- Главная
- Разное
- Дизайн
- Бизнес и предпринимательство
- Аналитика
- Образование
- Развлечения
- Красота и здоровье
- Финансы
- Государство
- Путешествия
- Спорт
- Недвижимость
- Армия
- Графика
- Культурология
- Еда и кулинария
- Лингвистика
- Английский язык
- Астрономия
- Алгебра
- Биология
- География
- Детские презентации
- Информатика
- История
- Литература
- Маркетинг
- Математика
- Медицина
- Менеджмент
- Музыка
- МХК
- Немецкий язык
- ОБЖ
- Обществознание
- Окружающий мир
- Педагогика
- Русский язык
- Технология
- Физика
- Философия
- Химия
- Шаблоны, картинки для презентаций
- Экология
- Экономика
- Юриспруденция
Lecture1 - SOA, XML, XSD презентация
Содержание
- 1. Lecture1 - SOA, XML, XSD
- 2. Confidential Introduction Senior Software Test
- 3. Confidential Some rules Listen
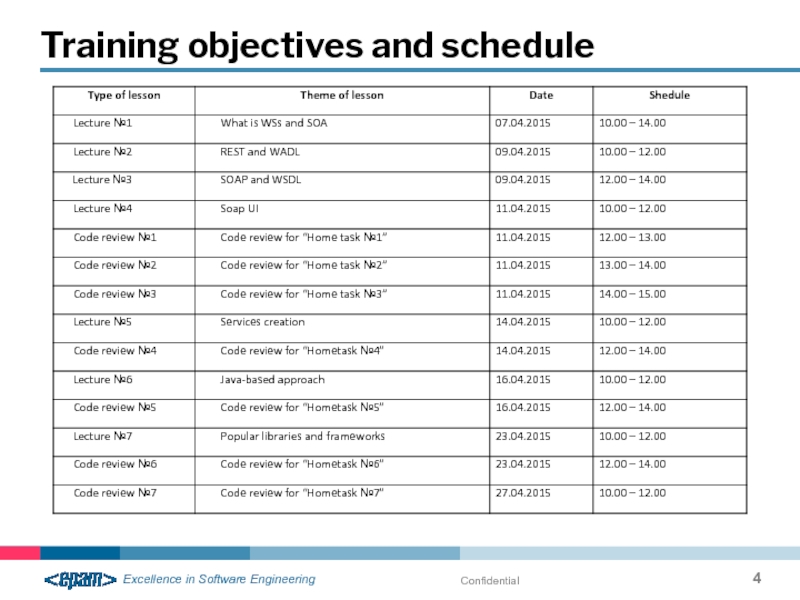
- 4. Confidential Training objectives and schedule
- 5. Confidential Service- Oriented Architecture
- 6. Confidential What is SOA? Service-oriented architecture
- 7. Confidential What is SOA? SOA also
- 8. Confidential Example of SOA From Life
- 9. Confidential Example of SOA From Life getBook(Pushkin); setBook(Dostoevski); removeBook(Tolstoy);
- 10. Confidential SOA Goals Reducing costs when
- 11. Confidential SOA
- 12. Confidential Web- Service
- 13. Confidential Why do we need Web Services?
- 14. Confidential The Intelligence is in the Connections
- 15. Confidential How do people communication? Medium & Shared vocabulary
- 16. Confidential How does software communicate?
- 17. Confidential Web Service - Definition W3C Definition
- 18. Confidential Web Service – what are?
- 19. Confidential Web Service – type of usage
- 20. Confidential Reusable application-components Source: https://developers.facebook.com/docs/plugins/like-button/ Facebook like
- 21. Confidential Connect existing software Google maps Source: https://developers.google.com/maps/
- 22. Confidential Real project example Epam - Expedia
- 23. Confidential Real project example Epam - Expedia
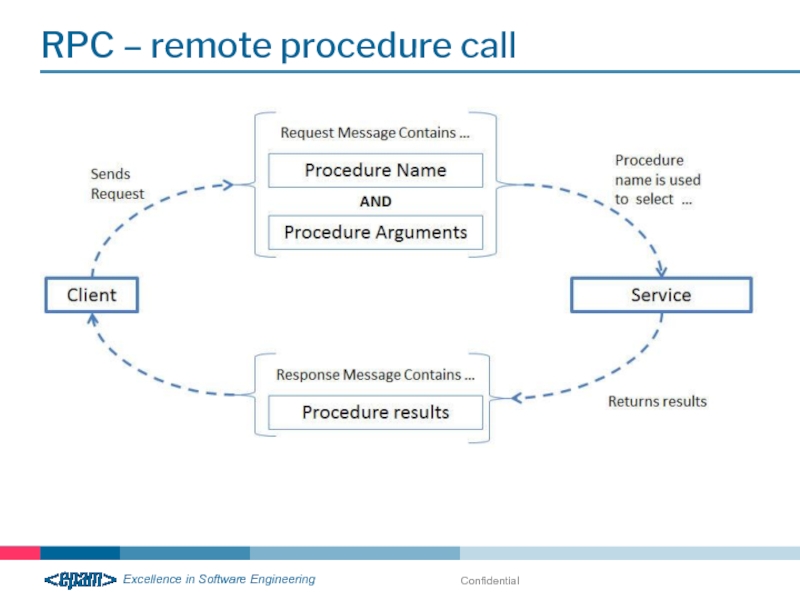
- 24. RPC – remote procedure call Confidential
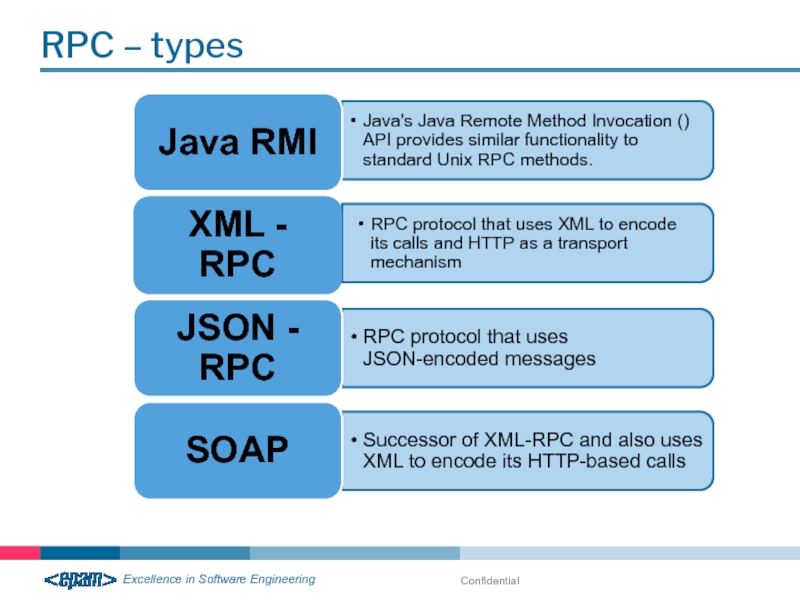
- 25. RPC – types Confidential
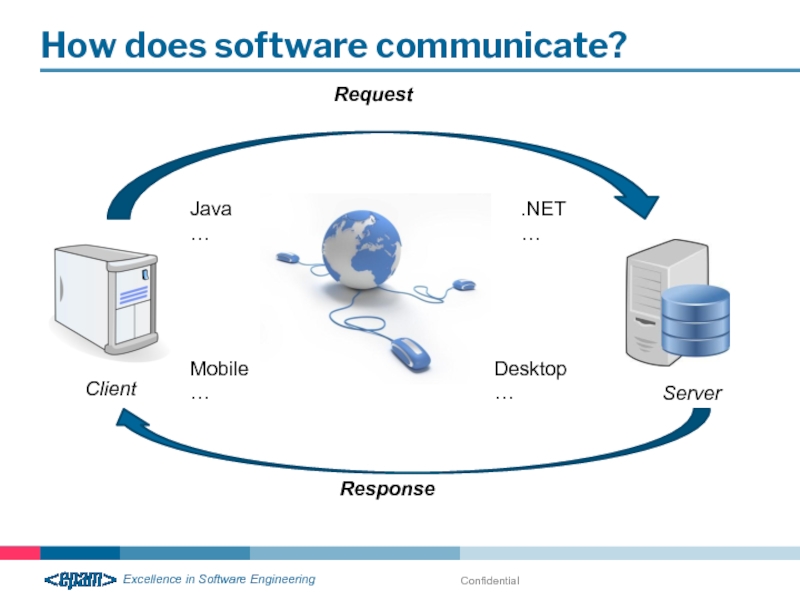
- 26. Confidential How does software communicate?
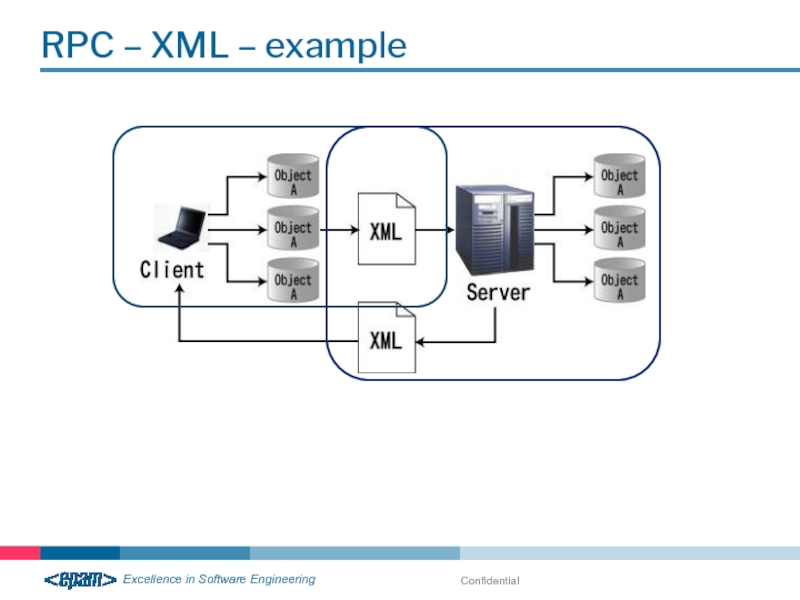
- 27. RPC – XML – example Confidential
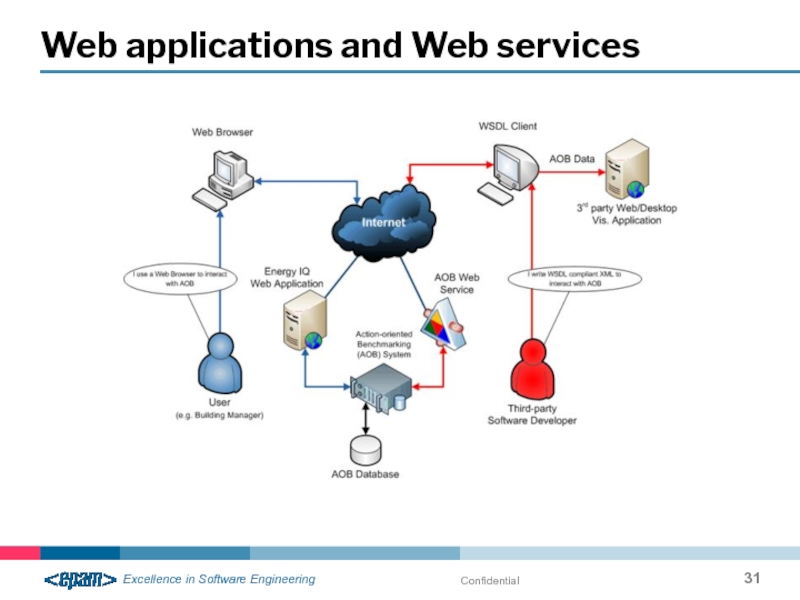
- 28. Confidential Web services & Web applications
- 29. Confidential Widely Well-known words Web
- 30. Confidential Widely Well-known words Web Server
- 31. Confidential Web applications and Web services
- 32. Confidential Extensible Markup Language (XML)
- 33. Confidential Based on Standard Generalized Markup
- 34. Confidential XML data can be stored
- 35. Confidential Give the life for derived
- 36. Confidential Well-formed XML
- 37. Confidential Well-formed XML All elements must
- 38. Confidential Well-formed XML Names of elements
- 39. Confidential Well-formed XML Elements can not
- 40. Confidential Well-formed XML All attribute values
- 41. Confidential Well-formed XML Unlike HTML, XML
- 42. Confidential XML and HTML. Semantics The
- 43. Confidential Pros of XML format Creation
- 44. Confidential Cons of XML format XML
- 45. Confidential Component parts of XML document
- 46. Confidential Prologue
- 47. Confidential XML declaration version="1.0" encoding="UTF-8"
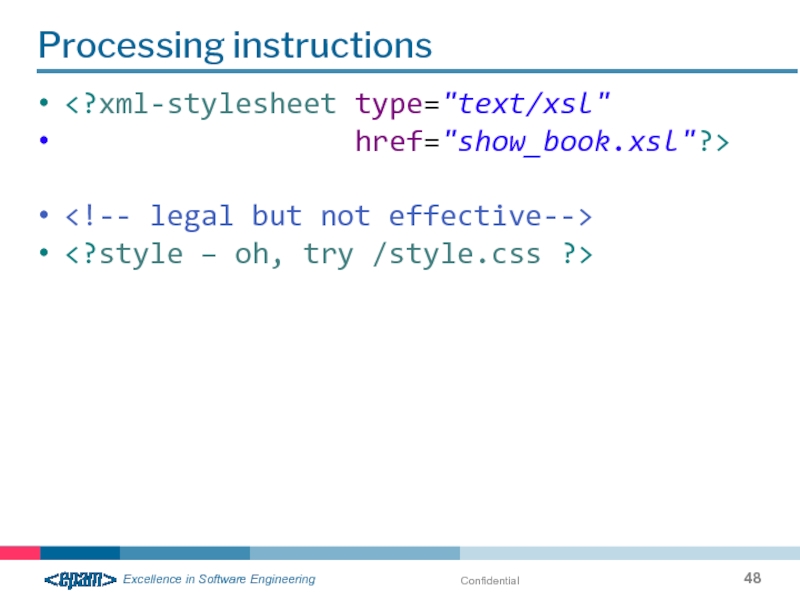
- 48. Confidential Processing instructions
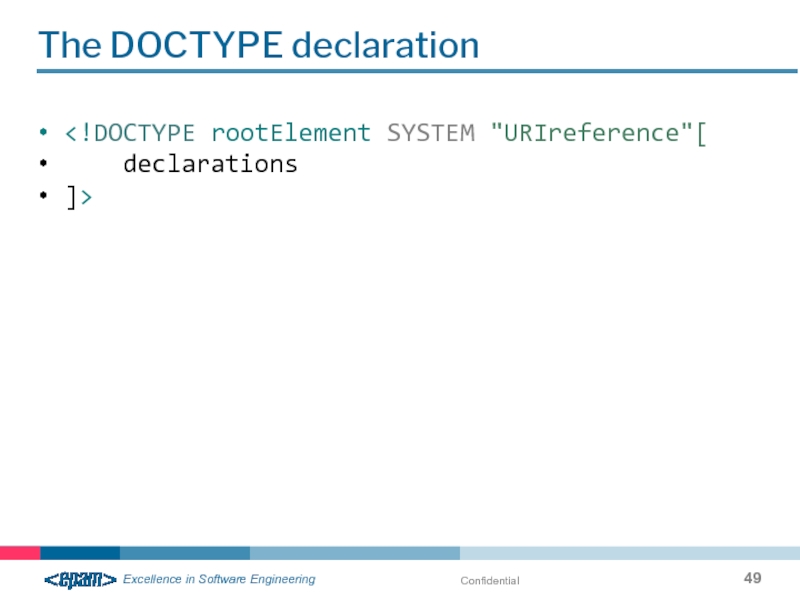
- 49. Confidential The DOCTYPE declaration
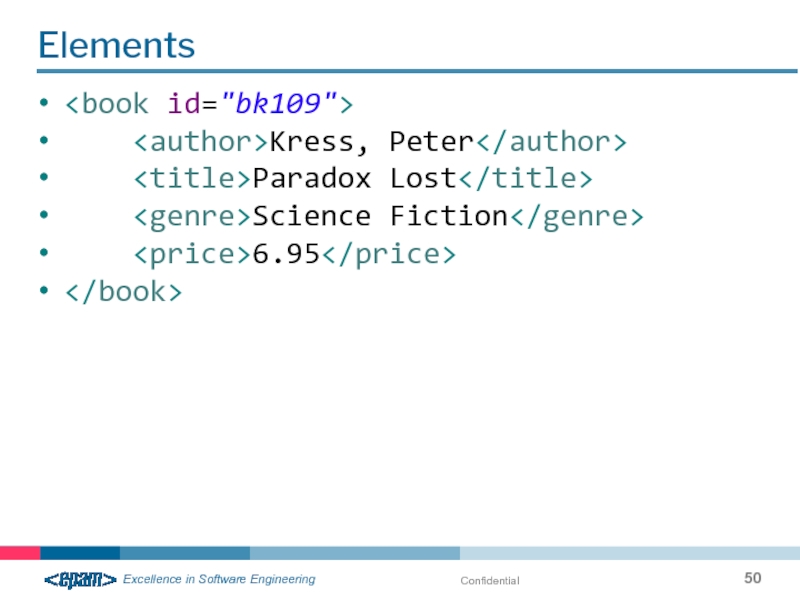
- 50. Confidential Elements Kress,
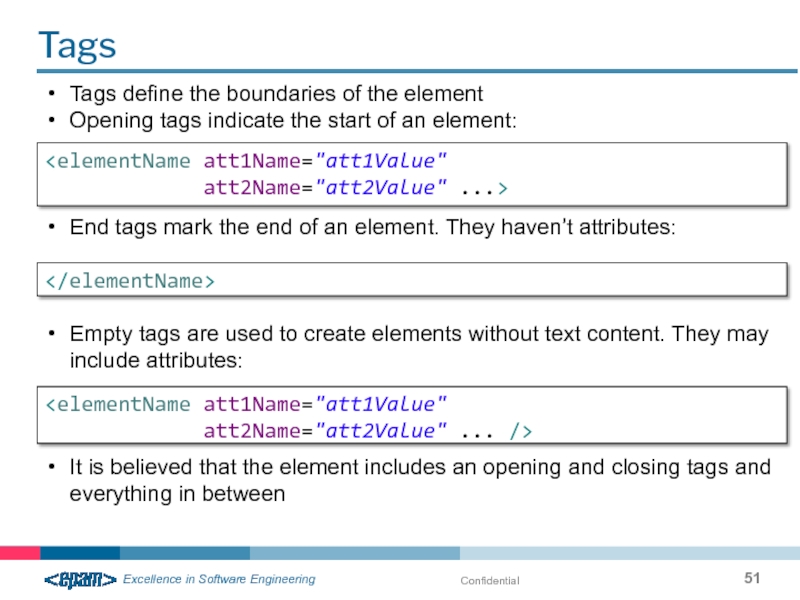
- 51. Confidential Tags Tags
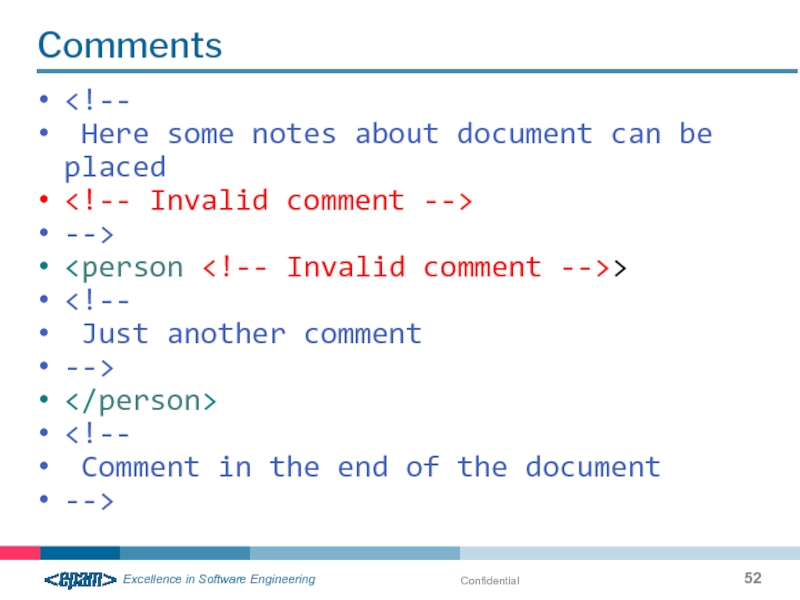
- 52. Confidential Comments -->
- 53. Confidential Text blocks Instead of characters
- 54. Confidential Pointers to characters and entities
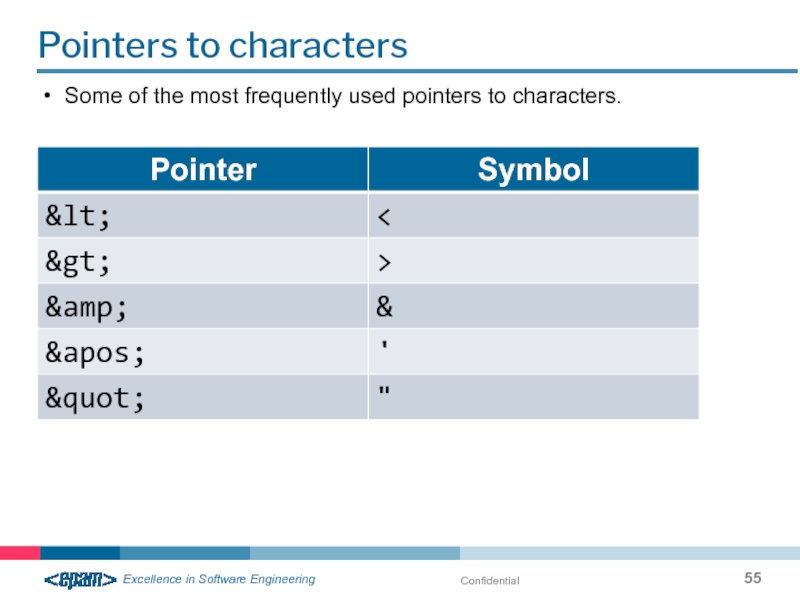
- 55. Confidential Pointers to characters Some of the most frequently used pointers to characters.
- 56. Confidential CDATA Blocks CDATA sections give
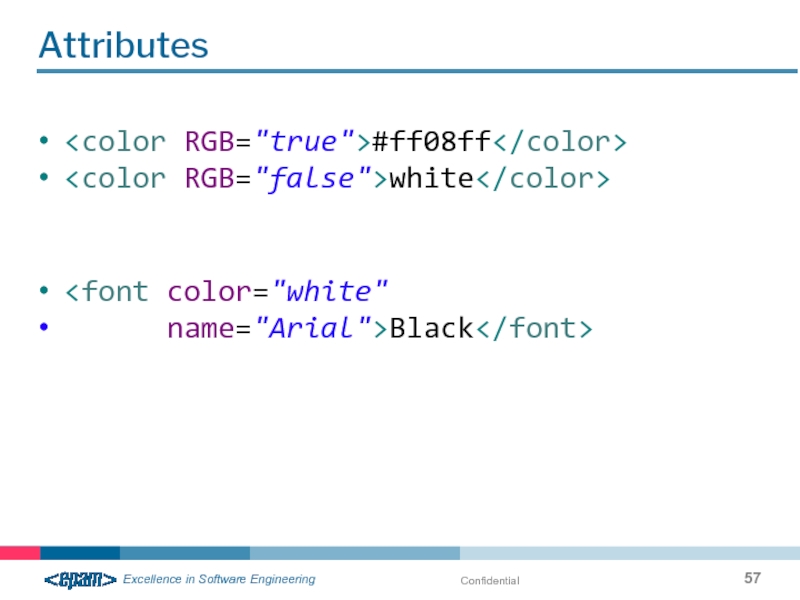
- 57. Confidential Attributes #ff08ff white Black
- 58. Confidential Usage of Namespaces XML namespace
- 59. Confidential The scope of namespace Namespace
- 60. Confidential XSD
- 61. Confidential What is XML schema (XSD)?
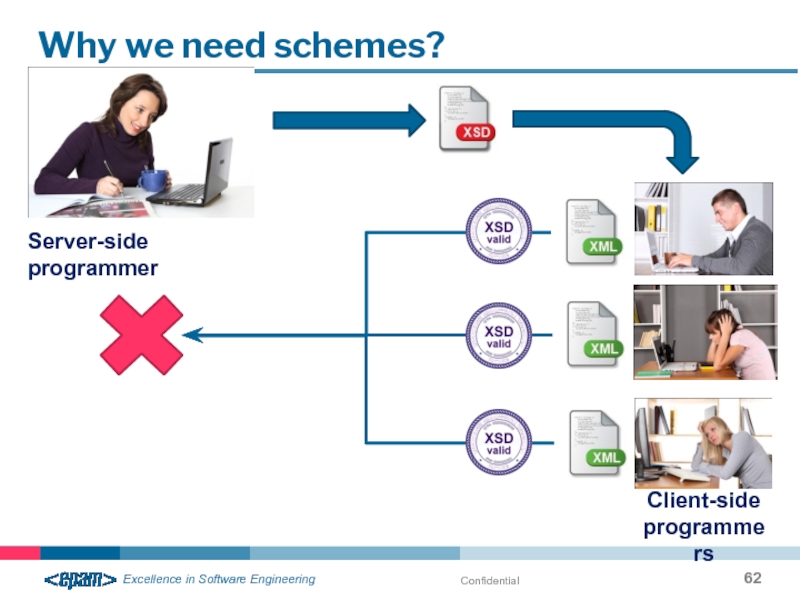
- 62. Confidential Why we need schemes? Server-side programmer Client-side programmers
- 63. Confidential Creation of XML Schema
- 64. Confidential Simple elements Elements are declared
- 65. Confidential Attributes Attributes are declared using
- 66. Confidential Simple Type SimpleType element defines
- 67. Confidential Complex Type Composite type describes
- 68. Confidential Element simpleContent For expansion /
- 69. Confidential Element complexContent ComplexContent element serves
- 70. Confidential Types Types of elements /
- 71. Confidential Using of elements and attributes
- 72. Confidential Base types XML schema contains
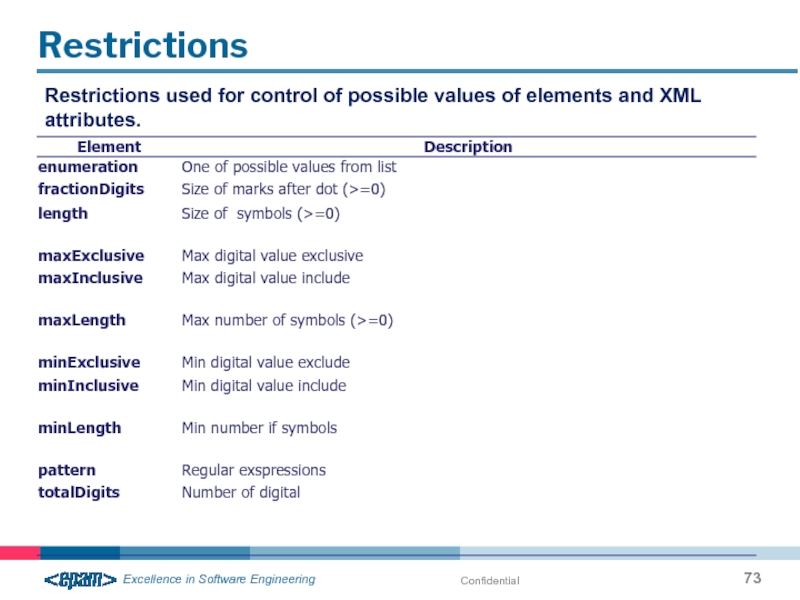
- 73. Confidential Restrictions Restrictions used for control of possible values of elements and XML attributes.
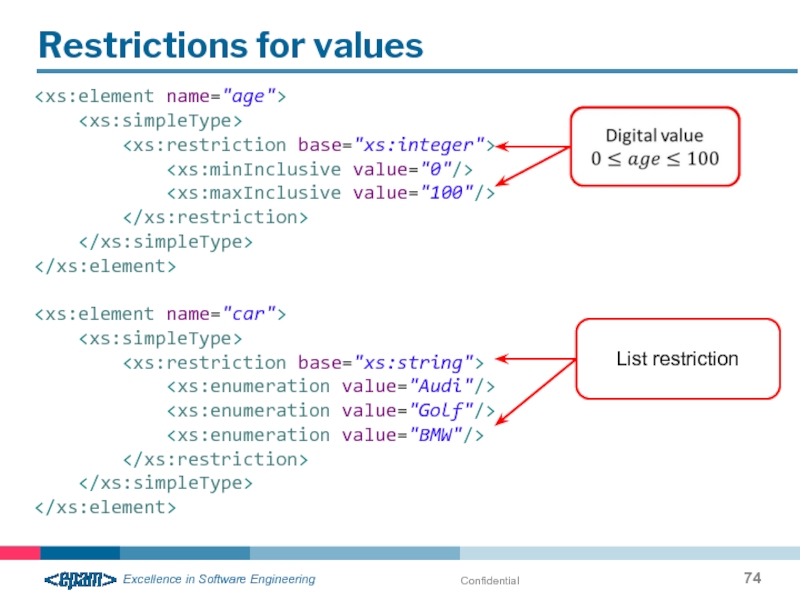
- 74. Confidential Restrictions for values
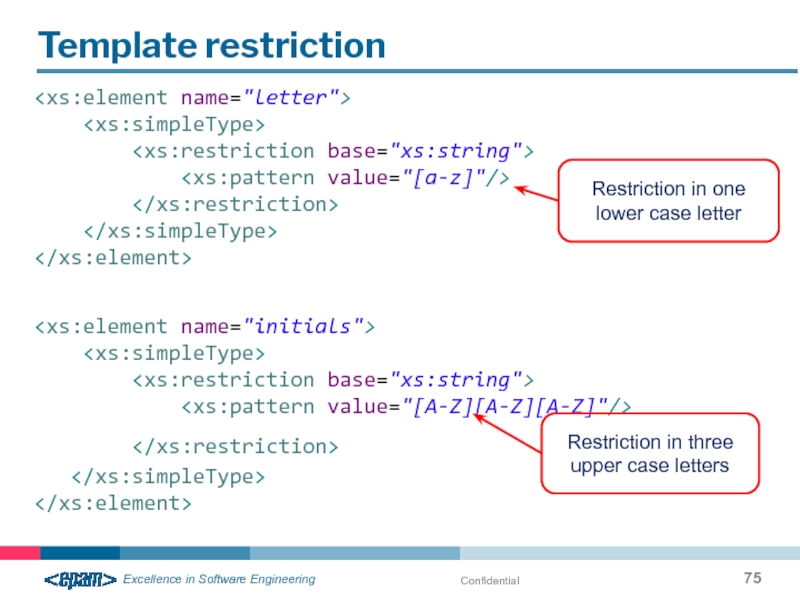
- 75. Confidential Template restriction
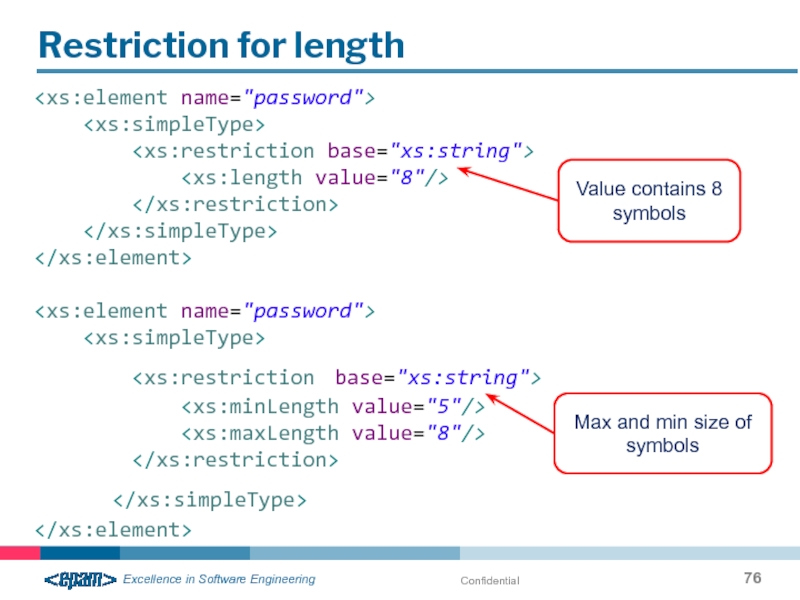
- 76. Confidential Restriction for length
- 77. Confidential White spaces restriction Restriction whiteSpace
- 78. Confidential Indicators XML Schema has
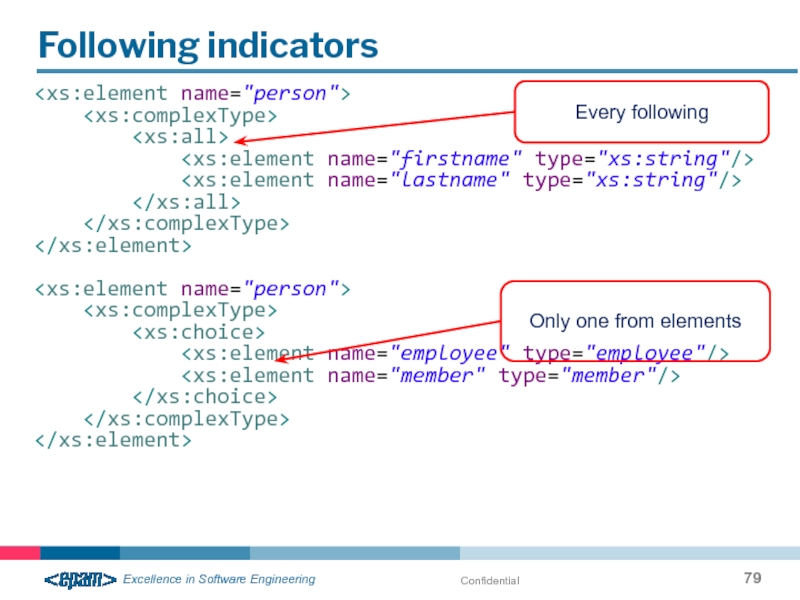
- 79. Confidential Following indicators
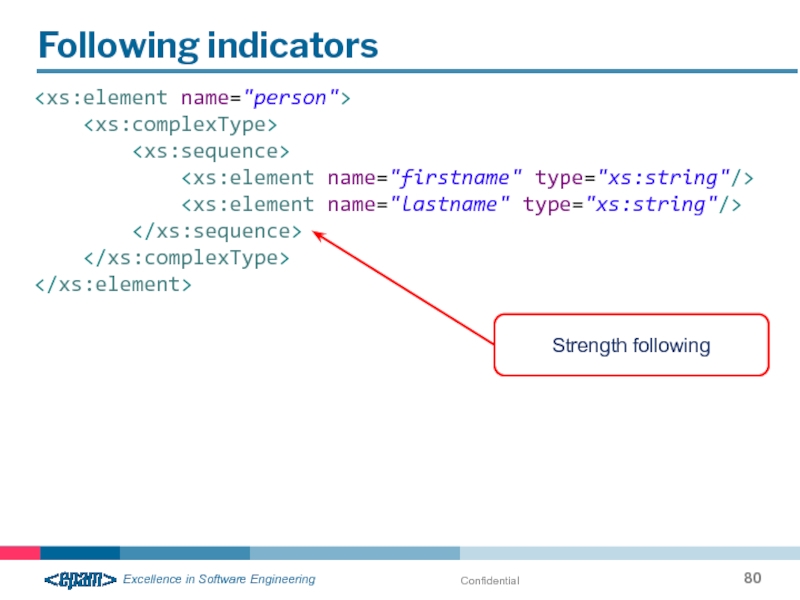
- 80. Confidential Following indicators
- 81. Confidential Input indicators For size of
- 82. Confidential Indicators input Indicator maxOccurs can
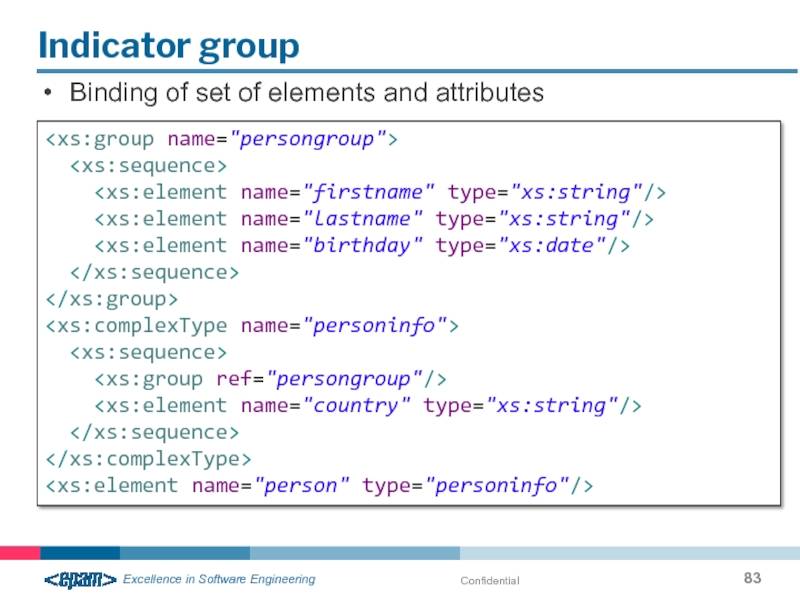
- 83. Confidential Indicator group Binding of set
- 84. Confidential Element unique Attribute or element
- 85. Confidential Unique – Example
- 86. Confidential Schema documentation Can us simple
- 87. Confidential Describe ref to XSD in
- 88. Confidential Describing of ref to XSD
- 89. Confidential What was learnt for today?
- 90. Confidential What was learnt for today?
- 91. Thank you for your attention! Anastasiya Babovich Anastasiya_Babovich@epam.com
Слайд 1Web Services (WSs) and
Service-oriented architecture (SOA)
Test automation for WSs
Confidential
Слайд 2Confidential
Introduction
Senior Software Test Automation Engeneer
More than 2 year in
Expertise:
UI Test Automation based on Java
WS Test Automation using tools and custom frameworks
BDD approaches
Anastasiya Babovich
E-mail: Anastsiya_Babovich@epam.com
Skype: anastasiya_babovich
Слайд 3Confidential
Some rules
Listen attentively
The rule of hand
Turn off your phones
Be punctual
Слайд 6Confidential
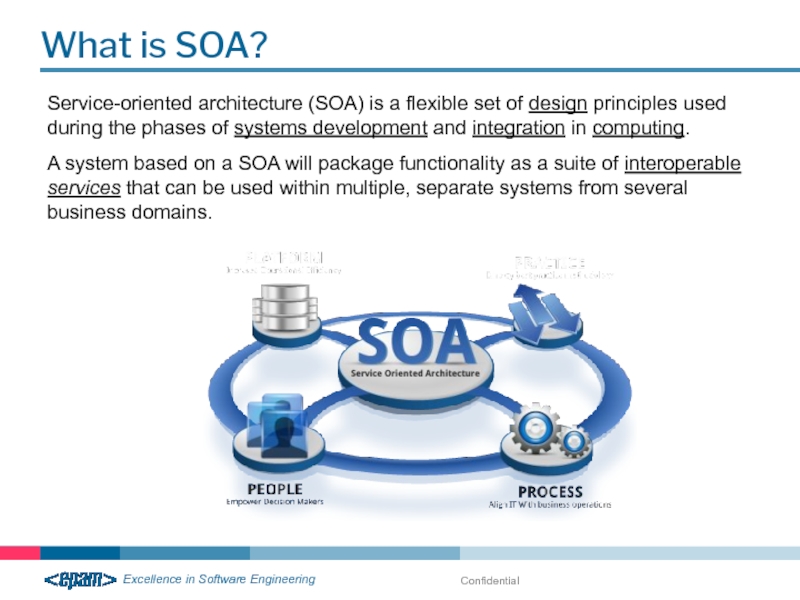
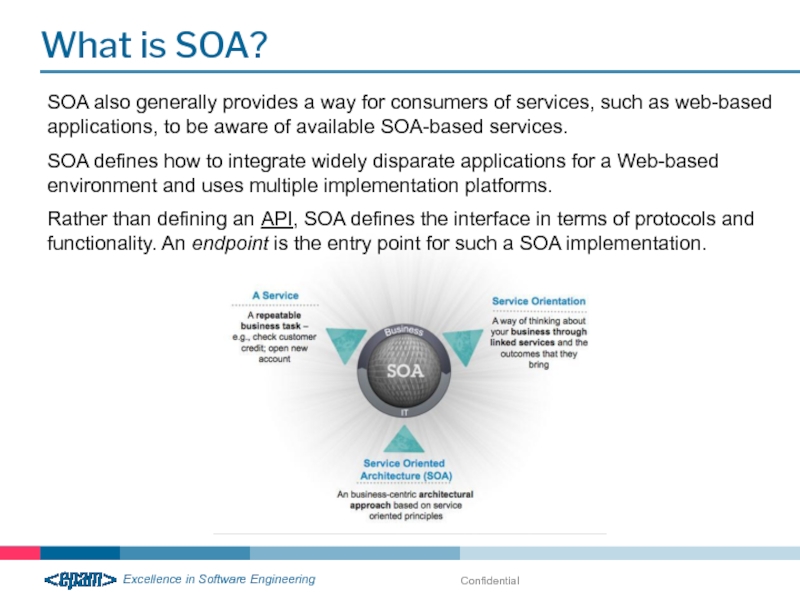
What is SOA?
Service-oriented architecture (SOA) is a flexible set of design
A system based on a SOA will package functionality as a suite of interoperable services that can be used within multiple, separate systems from several business domains.
Слайд 7Confidential
What is SOA?
SOA also generally provides a way for consumers of
SOA defines how to integrate widely disparate applications for a Web-based environment and uses multiple implementation platforms.
Rather than defining an API, SOA defines the interface in terms of protocols and functionality. An endpoint is the entry point for such a SOA implementation.
Слайд 9Confidential
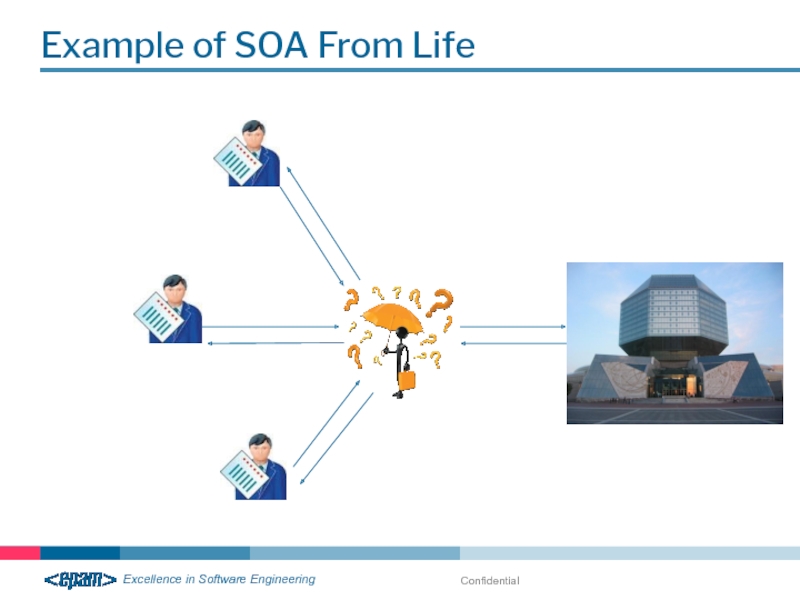
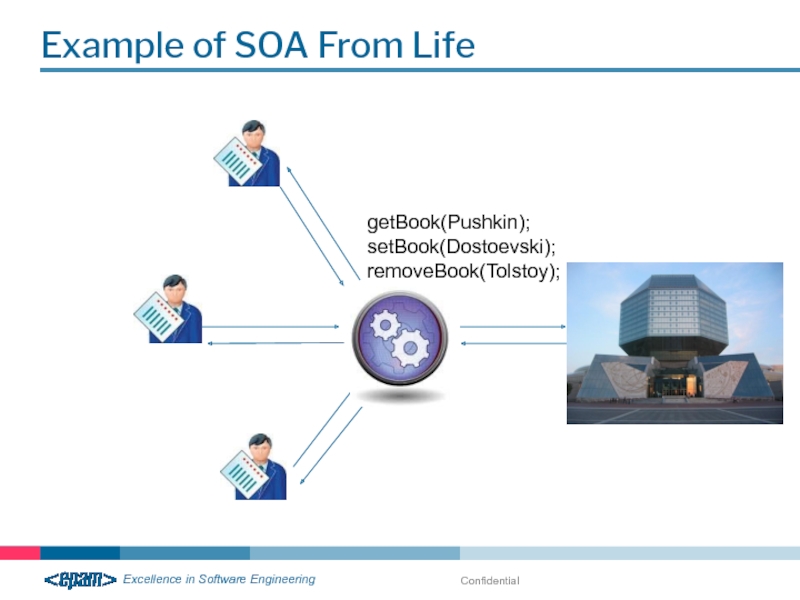
Example of SOA From Life
getBook(Pushkin);
setBook(Dostoevski);
removeBook(Tolstoy);
Слайд 10Confidential
SOA Goals
Reducing costs when developing applications, due to streamlining the development
Increased code reuse.
Independence of the platform, tools, development languages;
Increased scalability posed systems;
Improved manageability of systems produced;
Слайд 11
Confidential
SOA Principles
Architecture is not tied to any particular technology.
Independence of the
Independence of the organization system used by programming languages.
Use services that are independent of specific applications, with a uniform interface to access them.
Organization of services as a weakly-coupled components for building systems.
Слайд 16Confidential
How does software communicate?
Client
Server
Java
…
.NET
…
Desktop
…
Mobile
…
Request
Response
Слайд 17Confidential
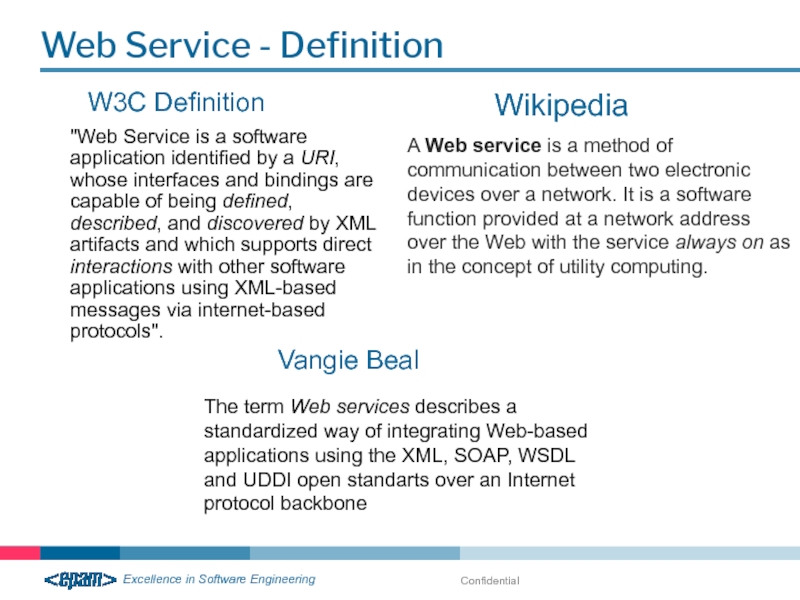
Web Service - Definition
W3C Definition
"Web Service is a software application identified
A Web service is a method of communication between two electronic devices over a network. It is a software function provided at a network address over the Web with the service always on as in the concept of utility computing.
Wikipedia
The term Web services describes a standardized way of integrating Web-based applications using the XML, SOAP, WSDL and UDDI open standarts over an Internet protocol backbone
Vangie Beal
Слайд 18Confidential
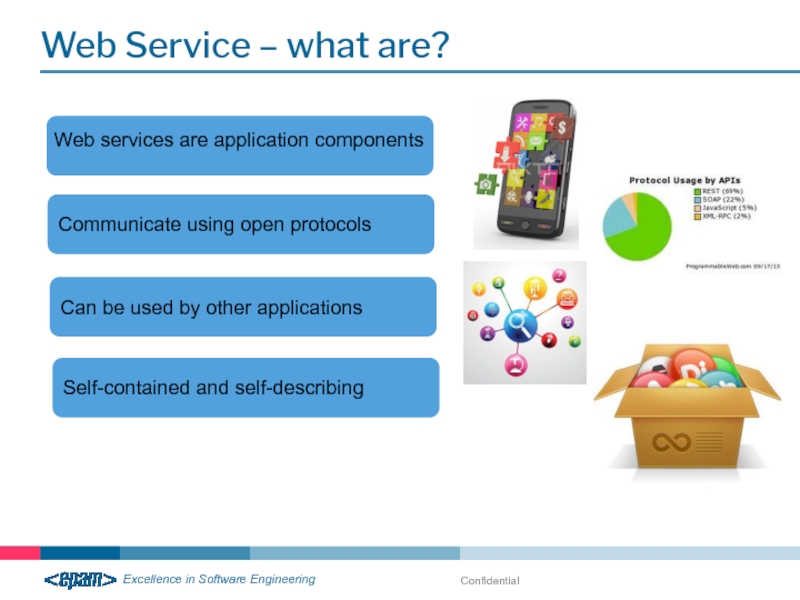
Web Service – what are?
Web services are application components
Communicate using open
Can be used by other applications
Self-contained and self-describing
Слайд 20Confidential
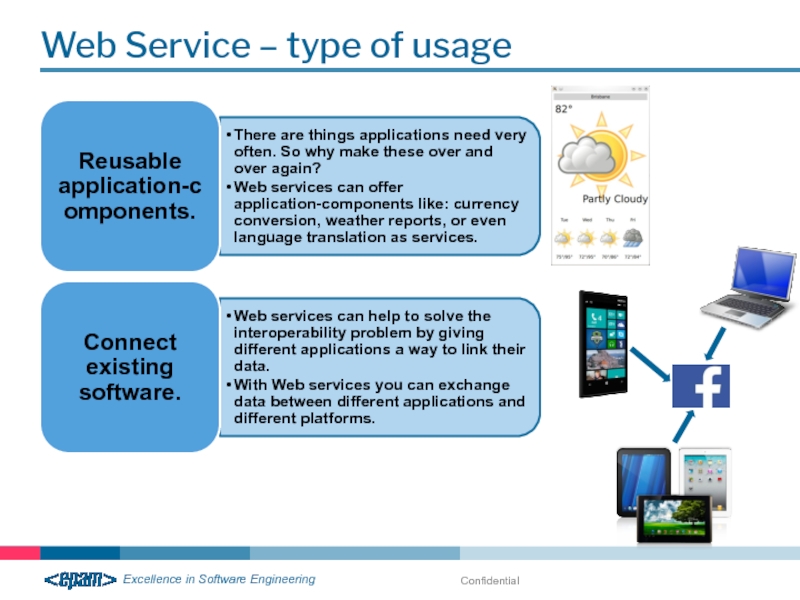
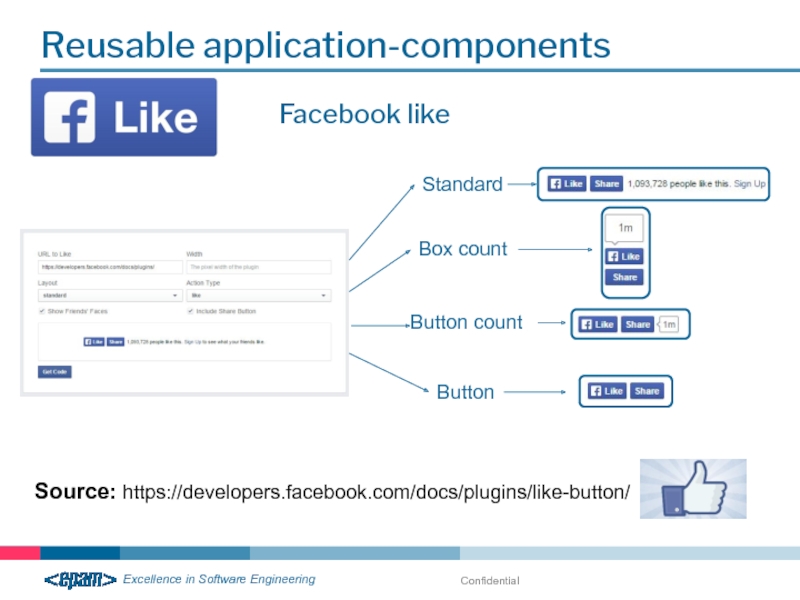
Reusable application-components
Source: https://developers.facebook.com/docs/plugins/like-button/
Facebook like
Standard
Box count
Button count
Button
Слайд 26Confidential
How does software communicate?
Client
Server
Java
…
.NET
…
Desktop
…
Mobile
…
Request
Response
Слайд 29Confidential
Widely Well-known words
Web Application
Usually a collection of dynamic
Usually restricted to the intranet
Can be implemented as desktop application
Information accessible using front end user interfaces
Accessed by authorised users only
Web Site
Collection of static and dynamic web pages
Available on the internet, or an organization's intranet
Cannot be implemented as desktop application
Information accessible using front end user interfaces
Accessed by anybody
Слайд 30Confidential
Widely Well-known words
Web Server
Software designed to serve web pages/web
services. Examples are IIS, Apache, etc.
Web Service
Application run by a web server, performing tasks and
returning structured data to a calling program, rather
than html for a browser.
Only “provides” information; does not “present”
information
Publicly available and standardized for use by all
programmers
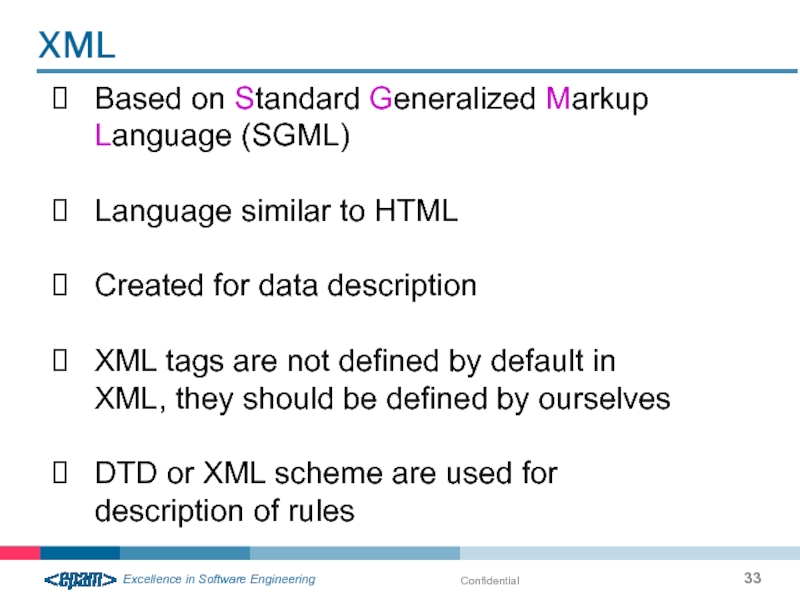
Слайд 33Confidential
Based on Standard Generalized Markup Language (SGML)
Language similar to HTML
Created for
XML tags are not defined by default in XML, they should be defined by ourselves
DTD or XML scheme are used for description of rules
XML
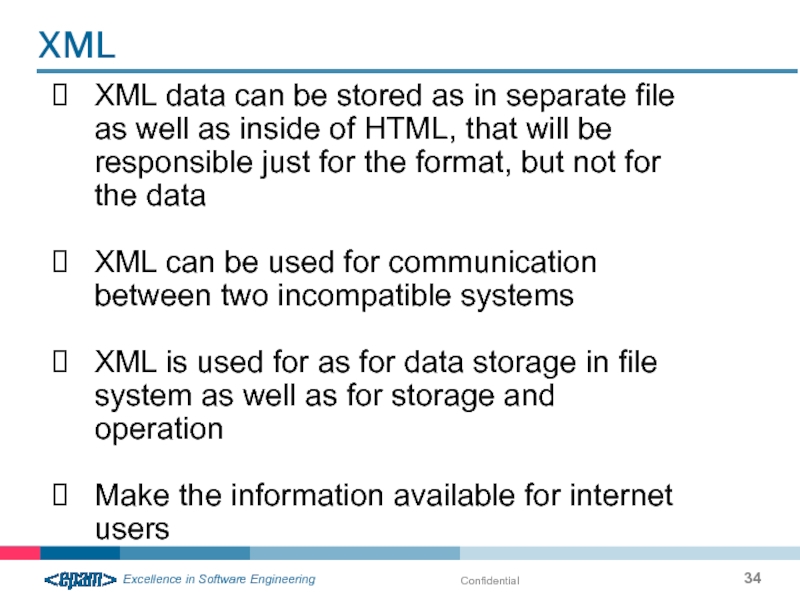
Слайд 34Confidential
XML data can be stored as in separate file as well
XML can be used for communication between two incompatible systems
XML is used for as for data storage in file system as well as for storage and operation
Make the information available for internet users
XML
Слайд 35Confidential
Give the life for derived from the XML languages like WAP
For communication between client and server in Web applications (Ajax)
XML
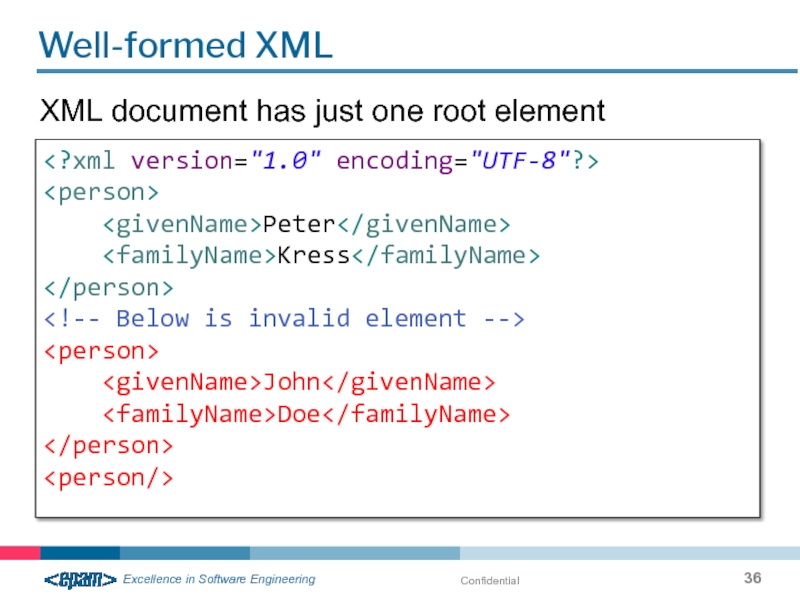
Слайд 36Confidential
Well-formed XML
Peter
Kress
XML document has just one root element
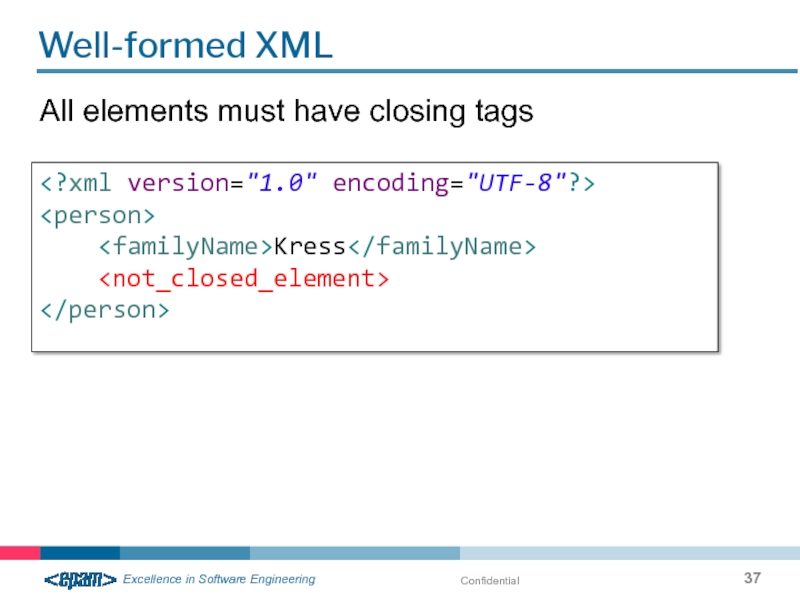
Слайд 38Confidential
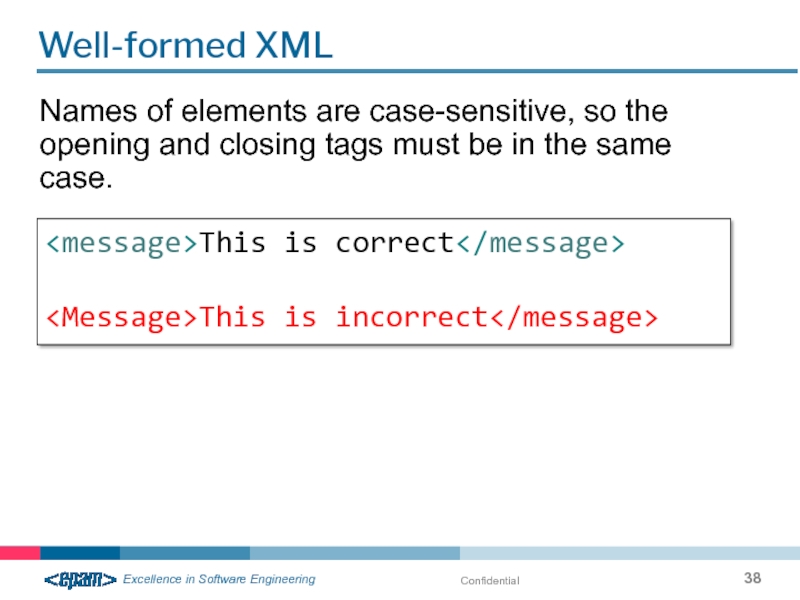
Well-formed XML
Names of elements are case-sensitive, so the opening and closing
Слайд 39Confidential
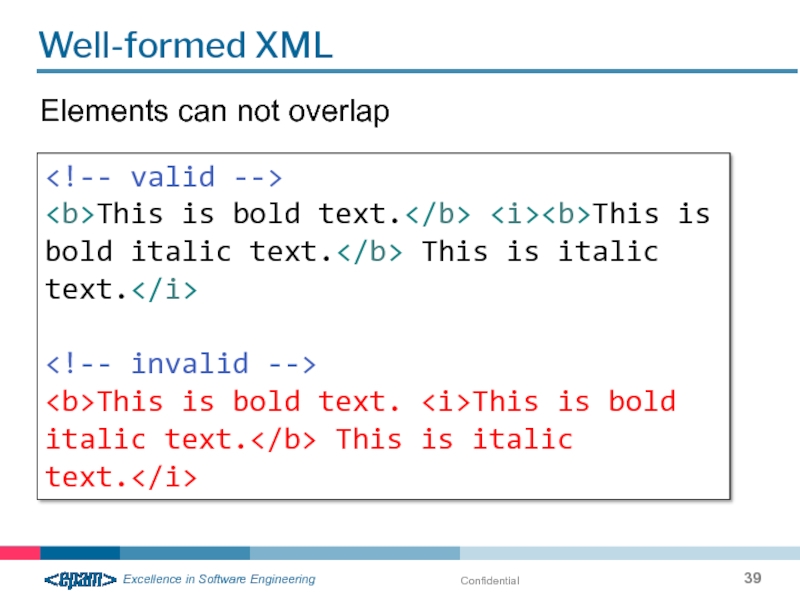
Well-formed XML
Elements can not overlap
This is bold text. This
This is bold text. This is bold italic text. This is italic text.
Слайд 40Confidential
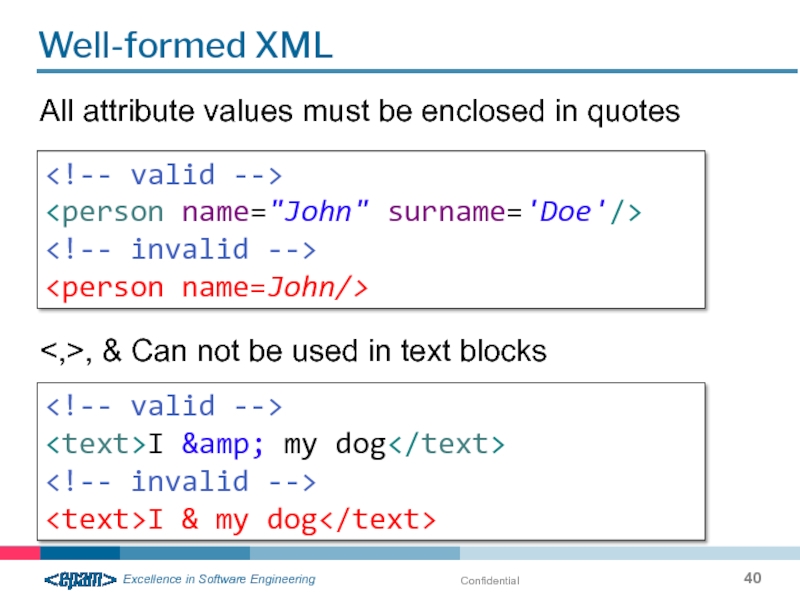
Well-formed XML
All attribute values must be enclosed in quotes
<,>, & Can not be used in text blocks
Слайд 41Confidential
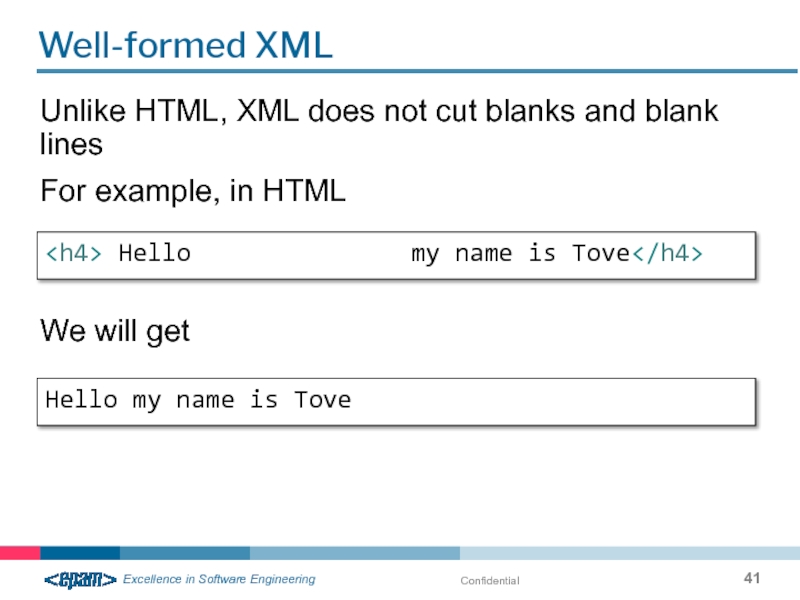
Well-formed XML
Unlike HTML, XML does not cut blanks and blank lines
Hello my name is Tove
For example, in HTML
We will get
Слайд 42Confidential
XML and HTML. Semantics
The values of the elements defined in the
Semantics and structure of elements in XML can be different
There are several approaches to describe the structure of XML (Schema and DTD)
XSLT can be used to effectively transform the XML document in any format: HTML, Plain text, XML, JavaScript, and others.
Слайд 43Confidential
Pros of XML format
Creation of own named structures for storage of
Task of analysis (parsing) XML is well-formalized and there are many implementations
XML uses Unicode, that is simplifies internationalization
Checking the document structure and data types is a standard operation
XML - is a text format, easy to read and debug
Tools for work with XML are available on all platforms
XML allows you to use the infrastructure, created for HTML, including HTTP and some browsers
Слайд 44Confidential
Cons of XML format
XML documents are usually less concise than comparable
Transferring of XML creates more traffic or more CPU overhead when using compression
XML parsing can be slower and more demanding of memory than parsing optimized binary documents
Слайд 45Confidential
Component parts of XML document
Prologue
Elements
Processing instructions
Comments
Attributes
Pointers
Text blocks
CDATA blocks
Namespaces
Слайд 46Confidential
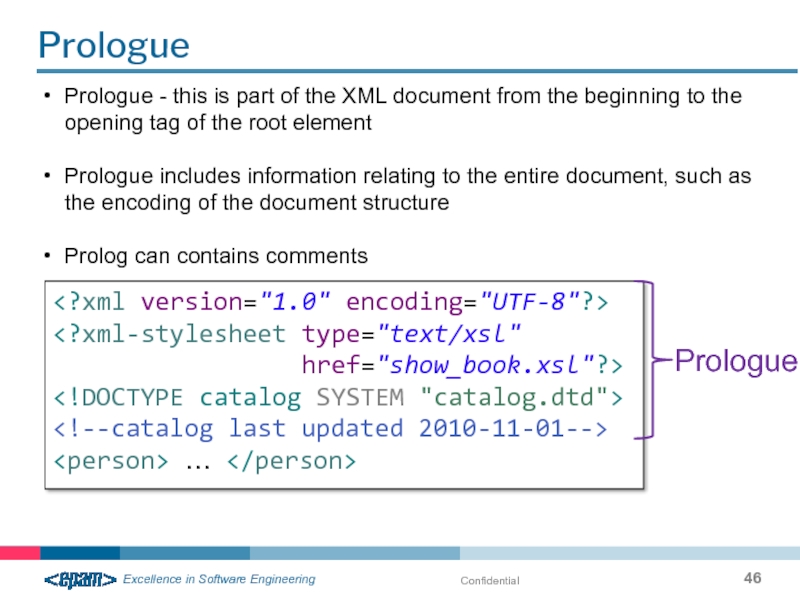
Prologue
Prologue
Prologue - this is part of the XML document from the beginning to the opening tag of the root element
Prologue includes information relating to the entire document, such as the encoding of the document structure
Prolog can contains comments
Слайд 47Confidential
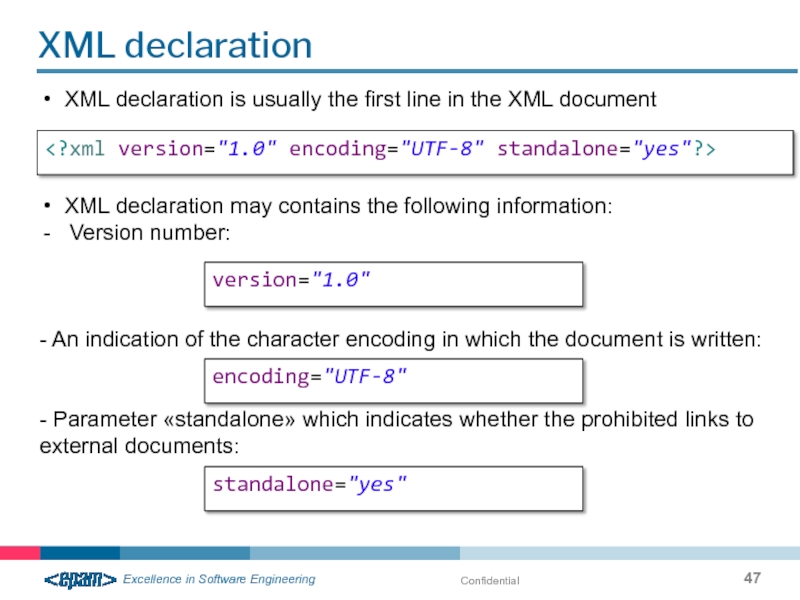
XML declaration
version="1.0"
encoding="UTF-8"
standalone="yes"
XML declaration is usually the first line
XML declaration may contains the following information:
Version number:
- An indication of the character encoding in which the document is written: - Parameter «standalone» which indicates whether the prohibited links to external documents:
Слайд 51Confidential
Tags
att2Name="att2Value" ... />
Tags define the boundaries of the element
Opening tags indicate the start of an element:
End tags mark the end of an element. They haven’t attributes:
Empty tags are used to create elements without text content. They may include attributes:
It is believed that the element includes an opening and closing tags and everything in between
Слайд 53Confidential
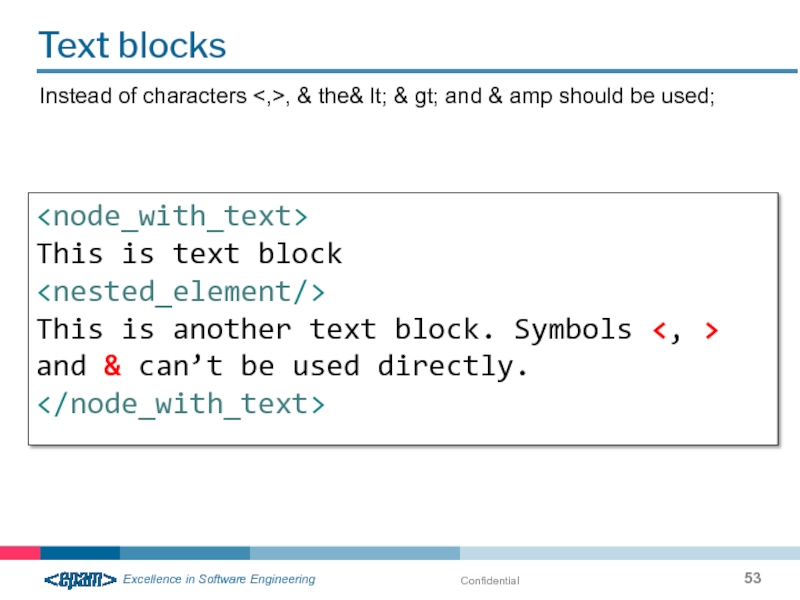
Text blocks
Instead of characters , & the& lt; & gt; and
This is text block
This is another text block. Symbols <, > and & can’t be used directly.
Слайд 54Confidential
Pointers to characters and entities
Pointers are used when it is impossible
Pointer to start with an ampersand & and end with a semicolon (;)
Pointers to characters provide an opportunity to include in the document Unicode characters using the number
& # value; - The syntax for the decimal indicator
& # xvalue; - The syntax for hexadecimal pointers.
Слайд 56Confidential
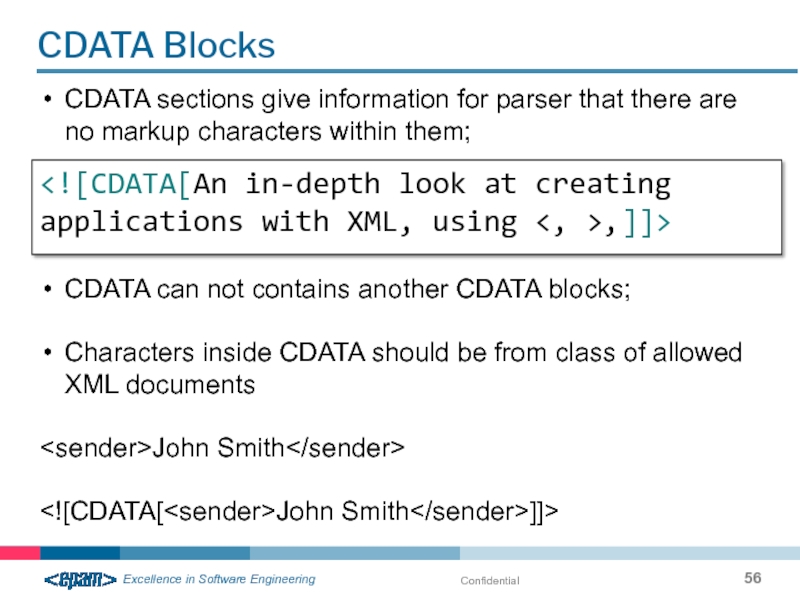
CDATA Blocks
CDATA sections give information for parser that there are no
CDATA can not contains another CDATA blocks;
Characters inside CDATA should be from class of allowed XML documents
John Smith]]>
,]]>
Слайд 58Confidential
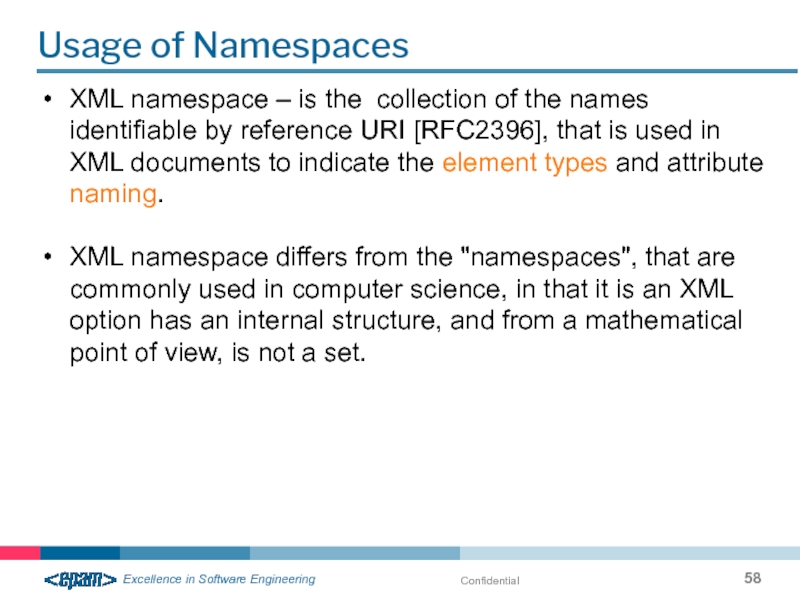
Usage of Namespaces
XML namespace – is the collection of the names
XML namespace differs from the "namespaces", that are commonly used in computer science, in that it is an XML option has an internal structure, and from a mathematical point of view, is not a set.
Слайд 59Confidential
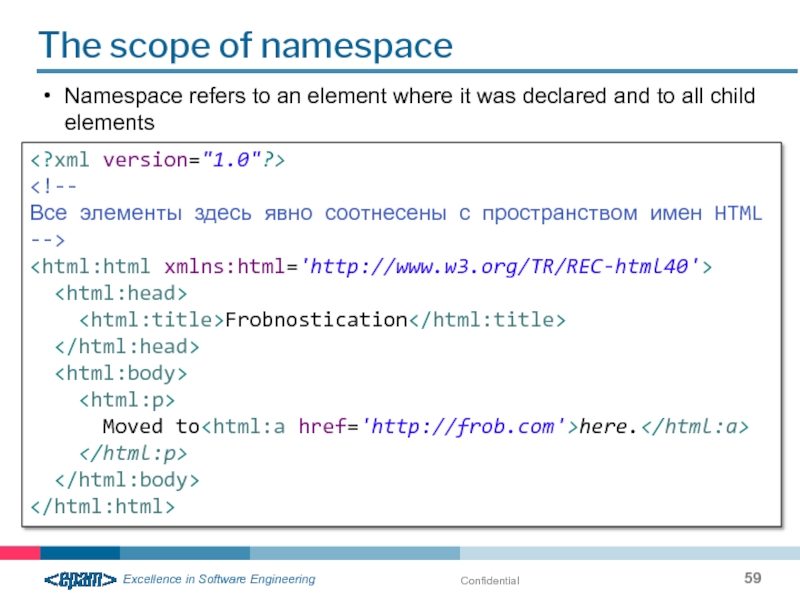
The scope of namespace
Namespace refers to an element where it was
Moved to
Слайд 61Confidential
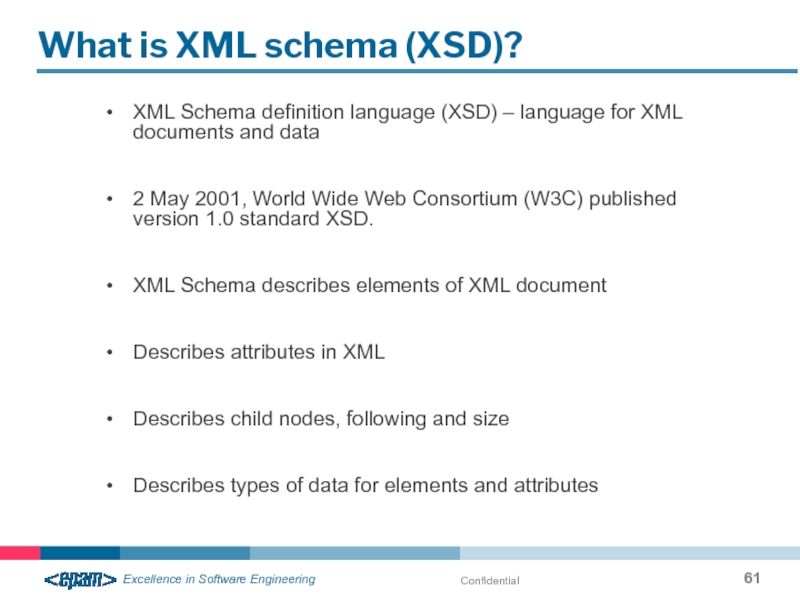
What is XML schema (XSD)?
XML Schema definition language (XSD) –
2 May 2001, World Wide Web Consortium (W3C) published version 1.0 standard XSD.
XML Schema describes elements of XML document
Describes attributes in XML
Describes child nodes, following and size
Describes types of data for elements and attributes
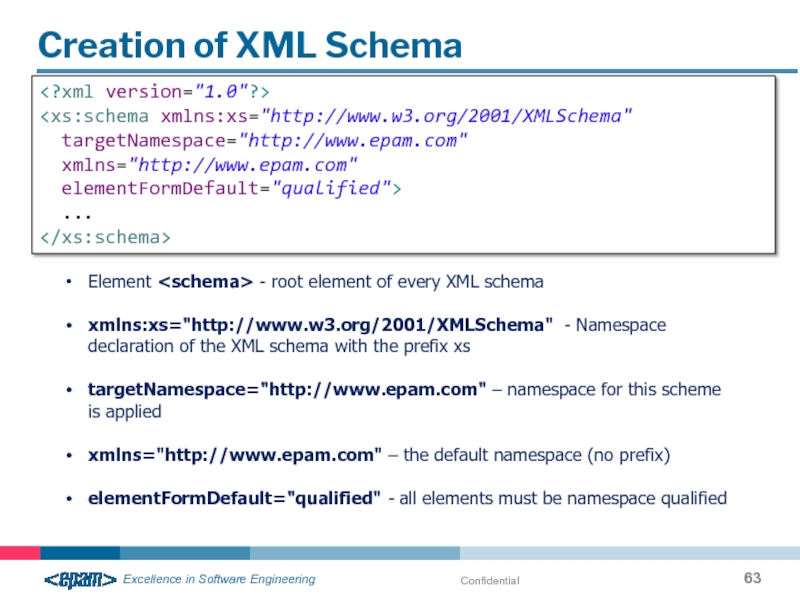
Слайд 63Confidential
Creation of XML Schema
...
Element
xmlns:xs="http://www.w3.org/2001/XMLSchema" - Namespace declaration of the XML schema with the prefix xs
targetNamespace="http://www.epam.com" – namespace for this scheme is applied
xmlns="http://www.epam.com" – the default namespace (no prefix)
elementFormDefault="qualified" - all elements must be namespace qualified
Слайд 64Confidential
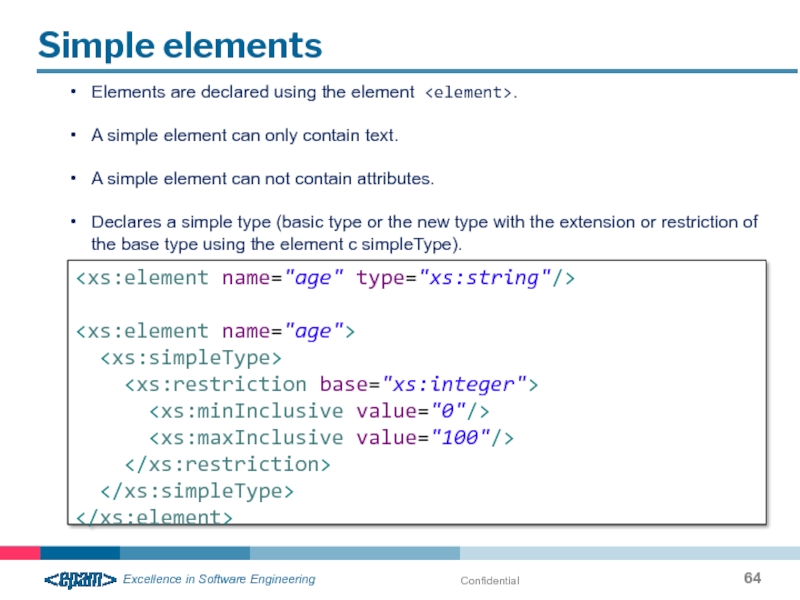
Simple elements
Elements are declared using the element .
A simple element can
A simple element can not contain attributes.
Declares a simple type (basic type or the new type with the extension or restriction of the base type using the element c simpleType).
Слайд 65Confidential
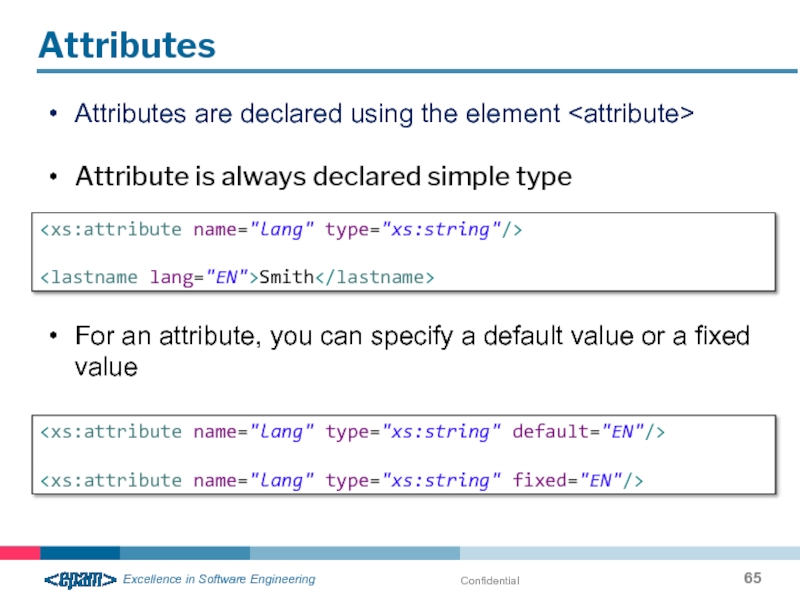
Attributes
Attributes are declared using the element
Attribute is always declared simple
For an attribute, you can specify a default value or a fixed value
Слайд 66Confidential
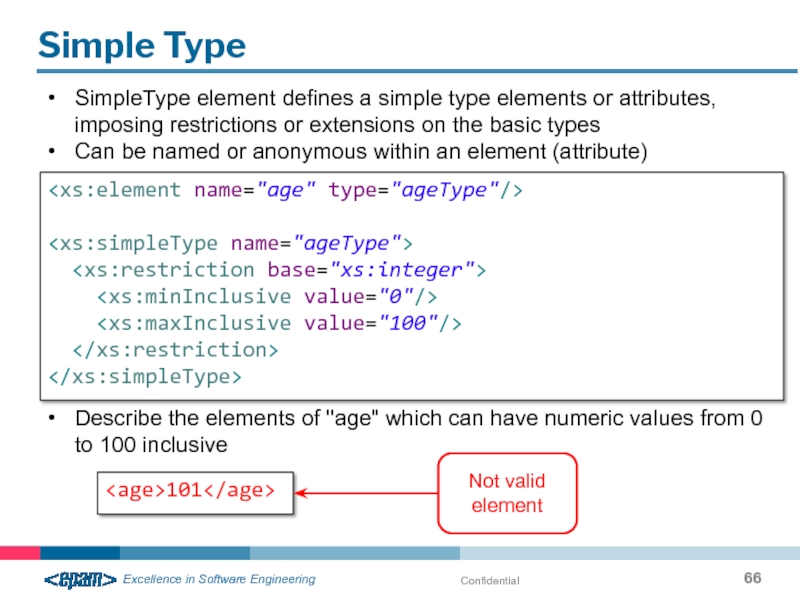
Simple Type
SimpleType element defines a simple type elements or attributes, imposing
Can be named or anonymous within an element (attribute)
Describe the elements of "age" which can have numeric values from 0 to 100 inclusive
Not valid element
Слайд 67Confidential
Complex Type
Composite type describes the element that contains other elements and
The composite type is described by an element complexType
Can be named or anonymous inside the cell
Слайд 68Confidential
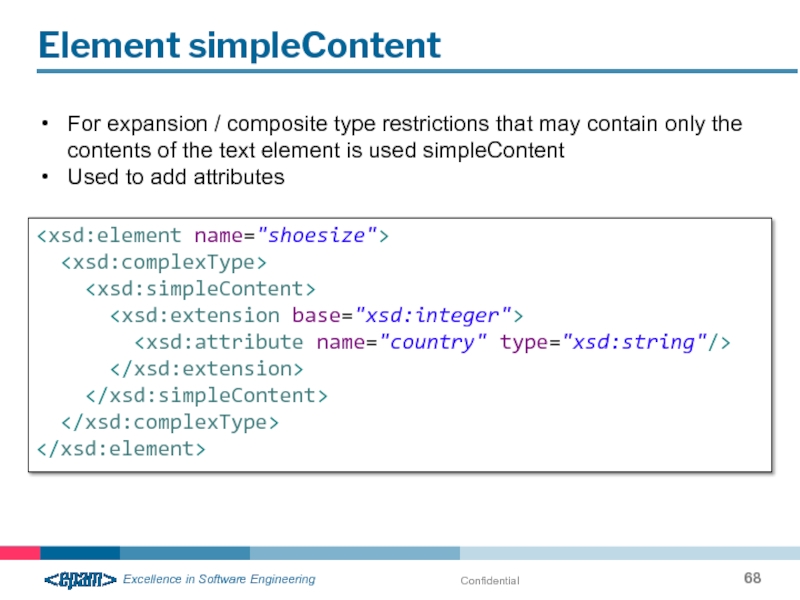
Element simpleContent
For expansion / composite type restrictions that may contain only
Used to add attributes
Слайд 69Confidential
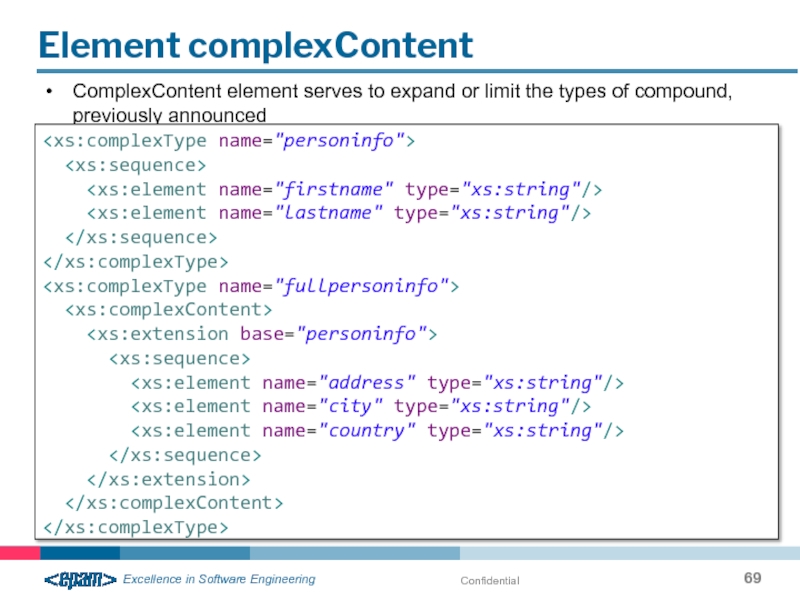
Element complexContent
ComplexContent element serves to expand or limit the types of
Слайд 70Confidential
Types
Types of elements / attributes can be
Local and anonymous (in the
Global and named (directly in the element schema)
Слайд 71Confidential
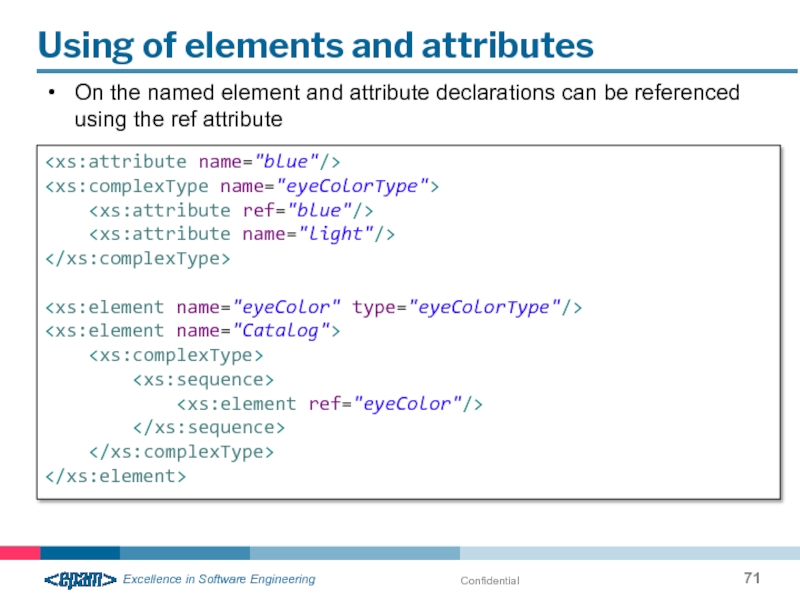
Using of elements and attributes
On the named element and attribute declarations
Слайд 72Confidential
Base types
XML schema contains 44 base types. General:
string
decimal
integer
boolean
date
time
Слайд 73Confidential
Restrictions
Restrictions used for control of possible values of elements and XML
Слайд 75Confidential
Template restriction
Restriction in one lower case letter
Restriction in three upper case letters
Слайд 77Confidential
White spaces restriction
Restriction whiteSpace can have 3 values:
preserve – leave all
replace – replace all such symbols with one
collapse – delete all white spaces before and after
Слайд 78Confidential
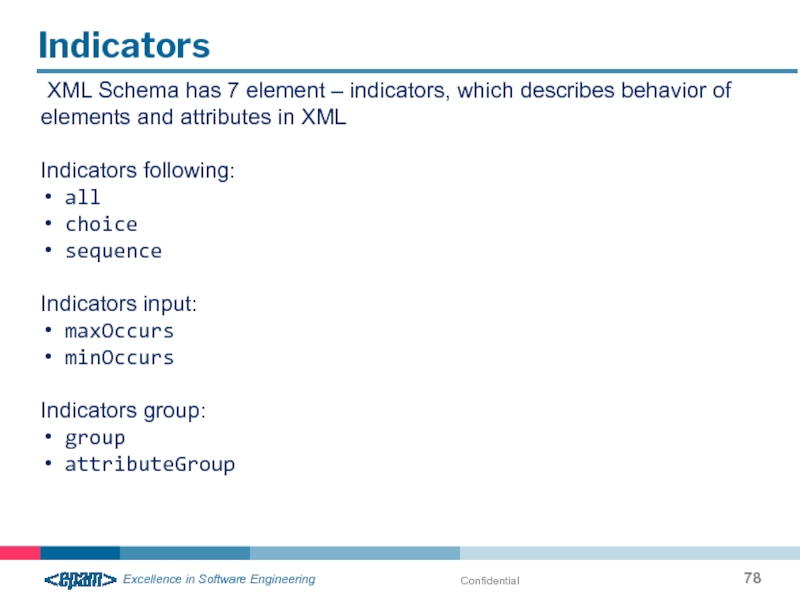
Indicators
XML Schema has 7 element – indicators, which describes behavior
Indicators following:
all
choice
sequence
Indicators input:
maxOccurs
minOccurs
Indicators group:
group
attributeGroup
Слайд 81Confidential
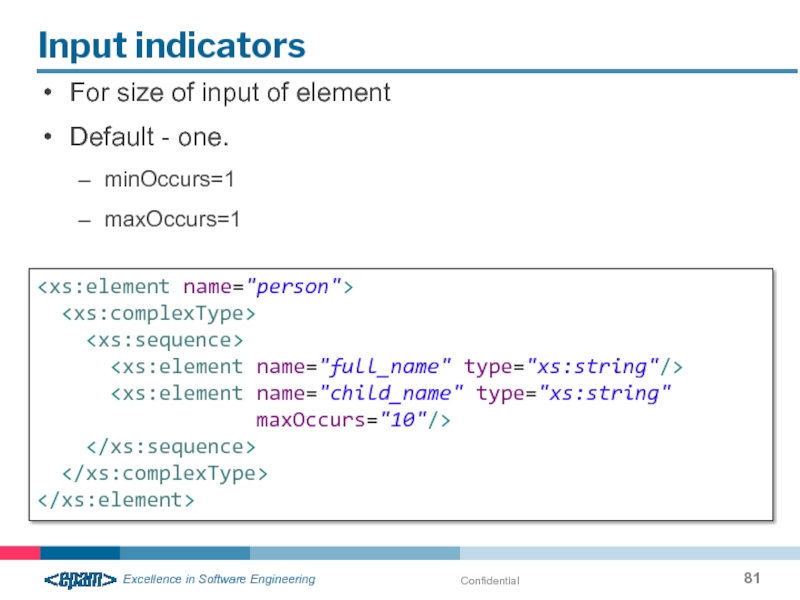
Input indicators
For size of input of element
Default - one.
minOccurs=1
maxOccurs=1
Слайд 82Confidential
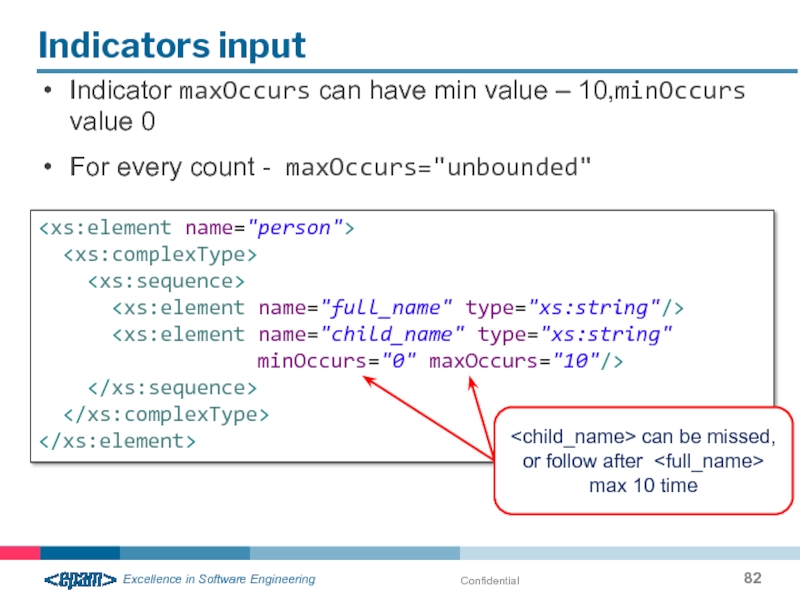
Indicators input
Indicator maxOccurs can have min value – 10,minOccurs value 0
For
Слайд 84Confidential
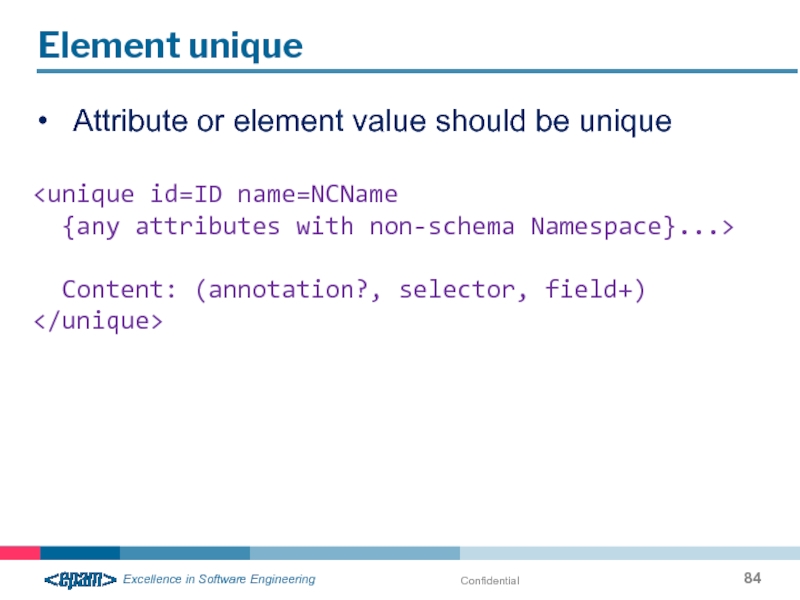
Element unique
Attribute or element value should be unique
Content: (annotation?, selector, field+)
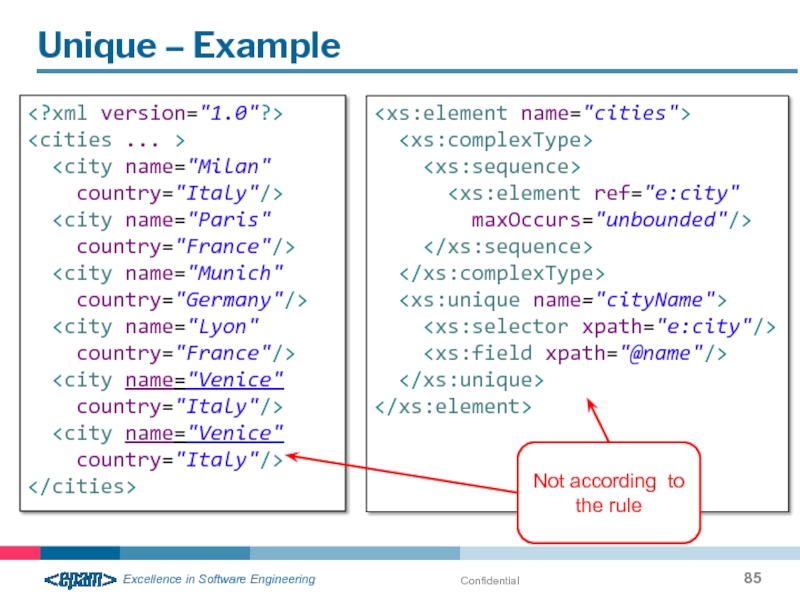
Слайд 85Confidential
Unique – Example
country="France"/>
Not according to the rule
Слайд 86Confidential
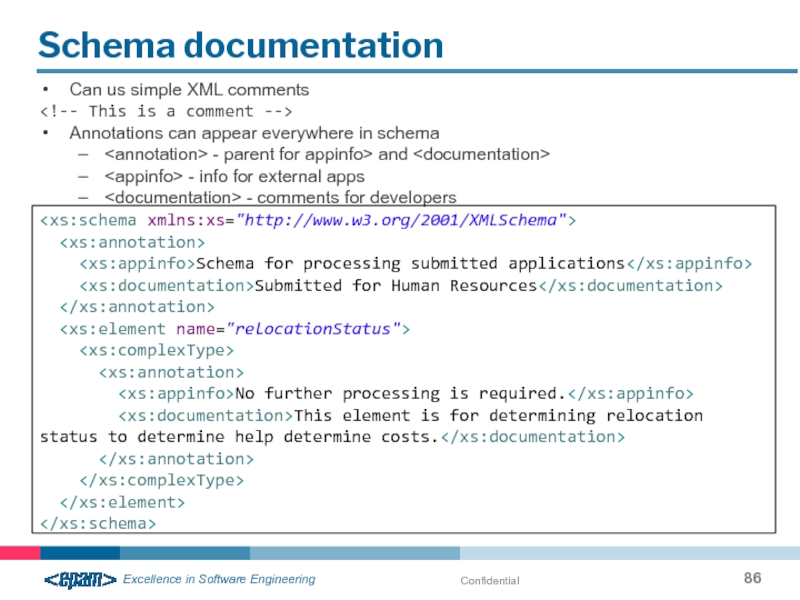
Schema documentation
Can us simple XML comments
Annotations
Слайд 87Confidential
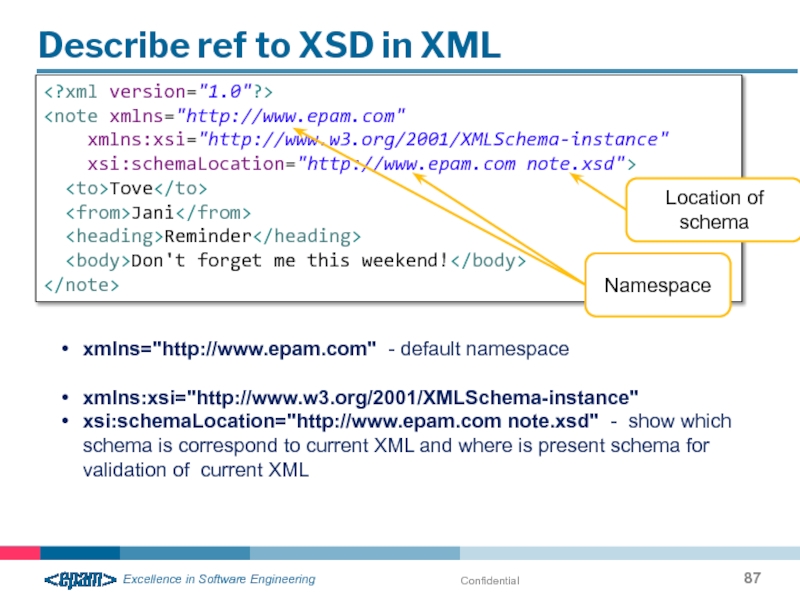
Describe ref to XSD in XML
Don't forget me this weekend!
Namespace
Location of schema
xmlns="http://www.epam.com" - default namespace
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://www.epam.com note.xsd" - show which schema is correspond to current XML and where is present schema for validation of current XML
Слайд 88Confidential
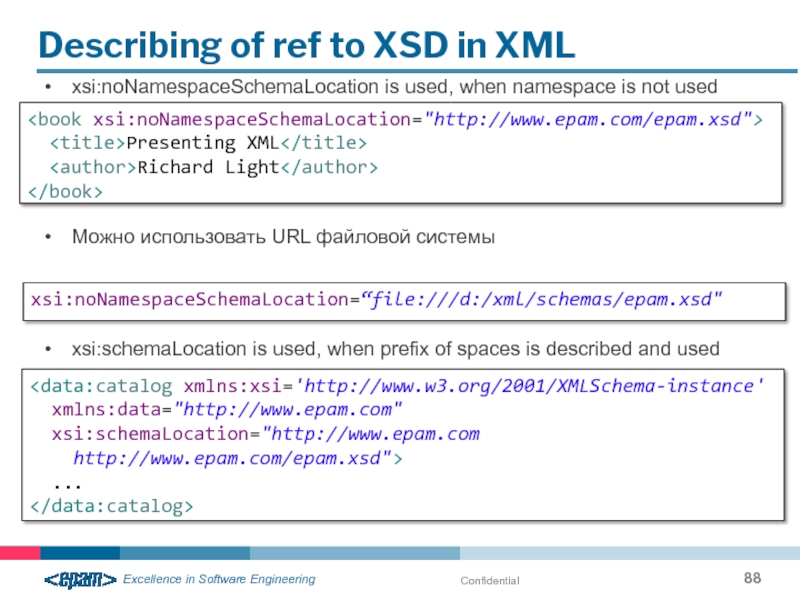
Describing of ref to XSD in XML
xsi:noNamespaceSchemaLocation is used, when namespace
Можно использовать URL файловой системы
xsi:schemaLocation is used, when prefix of spaces is described and used
xsi:noNamespaceSchemaLocation=“file:///d:/xml/schemas/epam.xsd"
xsi:schemaLocation="http://www.epam.com
http://www.epam.com/epam.xsd">
...
Слайд 90Confidential
What was learnt for today?
Web application / Web site /
Web service
XML and how to create XML
XSD and how to create XSD