. Rev2/28/2011 © 2011 Maze & Associates
- 54. Phishing Example Rev2/28/2011 © 2011 Maze & Associates
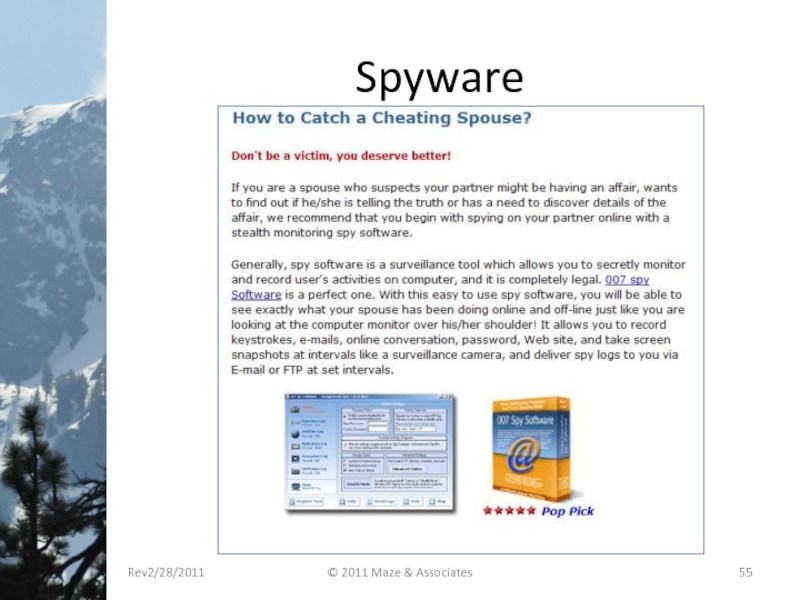
- 55. Spyware Rev2/28/2011 © 2011 Maze & Associates
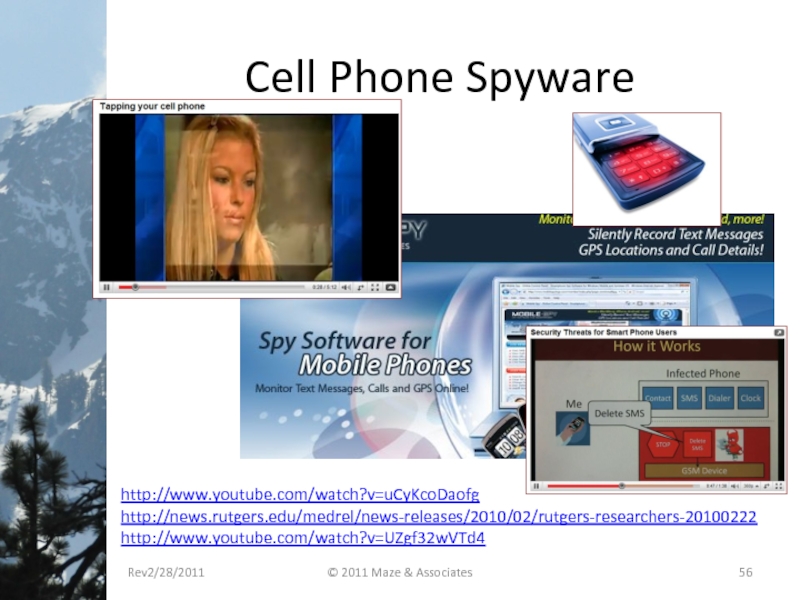
- 56. Cell Phone Spyware Rev2/28/2011 © 2011 Maze & Associates http://www.youtube.com/watch?v=uCyKcoDaofg http://news.rutgers.edu/medrel/news-releases/2010/02/rutgers-researchers-20100222 http://www.youtube.com/watch?v=UZgf32wVTd4
- 57. Physical theft Dumpster diving ATM – Credit
- 58. Close to Home Rev2/28/2011 © 2011 Maze & Associates
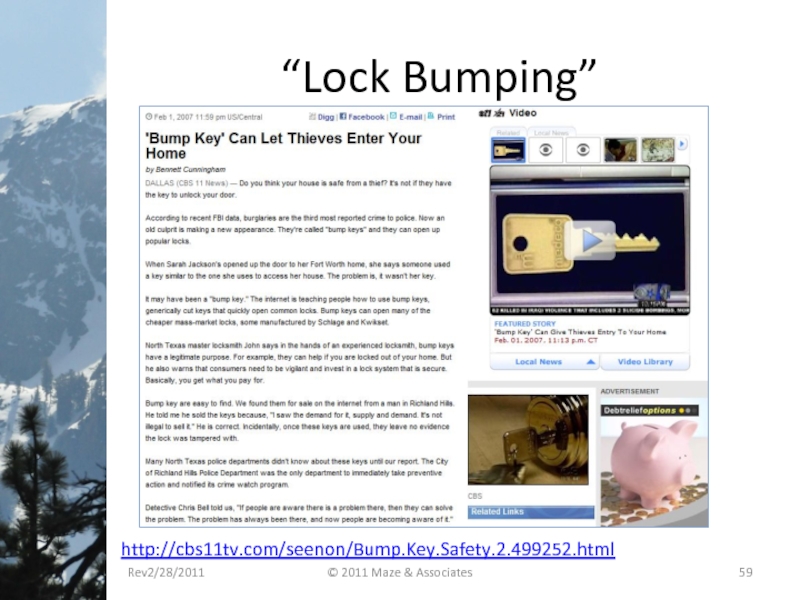
- 59. “Lock Bumping” http://cbs11tv.com/seenon/Bump.Key.Safety.2.499252.html Rev2/28/2011 © 2011 Maze & Associates
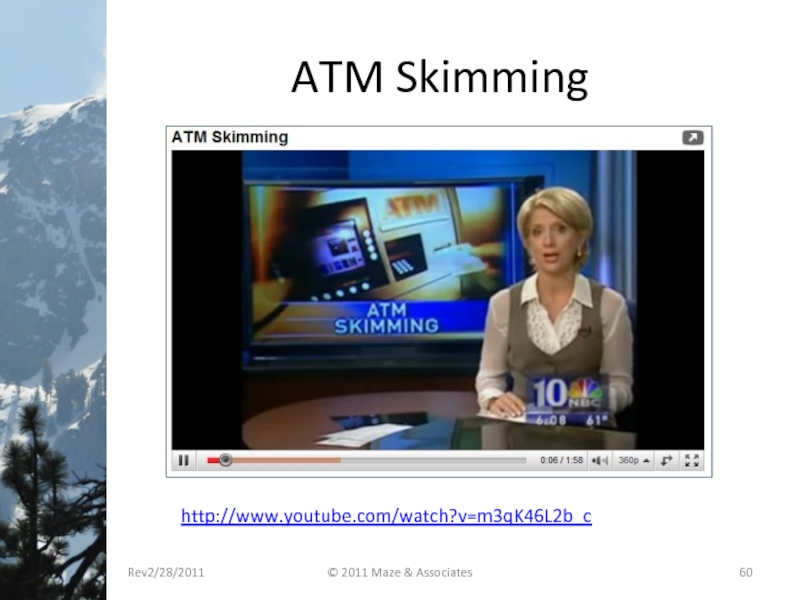
- 60. ATM Skimming Rev2/28/2011 © 2011 Maze & Associates http://www.youtube.com/watch?v=m3qK46L2b_c
- 61. Credit Card Skimming Rev2/28/2011 © 2011 Maze & Associates
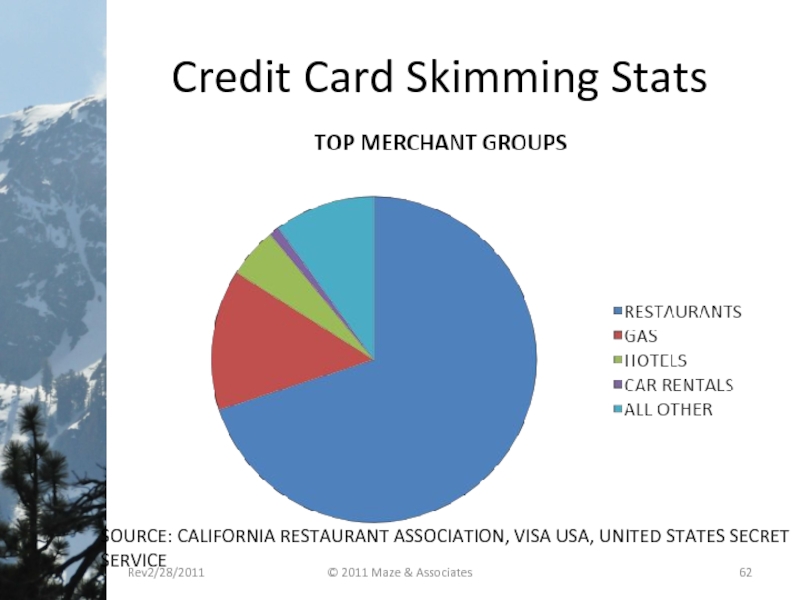
- 62. Credit Card Skimming Stats SOURCE: CALIFORNIA RESTAURANT
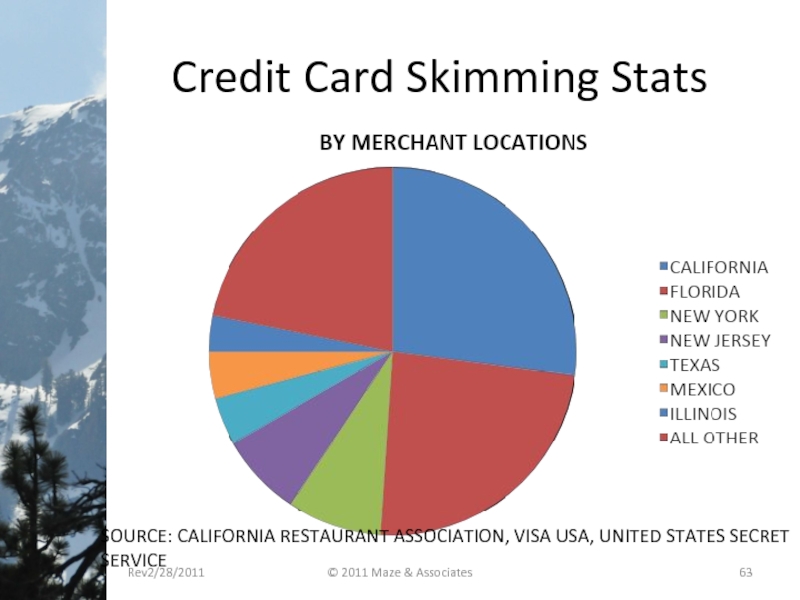
- 63. Credit Card Skimming Stats SOURCE: CALIFORNIA RESTAURANT
- 64. HOW OTHERS MIGHT EXPOSE YOUR PII Rev2/28/2011 © 2011 Maze & Associates
- 65. How others might expose your PII Data
- 66. Sony PlayStaion Network Breach Rev2/28/2011 © 2011 Maze & Associates
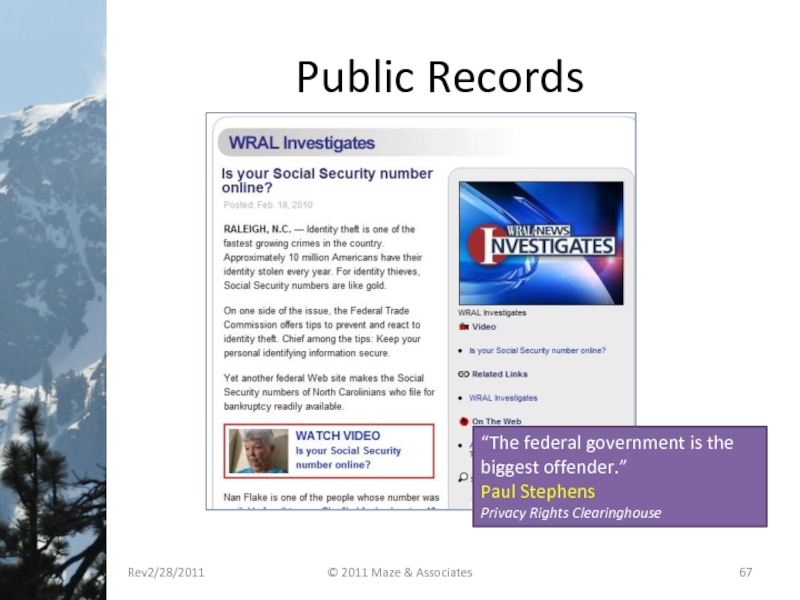
- 67. Public Records Rev2/28/2011 © 2011 Maze &
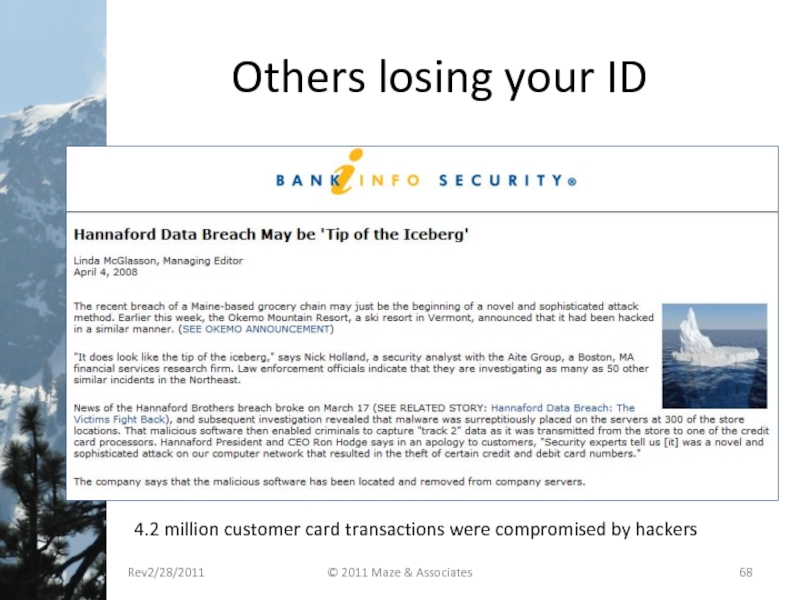
- 68. Others losing your ID 4.2 million customer
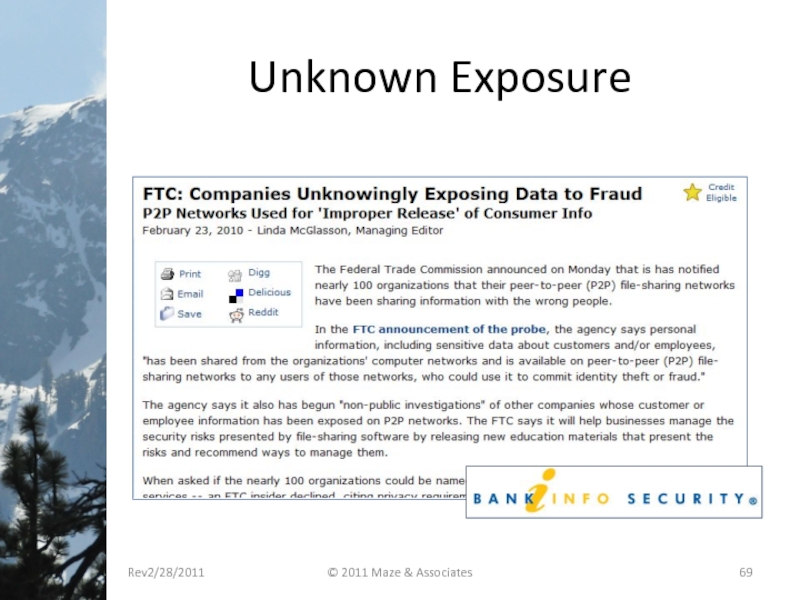
- 69. Unknown Exposure Rev2/28/2011 © 2011 Maze & Associates
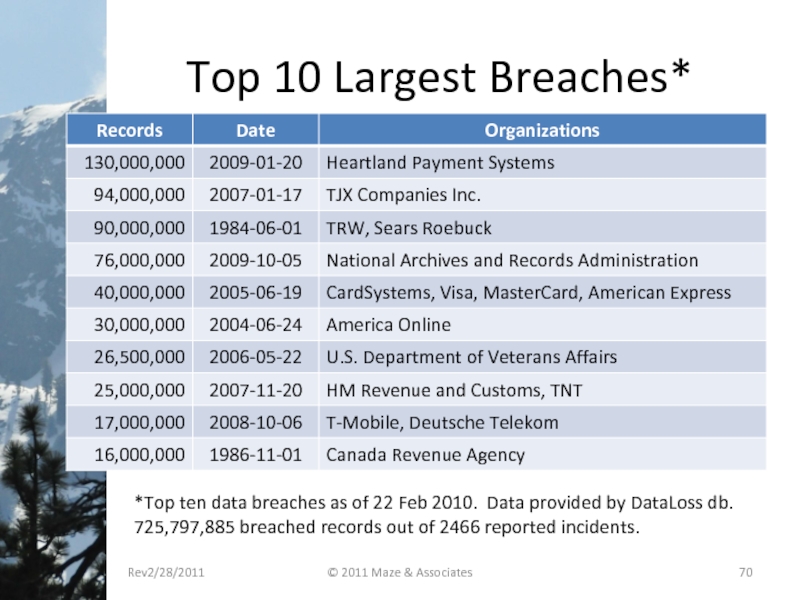
- 70. Top 10 Largest Breaches* Rev2/28/2011 © 2011
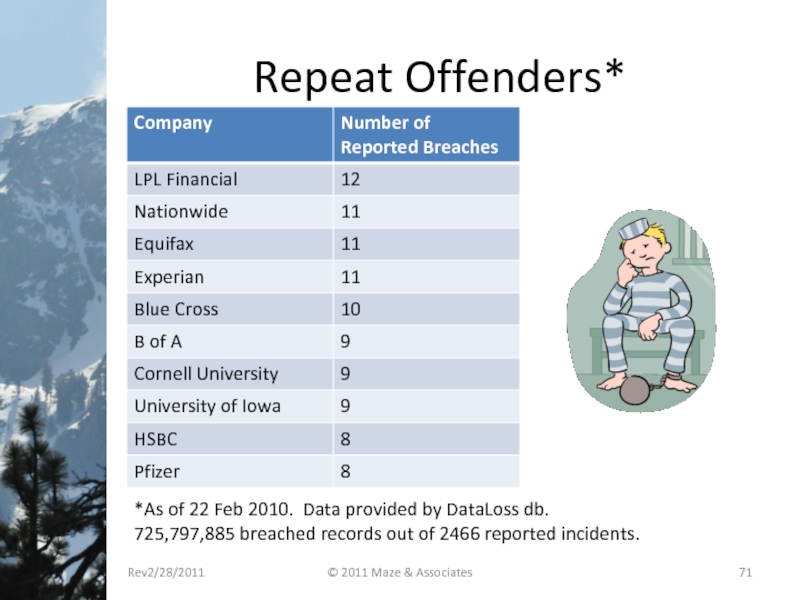
- 71. Repeat Offenders* Rev2/28/2011 © 2011 Maze &
- 72. Sony Root kit Sony, in its efforts
Слайд 2Donald E. Hester
CISSP, CISA, CAP, MCT, MCITP, MCTS, MCSE Security, Security+,
Director, Maze & Associates
University of San Francisco / San Diego City College
www.LearnSecurity.org | www.linkedin.com/in/donaldehester | www.facebook.com/LearnSec | www.twitter.com/sobca
DonaldH@MazeAssociates.com
Слайд 7Brand Protection - Concerns
Fear of losing control
Fear of losing customers
Fear of
Fear of customers speaking up
Avoiding social media
Fear of the unknown
Thinking it is a fade
Not understanding social media
How will you measure impact
Rev2/28/2011
© 2011 Maze & Associates
Слайд 11How to get started
Social Technology
The train has left the building, are
Get informed
Get help (technical and soft skills)
Develop a social media marketing strategic plan
Create short term goals
Execute and Adapt
Rev2/28/2011
© 2011 Maze & Associates
Слайд 12Marketing
Manger's Guide to Social Media
by Scott Klososky
The FaceBook Era
by
Facebook Marketing: An Hour a Day
by Chris Treadaway and Mari Smith
New Rules of Marketing and PR
by David Meerman Scott
The Zen of Social Media Marketing: An Easier Way to Build Credibility, Generate Buzz, and Increase Revenue
by Shama Kabani and Chris Brogan
Rev2/28/2011
© 2011 Maze & Associates
Слайд 17Endorsements
If you are being paid to endorse a product, you must
Rev2/28/2011
© 2011 Maze & Associates
http://www.ftc.gov/opa/2009/10/endortest.shtm
Слайд 19Social Media Uses in HR
The use of social media outside of
Concern that potential employers will misconstrue what is seen
Used for monitoring current employees
Used for screening job applicants
Employees see it as a good way to “get to know” the applicant
Rev2/28/2011
© 2011 Maze & Associates
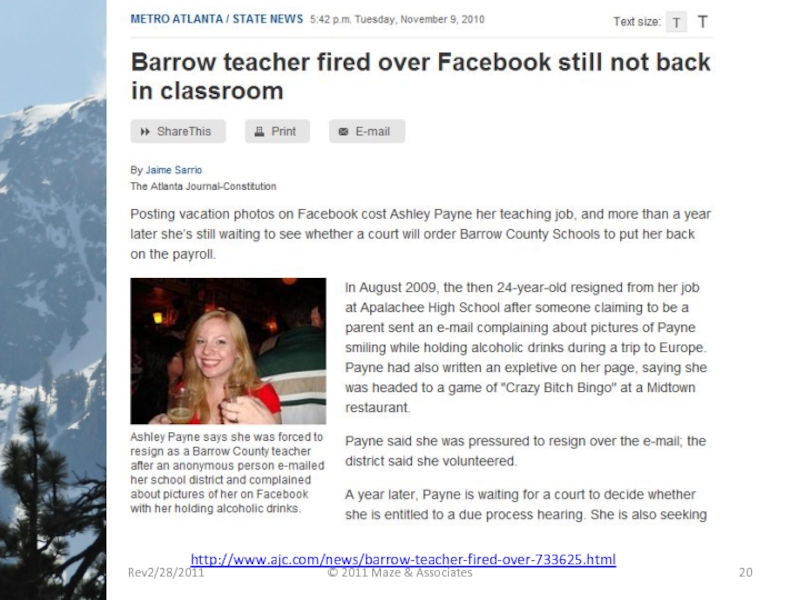
Слайд 20
http://www.ajc.com/news/barrow-teacher-fired-over-733625.html
Rev2/28/2011
© 2011 Maze & Associates
Слайд 21
http://www.dailyfinance.com/story/media/facebook-spying-costs-canadian-woman-her-health-benefits/19250917/
Rev2/28/2011
© 2011 Maze & Associates
Слайд 22
Rev2/28/2011
© 2011 Maze & Associates
http://smallbiztrends.com/2009/09/social-media-background-checks.html
Слайд 23Horns of a dilemma
If employers use social media to do background
The company is open to discrimination charges
The candidates is vulnerable to discrimination
Rev2/28/2011
© 2011 Maze & Associates
Слайд 24Horns of a dilemma
If employers don’t use social media to do
The company is open to negligent hires
Good candidates are missed
Bad candidates are hired
Rev2/28/2011
© 2011 Maze & Associates
Слайд 25Use of Social Media at Work
Does your company have a social
How much time do employees use social media?
Does it effect employee productivity?
How much cross over between work / home life?
Rev2/28/2011
© 2011 Maze & Associates
Слайд 28Online Privacy
Do you have control of what is posted?
Not all fame
People use anonymity to post stuff about others!
Embarrassing, loss of credibility
Rev2/28/2011
© 2011 Maze & Associates
Слайд 29Information about you online
Do I have control of what is posted
Look yourself up!
All but one of these is about me.
One of these I was completely unaware of.
Even if you are not on the web, you may be on the web!
Do what you can to control what is out there.
What is you social relevancy (Reputation)?
Rev2/28/2011
© 2011 Maze & Associates
Слайд 35Social Media (Web 2.0)
Services are extremely popular and useful
Almost a must
People post too much information about themselves or their kids
Be aware of your aggregate information
The key is to be aware of what you are sharing
Rev2/28/2011
© 2011 Maze & Associates
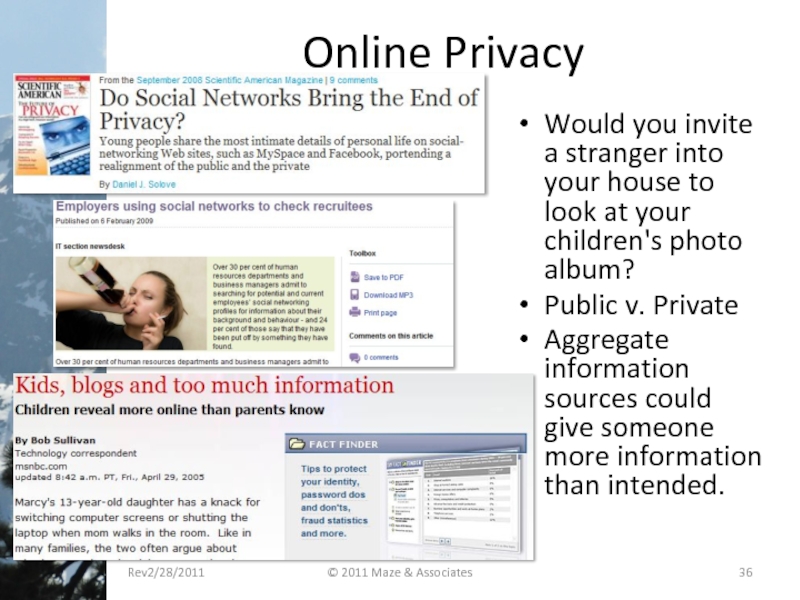
Слайд 36Online Privacy
Would you invite a stranger into your house to look
Public v. Private
Aggregate information sources could give someone more information than intended.
Rev2/28/2011
© 2011 Maze & Associates
Слайд 37Situation
Why does someone want your personal information?
In an information age information
Information has a value
Some information has a greater value
Your personal information is potentially worth more than you think
Rev2/28/2011
© 2011 Maze & Associates
Слайд 38What is PII
Personally Identifiable Information
Name and account number
Name and social security
Name and address
Credit Card Number
Where you might find it
Tax files
Account Statements
Records (Medical, Public and other)
Businesses you do business with
Rev2/28/2011
© 2011 Maze & Associates
Слайд 39ID Theft vs. ID Fraud
“Identity fraud," consists mainly of someone making
“Identity theft,” is when someone gathers your personal information and assumes your identity as their own.
"Identify theft is one of the fastest growing crimes in the US."
John Ashcroft
79th US Attorney General
Rev2/28/2011
© 2011 Maze & Associates
Слайд 40March 20th 2001, MSNBC reported the first identity theft case to
Thief assumed the identities of Oprah Winfrey and Martha Stewart, took out new credit cards in their names, and accessed their bank accounts
Stole more than $7 million from 200 of the world’s super rich - Warren Buffet and George Soros, tech tycoons Paul Allen and Larry Ellison
Used a library computer, public records, a cell phone, a fax machine, a PO Box, and a copy of Forbes Richest People
32-year-old Abraham Abdallah was described as “a high school dropout, a New York City busboy, a pudgy, disheveled, career petty criminal.”
The Busboy That Started It All
Rev2/28/2011
© 2011 Maze & Associates
Слайд 41ID Theft & Fraud
PII exposed by others (Data Breaches)
PII exposed by
Malware (Spyware, Viruses, etc…)
Social Engineering
Phone
Internet (Phishing, social websites etc…)
In Person (at your door, in a restaurant etc…)
Physical theft
Mail box
Trash (Dumpster diving)
ATMs (skimming)
Home break-ins
Rev2/28/2011
© 2011 Maze & Associates
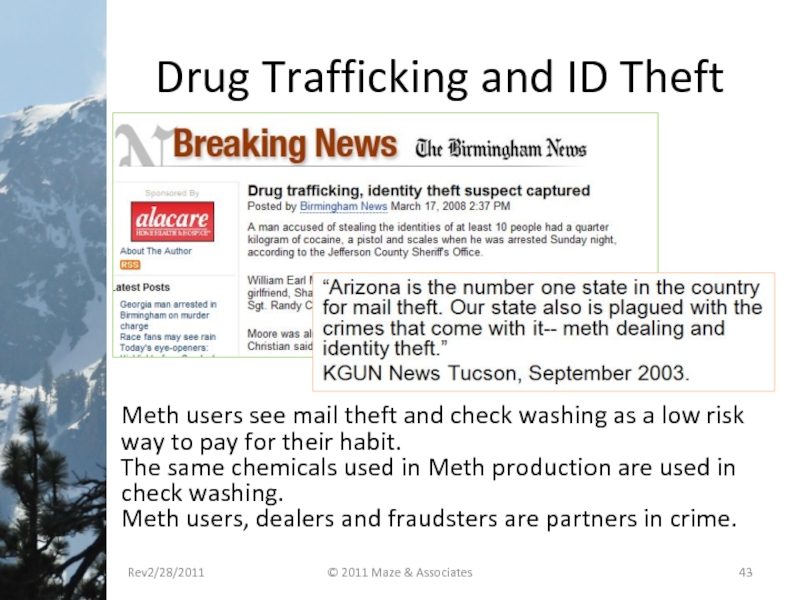
Слайд 43Drug Trafficking and ID Theft
Meth users see mail theft and check
The same chemicals used in Meth production are used in check washing.
Meth users, dealers and fraudsters are partners in crime.
Rev2/28/2011
© 2011 Maze & Associates
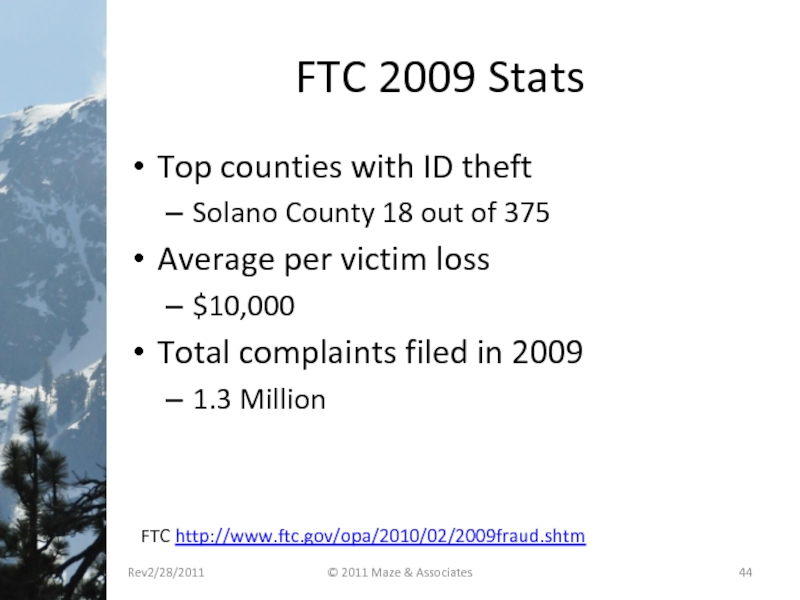
Слайд 44FTC 2009 Stats
Top counties with ID theft
Solano County 18 out of
Average per victim loss
$10,000
Total complaints filed in 2009
1.3 Million
Rev2/28/2011
© 2011 Maze & Associates
FTC http://www.ftc.gov/opa/2010/02/2009fraud.shtm
Слайд 46Watch what you put online
Rev2/28/2011
© 2011 Maze & Associates
http://www.youtube.com/watch?v=Soq3jzttwiA
Слайд 48P2P (Peer to Peer file sharing)
Napster used to fit in this
Used to ‘share’ computer files
Legal issues with copyright
Malware issues, often the P2P software will install adware or tracking software.
Privacy issues, do you know what you are sharing?
Rev2/28/2011
© 2011 Maze & Associates
Слайд 50Malware
Malware (Viruses, Worms, Spyware, etc…)
1999 Melissa, Kevin Mitnick,
2000 Mafiaboy, DoS
2001 Code Red, Nimda,
2002 Root Rot, Slapper,
2003 SQL Slammer,
2004 MyDoom, BerBew,
2005 Samy (MySpace),
2007 Storm Worm, Botnets, etc..
Malware has cost trillions of dollars in the last decade
Rev2/28/2011
© 2011 Maze & Associates
Слайд 51Viruses
In the past they were primarily destructive
Today they focus on stealing
Using your computer as a Bot (Zombie) to send out SPAM
Rev2/28/2011
© 2011 Maze & Associates
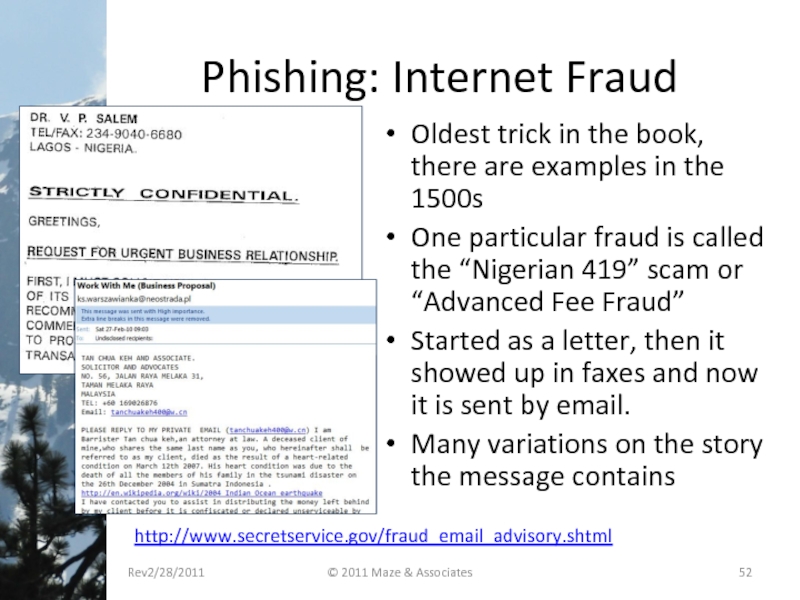
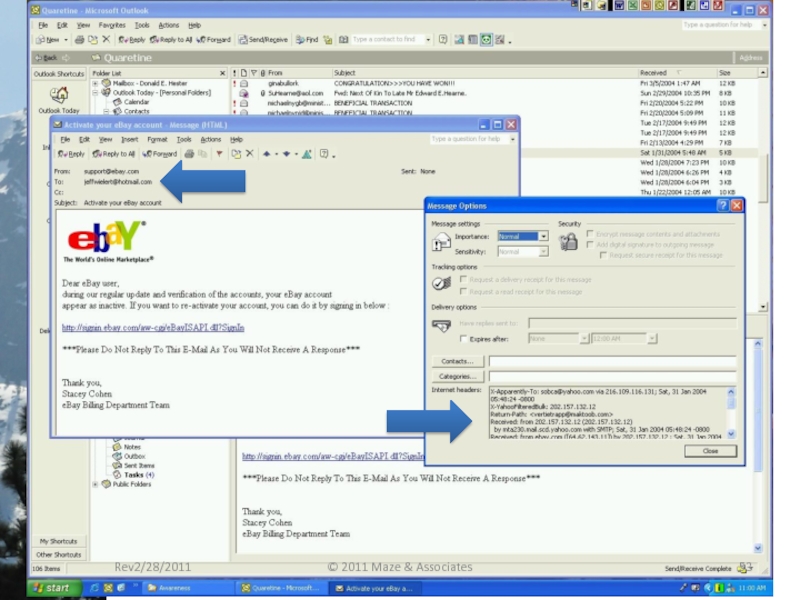
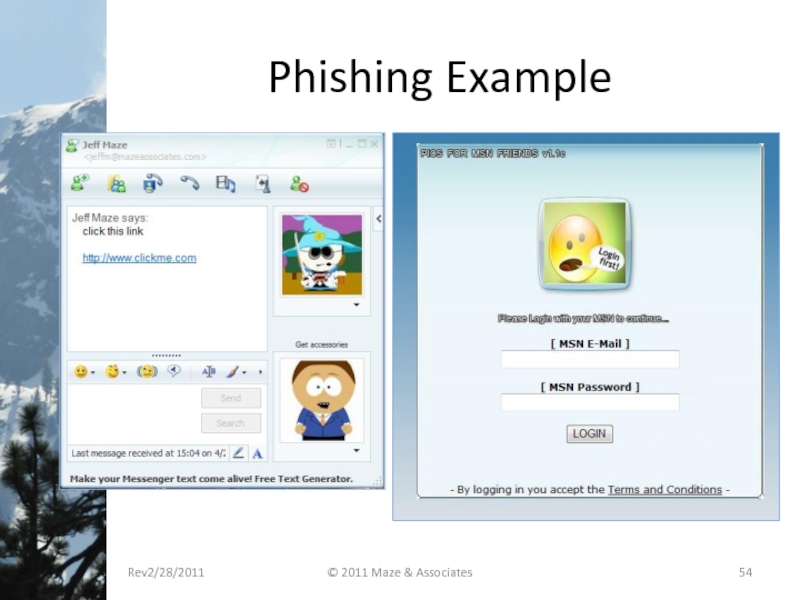
Слайд 52Phishing: Internet Fraud
Oldest trick in the book, there are examples in
One particular fraud is called the “Nigerian 419” scam or “Advanced Fee Fraud”
Started as a letter, then it showed up in faxes and now it is sent by email.
Many variations on the story the message contains
http://www.secretservice.gov/fraud_email_advisory.shtml
Rev2/28/2011
© 2011 Maze & Associates
Слайд 56Cell Phone Spyware
Rev2/28/2011
© 2011 Maze & Associates
http://www.youtube.com/watch?v=uCyKcoDaofg
http://news.rutgers.edu/medrel/news-releases/2010/02/rutgers-researchers-20100222
http://www.youtube.com/watch?v=UZgf32wVTd4
Слайд 57Physical theft
Dumpster diving
ATM – Credit Card skimming
Mailbox
Home Break-in
Rev2/28/2011
© 2011 Maze &
Слайд 59“Lock Bumping”
http://cbs11tv.com/seenon/Bump.Key.Safety.2.499252.html
Rev2/28/2011
© 2011 Maze & Associates
Слайд 62Credit Card Skimming Stats
SOURCE: CALIFORNIA RESTAURANT ASSOCIATION, VISA USA, UNITED STATES
Rev2/28/2011
© 2011 Maze & Associates
Слайд 63Credit Card Skimming Stats
SOURCE: CALIFORNIA RESTAURANT ASSOCIATION, VISA USA, UNITED STATES
Rev2/28/2011
© 2011 Maze & Associates
Слайд 65How others might expose your PII
Data Breach
Lack of security on the
Organization may post information online
Loss of a laptop, hard drive or paper work
Data loss by a third party
Hacker (Organized Crime & Nation State)
Organizations may break into your computer
Rev2/28/2011
© 2011 Maze & Associates
Слайд 67Public Records
Rev2/28/2011
© 2011 Maze & Associates
“The federal government is the biggest
Paul Stephens
Privacy Rights Clearinghouse
Слайд 68Others losing your ID
4.2 million customer card transactions were compromised by
Rev2/28/2011
© 2011 Maze & Associates
Слайд 70Top 10 Largest Breaches*
Rev2/28/2011
© 2011 Maze & Associates
*Top ten data breaches
725,797,885 breached records out of 2466 reported incidents.
Слайд 71Repeat Offenders*
Rev2/28/2011
© 2011 Maze & Associates
*As of 22 Feb 2010. Data
725,797,885 breached records out of 2466 reported incidents.
Слайд 72Sony Root kit
Sony, in its efforts to preserve control over its
Consumers were not aware it was installed (on copy-protected CDs)
Gave Sony and potentially hackers the ability to remotely control your computer
Removal of software disabled CD drives on consumers computers
http://www.cnet.com/4520-6033_1-6376177-1.html?tag=nl.e501
Rev2/28/2011
© 2011 Maze & Associates